容器计算服务 ACS(Container Compute Service)的授权体系包含对基础计算资源的RAM授权和对ACS类型ACK集群侧RBAC授权,不同用户角色在这两个层面都具有不同的权限要求。本文介绍针对企业资源管理人员,Kubernetes集群管理人员,以及集群与应用运维人员、应用开发人员、权限管理人员五类对象的授权最佳实践。
ACS授权体系
ACS的授权体系包含对基础资源层的RAM授权以及对ACS集群层的RBAC授权。ACS授权体系如下图所示。

RAM授权包括对集群的运维操作,因为ACS集群是 ACK 的一种 Serverless K8s 集群类型,对ACS集群的运维操作需要通过ACK OpenAPI执行,所以需要获取ACK产品及其所依赖的阿里云产品的OpenAPI操作权限,主要包括以下操作:
集群:创建、查看、删除。
集群RBAC授权管理。
集群监控、日志、事件。
RBAC授权对应的是运行于ACS集群中Kubernetes应用的运维操作,需要获取ACS集群及其命名空间的操作权限,主要包括对以下Kubernetes对象的增删改查操作:
工作负载:Deployment、StatefulSet、Job、CronJob、Pod、ReplicaSet、HPA等。
网络:Service、Ingress、NetworkPolicy等。
存储:PV、PVC、StorageClass等。
Namespace、ConfigMap、Secrets等。
系统默认授权策略
容器计算服务ACS预置以下系统授权策略,您可以通过给RAM用户或RAM角色授权系统默认授权策略,完成快速授权。
系统默认授权策略授权范围较大,可具有ACK、ACS所有OpenAPI的读或写权限,请谨慎授权。
系统默认授权策略 | 授权策略描述 |
AliyunAccFullAccess | 管理容器计算服务ACS的权限。 |
AliyunAccReadOnlyAccess | 只读访问容器计算服务ACS的权限。 |
AliyunCSFullAccess | 管理容器服务ACK的权限。 重要 可读写操作包括ACS类型在内的所有ACK集群,请谨慎授权。 |
AliyunCSReadOnlyAccess | 只读访问容器服务ACK的权限。 重要 可读操作包括ACS类型在内的所有ACK集群,请谨慎授权。 |
AliyunAccFullAccess授权策略
{
"Statement": [
{
"Effect": "Allow",
"Action": "acc:*",
"Resource": "*"
}
],
"Version": "1"
}AliyunAccReadOnlyAccess授权策略
{
"Version": "1",
"Statement": [
{
"Action": [
"acc:Describe*",
"acc:CheckServiceRole"
],
"Resource": "*",
"Effect": "Allow"
}
]
}AliyunCSFullAccess授权策略
{
"Version": "1",
"Statement": [
{
"Action": "cs:*",
"Resource": "*",
"Effect": "Allow"
},
{
"Action": "ram:PassRole",
"Resource": "*",
"Effect": "Allow",
"Condition": {
"StringEquals": {
"acs:Service": "cs.aliyuncs.com"
}
}
}
]
}AliyunCSReadOnlyAccess授权策略
{
"Version": "1",
"Statement": [
{
"Action": [
"cs:CheckServiceRole",
"cs:Get*",
"cs:List*",
"cs:Describe*"
],
"Resource": "*",
"Effect": "Allow"
}
]
}授权最佳实践
当RAM用户或RAM角色需要进行集群运维和应用运维时,您需要依次对其进行RAM授权和RBAC授权。在进行RBAC授权之前,您需要先进行RAM授权。三种典型场景的授权操作如下:
如果授权对象为集群与集群内应用的运维人员,请参见场景一:授权对象为集群与集群内应用的运维人员。
如果授权对象为集群内应用的开发人员,请参见场景二:授权对象为集群内应用的开发人员。
如果授权对象为集群内应用的权限管理员,请参见场景三:授权对象为集群内应用的权限管理员。
场景一:授权对象为集群与集群内应用的运维人员
授权对象需要管理和运维ACS集群所需的必要权限,同时有ACS集群内应用资源对象的运维需求。因此授权流程包含RAM授权和RBAC授权。
RAM授权
容器服务ACK在RAM侧提供了AliyunCSFullAccess和AliyunCSReadOnlyAccess两个系统策略。
AliyunCSFullAccess包含了容器服务ACK全部OpenAPI的读写访问权限。
