使用ID²-KM将设备接入阿里云物联网平台
本文介绍了设备如何通过更安全的身份认证方式(ID²)连接到阿里云物联网平台,并建立安全传输通道。
1. 术语
Soft-KM(Key Management)密钥管理,由阿里提供的软件安全沙箱,基于软件加固和虚拟化技术提供对密钥(IoT ID²)的安全保护。
OSA(Operation System Abstractor Layer)操作系统抽象层,定义内存申请和释放、日志打印、系统时间、网络通信等接口,非遵循POSIX标准的OS,需重新适配这些接口。
HAL(Hardware Abstractor Layer)硬件抽象层,根据设备硬件特性,完成对加解密算法、设备唯一ID、密钥管理和数据安全存储的接口适配。
ID² OTP(One-Time Provisioning)一次性烧录,也称ID²空发,指设备在第一次联网时,通过网络请求,下发ID²数据烧录到设备中。
TLS(Transport Layer Security)安全传输层协议, 用于两个通信实体之间,保护通信数据的私密性和完整性。
IoT(Internet of things)物联网,基于互联网实现万物互联。
阿里云物联网平台(Link Platform)阿里云物联网平台,提供物联网的设备管理。
2. ID²产品架构
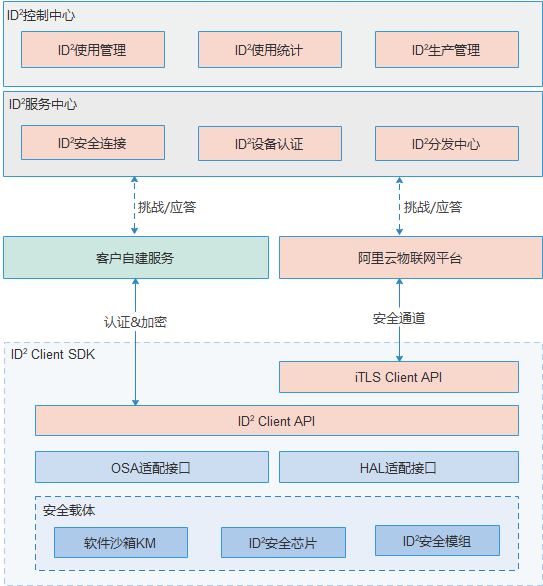
ID²控制中心:
ID²的Web控制台,提供对ID²产线灌装、ID²产品和配额申请、以及ID²使用统计的管理。
ID²服务中心:
ID²在云端的应用,提供ID²的各种安全能力,包括ID²密钥安全分发、设备认证、基于ID²的安全连接协议等;同时,提供各种能力的云端接口,支持业务平台的二次开发,支持不同的安全业务需求和场景。
ID² Client SDK:
ID²在设备端的功能组件和软件开发框架,可支持不同操作系统和不同硬件,为IoT设备提供基于ID²的端到端的设备认证、数据加解密等各种安全能力。
3. ID²接入流程
3.1 概述:
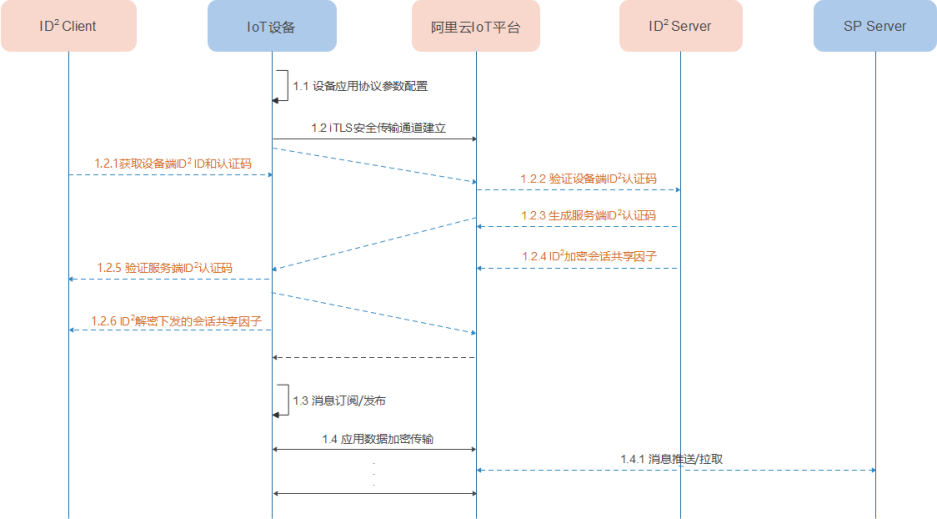
阿里云物联网平台接入的方式,ID²已默认同物联网平台打通,因此不需要进行服务端对接。
设备建连的过程,IoT设备通过物联网设备端Linkkit SDK调用ID²-iTLS,进行设备认证和会话密钥协商,最后建立数据安全传输通道。
设备建连成功后,IoT设备和物联网平台,通过安全通道进行应用数据的安全传输。
ID²对接步骤如下:

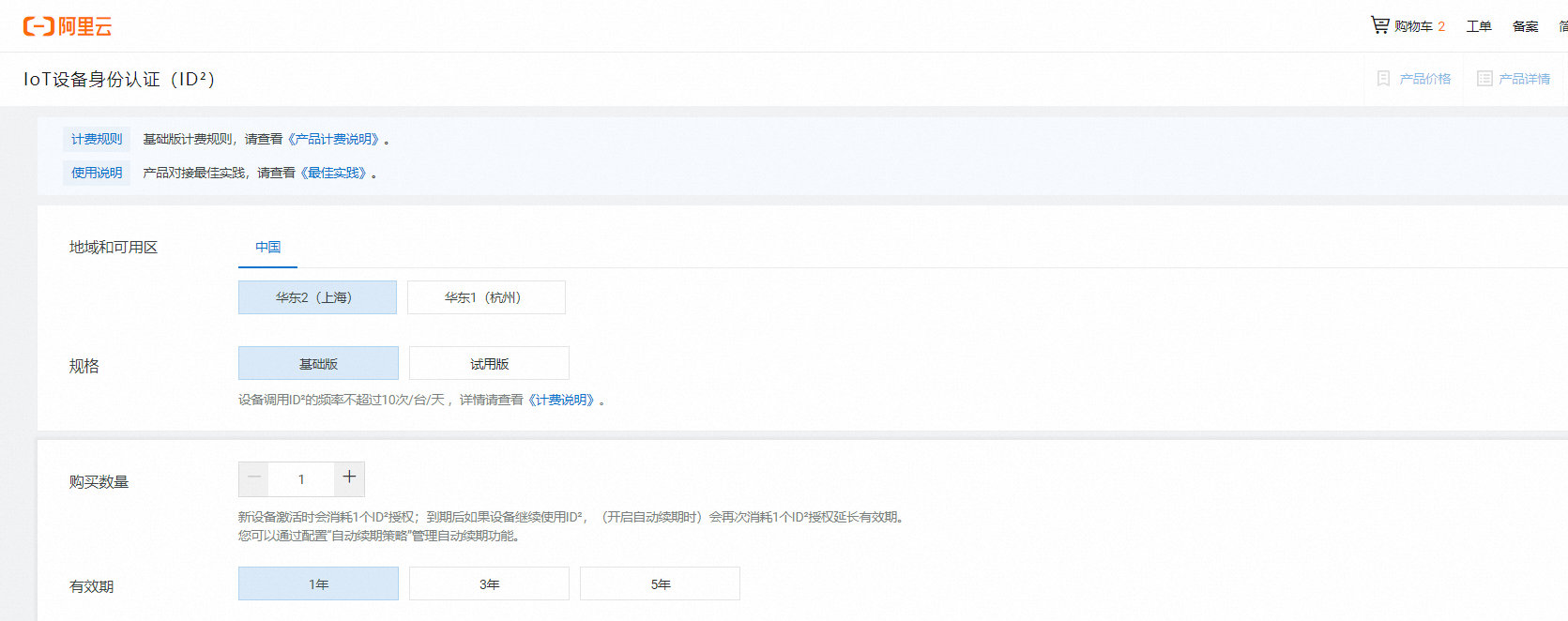
3.2 购买ID²授权:
点击购买链接 - 购买ID²认证授权。
选择地域和可用区、规格、购买数量和有效期:
3.3 创建产品:
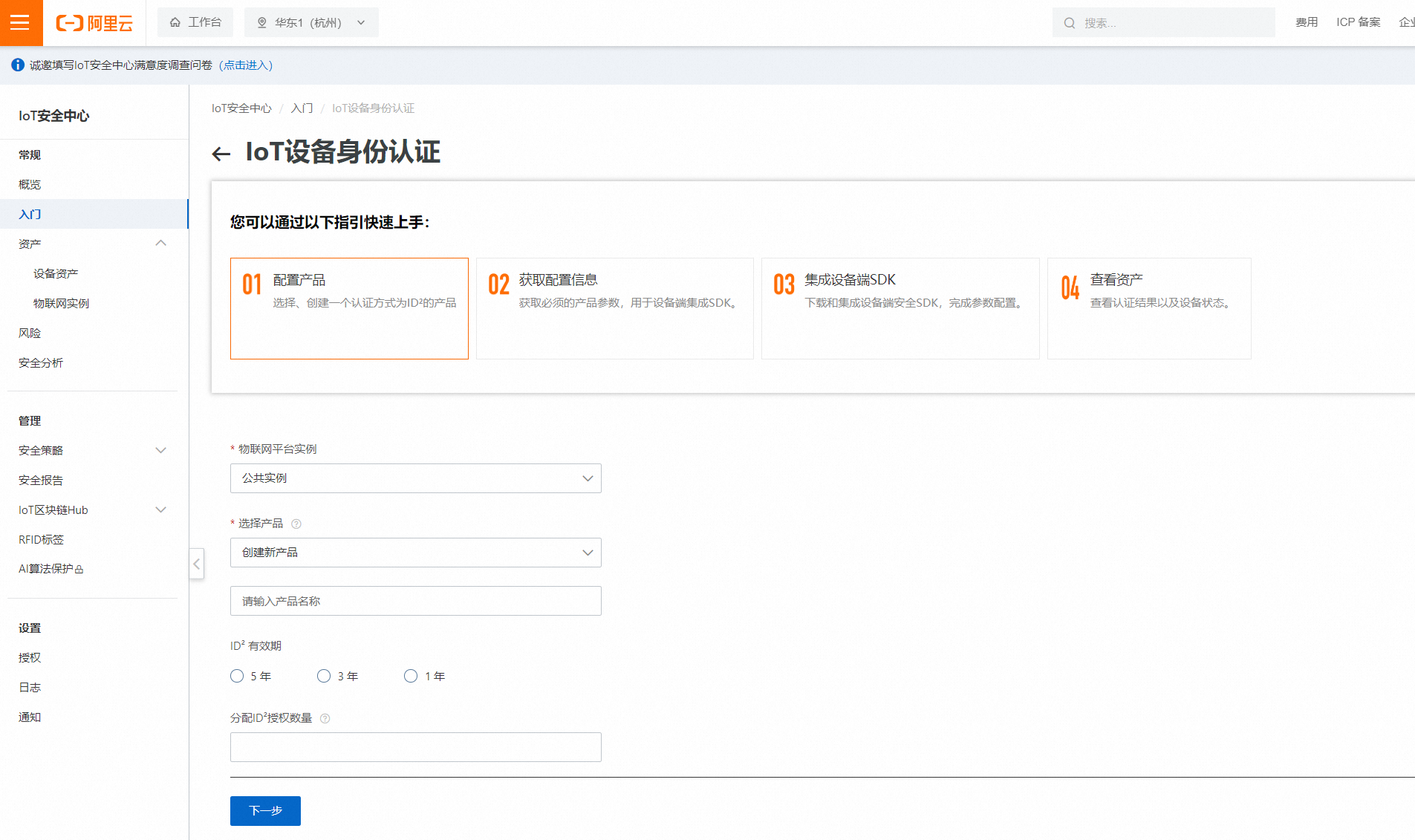
登录IoT安全产品控制台,在左侧导航栏,选择入门 > IoT设备身份认证,单击与阿里云物联网平台组合使用卡片的开始接入按钮
在配置产品页面创建新产品&分配ID²授权,然后单击下一步按钮。
选择产品:请选择创建新产品,并输入产品名称。
ID²有效期:请选择1年、3年、或5年。
分配ID²授权数量:填写实际的设备数量,不超过账号下可分配ID²的数量。
在查看配置信息页面,记录下实例ID、ProductKey、ProductSecret。
实例ID:阿里云物联网平台的实例标识。企业实例ID是字符串,公共实例ID是符号“-”。
ProductKey:设备所属产品的ProductKey。
ProductSecret:由IoT设备身份认证颁发的产品密钥,与 ProductKey 成对出现。