AliyunCSReadOnlyAccess包含了容器服务ACK全部OpenAPI的只读访问权限。
重要以上两个系统策略授权操作包括ACS类型在内所有ACK集群的,请谨慎授权。
如果您有细粒度权限控制的需求,可以自定义授权策略。具体操作,请参见为RAM用户或RAM角色授予RAM权限。
此场景下,RAM授权策略示例如下所示。
{ "Statement": [ { "Effect": "Allow", "Action": [ "acc:DescribeCommodityStatus", "acc:CheckServiceRole", "acc:DescribeCloudProducts", "acc:DescribeRegions", "acc:DescribeZones", "acc:GetInstancePrice", "acc:RecommendZones" ], "Resource": "*" }, { "Effect": "Allow", "Action": "bssapi:GetPayAsYouGoPrice", "Resource": "*" }, { "Action": "ecs:DescribePrice", "Effect": "Allow", "Resource": "*" }, { "Action": "ram:GetRole", "Effect": "Allow", "Resource": "*" }, { "Action": [ "cs:CreateCluster", "cs:DescribeAddons", "cs:DescribeUserQuota", "cs:DescribeTasks", "cs:ListClusterAddonInstances" ], "Effect": "Allow", "Resource": "*" }, { "Action": [ "cs:GetClusters", "cs:DescribeClustersV1", "cs:DescribeClusterUserKubeconfig", "cs:DescribeClusterResources", "cs:DescribeUserQuota", "cs:DescribeClusterLogs", "cs:ModifyCluster", "cs:UpgradeCluster", "cs:GetUpgradeStatus", "cs:ResumeUpgradeCluster", "cs:PauseClusterUpgrade", "cs:CancelClusterUpgrade", "cs:InstallClusterAddons", "cs:UpgradeClusterAddons", "cs:DescribeClusterAddonsUpgradeStatus", "cs:UnInstallClusterAddons", "cs:DeleteCluster", "cs:DescribeClusterDetail", "cs:GetClusterAuditProject", "cs:DescribeClusterAddonsVersion", "cs:DescribeClusterTasks", "cs:DescribeClusterEvents", "cs:DescribeEvents", "cs:ListClusterReportSummary", "cs:GetClusterBasicInfo", "cs:ListReportTaskRule", "cs:CreateReportTaskRule", "cs:CheckControlPlaneLogEnable", "cs:CreateClusterCheck" ], "Effect": "Allow", "Resource": "acs:cs:*:*:cluster/<yourclusterID>" }, { "Action": [ "cs:CheckServiceRole", "cs:DescribeKubernetesVersionMetadata" ], "Effect": "Allow", "Resource": "acs:cs:*:*:cluster/*" }, { "Action": [ "log:ListProject" ], "Effect": "Allow", "Resource": "*" }, { "Action": [ "vpc:ListEnhanhcedNatGatewayAvailableZones", "vpc:DescribeEipAddresses", "vpc:DescribeVSwitches" ], "Effect": "Allow", "Resource": "*" } ], "Version": "1" }上面示例中
<yourclusterID>需要替换成实际ACS集群ID。关于容器服务ACK OpenAPI的更多说明,请参见【产品变更】容器服务OpenAPI鉴权优化公告和API概览。
RBAC授权
完成RAM授权后,您还需要为RAM用户或RAM角色授予对应集群的RBAC权限。容器服务ACK在集群层面提供了四种预置角色。