3.4 选择设备认证算法:
IoT设备身份认证支持国际算法(AES-128、AES-192、AES-256)和国密算法(SM1、SM2、SM4-128),能满足企业不同安全等级的需求。
说明
国密算法SM1需要配合ID²安全芯片使用,SM2用于业务数据完整性校验和加密。
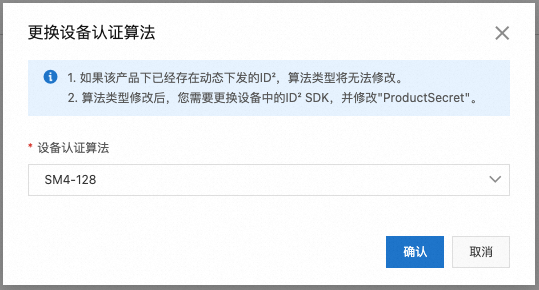
创建的ID²产品默认选择的设备认证算法是AES-128;如需选择其他设备认证算法,请按如下步骤操作:
在查看配置信息页面,单击设备认证算法后的更换按钮,查看支持的密钥类型(如SM4-128),并确认。
在查看配置信息页面,记录下实例ID、ProductKey、ProductSecret。
实例ID:阿里云物联网平台的实例标识。企业实例ID是字符串,公共实例ID是符号“-”。
ProductKey:设备所属产品的ProductKey。
ProductSecret:由IoT设备身份认证颁发的产品密钥,与 ProductKey 成对出现。
3.5 集成设备端SDK:
3.5.1 ID²设备端SDK框架:
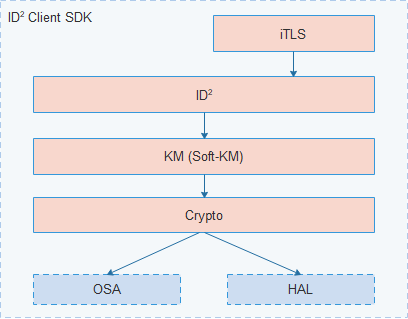
iTLS:轻量的安全连接协议TLS,基于ID²完成TLS的握手认证和密钥协议,提供应用数据的加密传输。
ID²:IoT设备认证和数据加密的对外接口,上层应用/协议基于此接口进行开发。
KM:密钥管理模块,支持不同形式的载体:
Soft-KM:软件沙箱,基于软件加固和虚拟化技术提供对ID²密钥的安全保护。
SE(Secure Element):安全芯片,基于物理防护机制,提供对ID²密钥的安全保护,通过AT指令对设备提供ID²的运算指令。
Crypto:提供统一的加解密算法接口。
OSA:操作系统适配接口,厂商需根据使用的OS,重新进行接口适配。
HAL:硬件适配接口,提供算法库和Soft-KM的适配接口,厂商需根据选择的硬件平台,重新进行接口适配。
3.5.2 下载设备端SDK:
登录IoT安全产品控制台,在左侧导航栏,选择文档与工具,在IoT设备身份认证设备端SDK中单击立即下载右侧的复制按钮获取最新的下载地址,执行命令获取设备端SDK。
wget https://id2-schip-online.oss-cn-shanghai.aliyuncs.com/static_resources/id2_client_sdk/ID2_Client_SDK.tar执行命令tar -xvf ID2_Client_SDK.tar完成解压,执行命令cd <解压SDK后的目录>。设备端SDK的目录说明见表格内容:
目录/文件 | 说明 |
demos | ID²设备端的示例代码:
|
external | 用于存放外部的组件:
|
include | ID²的头文件目录 |
libs | ID²的静态库 |
make.rules | 编译规则文件,可配置编译工具链和编译参数 |
make.settings | 编译配置文件,可配置ID²的密钥类型(如AES、SM4) |
makefile | 编译脚本 |
src | ID²的源码目录 |
tests | ID²的测试用例,包括HAL和ID²的测试。 |
3.5.3 集成设备端SDK:
设备硬件及系统层集成, 详情请参考ID²安全Agent适配接口:
OSA接口适配:实现src/osa/ls_osa.c中的接口,参考目录下__DEMO__的实现。
HAL接口适配:实现src/hal/km/demo/ls_hal_km.c中的接口,通过hal_test测试用例验证(成功日志: “HAL KM Test Pass”),参考目录下__DEMO__的实现。
2. 设备连接通道层集成
本节说明ID²和不同Link SDK(ID² SDK中默认提供的,以及用户自定义构建的)的集成方式:
使用默认的Link SDK v4.x,请跳过此步骤。
使用单独构建的Link SDK时,认证方式必须选择ID²;拷贝LinkSDK到external/mqtt/lk_4.x中,并执行命令cd external/mqtt/lk_4.x & ./ls_config_LinkSDK.sh完成Link SDK的配置。
返回设备端SDK根目录。
3. 设备应用层集成
设备应用调用Link SDK的实现请参考使用示例。需要注意:
设备接入域名(mqtt_host)、MQTT服务器端口的配置方式:
设备接入域名:${YourProductKey}.itls.cn-shanghai.aliyuncs.com,其中${YourProductKey}为IoT设备身份认证产品的ProductKey
MQTT服务器端口:1883在配置连接参数中追加配置:
设备接入域名:${YourProductKey}.itls.cn-shanghai.aliyuncs.com,其中${YourProductKey}为IoT设备身份认证产品的ProductKey
MQTT服务器端口:1883LinkSDK集成ID² 的示例代码,请参考demos/mqtt/lk_4.x/mqtt_id2_demo.c
4. 设备端SDK的编译
在ID² SDK的根目录,执行命令vi ./make.settings打开文件, 修改CONFIG_LS_ID2_KEY_TYPE的值
同ID²产品选择的认证算法保持相同

执行命令 vi demos/mqtt/lk_4.x/mqtt_id2_demo.c打开文件,配置如下参数:
ProductKey:ID²产品的ProductKey。
ProductSecret:ID²产品的ProductSecret。
DeviceName:自定义,同一个产品下唯一。
LP_Instance_ID:填写在ID²产品详情中获得的企业实例ID字符串;如果是公共实例,填写NULL

执行命令“make clean & make plat=xxx”进行编译
Linux x86_64默认使用系统中的GCC作为编译工具,且默认指定“plat=x86_64”参数
如要编译其他架构,如armhf,在make.rules中配置编译工具,运行编译命令“make clean & make plat=armhf”
3.6 安全接入
在完成设备端集成的基础上,运行设备应用, 或者演示示例接入阿里云物联网平台
使用演示示例接入物联网平台:
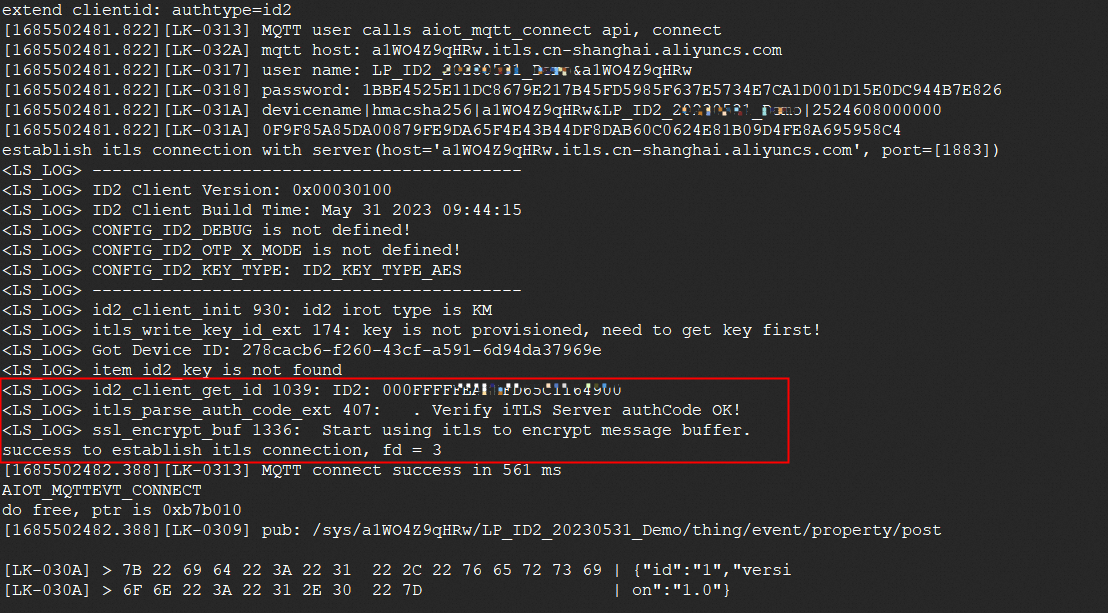
烧录固件mqtt_id2_demo到设备中
运行固件mqtt_id2_demo,查看设备端打印的日志
在日志中,可以看到此设备上的ID² ID(“ 000FF...”)
基于ID²进行设备和LP平台之间的双向认证(“Verify iTLS Server AuthCode OK”),并建立设备和LP平台的TLS安全传输通道(ID²-iTLS);MQTT消息开始基于TLS通道进行加密传输(“Start to use itls to encrypt message buffer”)
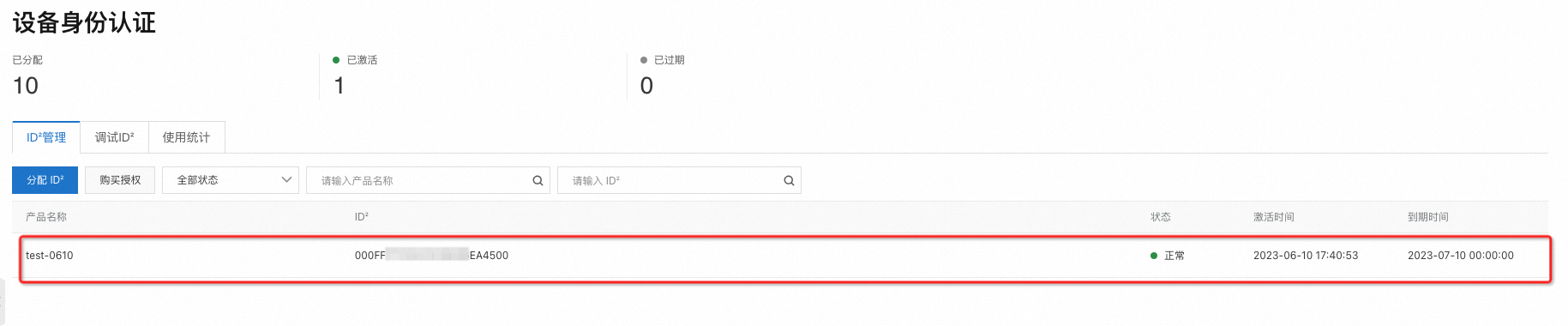
查看到期时间:
登录IoT设备身份认证控制台,在左侧导航栏,选择物联网身份>设备身份认证,查看设备状态为正常,到期时间为免费试用的到期时间。
重要
付费后,每个设备的ID²到期时间单独计算,到期时间 = 首次上线时间+授权有效期。详情请查看计费概述。