角色
集群内RBAC权限
管理员
对所有命名空间下所有资源有读写权限。
运维人员
对所有命名空间下控制台可见Kubernetes资源有读写权限,对集群节点、存储卷、命名空间、配额有只读权限。
开发人员
对所有命名空间或所选命名空间下控制台可见Kubernetes资源有读写权限。
受限用户
对所有命名空间或所选命名空间下控制台可见Kubernetes资源有只读权限。
在容器计算服务控制台左侧边栏点击授权管理页面,然后在右侧子账号或RAM角色页签选择授权对象,接着点击管理权限。
在弹窗页面中点击+添加权限,配置目标集群和对应命名空间的权限管理为运维人员,最后点击提交授权完成配置。
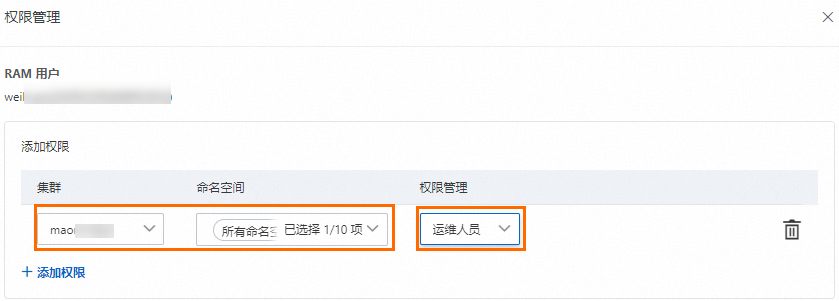
绑定预置角色后,ACS会自动在集群中创建与被授权对象身份对应的ClusterRoleBinding实例。预置运维人员角色的RBAC权限如下所示。
如果您有细粒度的RBAC权限控制需求,可以参考RBAC创建自定义ClusterRole实例,然后在容器计算服务控制台授权管理页面选择自定义角色,再从下拉列表中选择自定义的ClusterRole名称。具体操作,请参见自定义RBAC授权策略。
场景二:授权对象为集群内应用的开发人员
授权对象只需要拥有ACS类型ACK集群内Kubernetes资源对象的操作权限(即RBAC授权),无需云上资源的访问权限。
在进行RBAC授权之前,授权对象需要至少具有目标集群的容器服务只读权限(即RAM授权)。授权Action及Resource “*” 代表授予RAM用户或RAM角色包括ACS类型集群在内所有ACK集群的授权Action操作,所以请尽量不要将Resource置为“*”,除非您充分了解授权范围及影响,有目的性地进行全部授权。
RAM授权
您需要在RAM管理控制台,新增自定义策略,并将该策略授权给目标RAM用户或RAM角色。具体操作,请参见为RAM用户或RAM角色授予RAM权限。自定义策略内容如下所示:
{ "Statement": [ { "Effect": "Allow", "Action": [ "acc:DescribeCommodityStatus", "acc:CheckServiceRole", "acc:DescribeCloudProducts", "acc:DescribeRegions", "acc:DescribeZones", "acc:GetInstancePrice", "acc:RecommendZones" ], "Resource": "*" }, { "Effect": "Allow", "Action": "bssapi:GetPayAsYouGoPrice", "Resource": "*" }, { "Action": [ "cs:Get*", "cs:List*", "cs:Check*", "cs:Describe*" ], "Effect": "Allow", "Resource": [ "acs:cs:*:*:cluster/<yourclusterID>"。 ] }, { "Action": [ "vpc:ListEnhanhcedNatGatewayAvailableZones", "vpc:DescribeEipAddresses" ], "Effect": "Allow", "Resource": "*" } ], "Version": "1" }上面示例中
<yourclusterID>需要替换成实际ACS集群ID。说明如果您只需要为授权对象添加ACS类型ACK集群的只读权限,请务必通过该示例指定ACS类型ACK集群ARN,不可以为其添加容器服务ACK提供的RAM系统策略
AliyunCSReadOnlyAccess,否则将会为授权对象添加除ACS类型以外所有ACK集群的只读权限。RBAC授权
在容器计算服务控制台左侧边栏点击授权管理页面,然后在右侧子账号或RAM角色页签选择授权对象,接着点击管理权限。
在弹窗页面中点击+添加权限,配置目标集群和对应命名空间的权限管理为开发人员,最后点击提交授权完成配置。
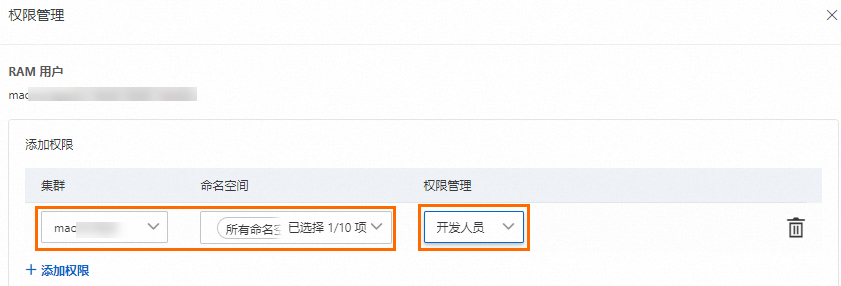
绑定预置角色后,ACS会自动在集群中创建与被授权对象身份对应的ClusterRoleBinding实例。预置开发人员角色的RBAC权限如下所示。
场景三:授权对象为集群内应用的权限管理员
授权对象需要管理其他RAM用户或RAM角色的RBAC权限。默认情况下,RAM用户或RAM角色不具备对其他RAM用户或RAM角色授权RBAC的权限。当授权对象进入容器计算服务控制台授权管理页面时,如果界面提示当前子账号不具备授权管理权限,请联系主账号或权限管理员授权,则说明授权对象缺少必要的RAM授权或对集群的RBAC管理员授权。
RAM授权
需要确保授权对象被授予必要的RAM权限,策略内容需要包括:
列举其他RAM用户或RAM角色
给指定RAM用户或RAM角色授予RAM权限策略
查看指定RAM用户或RAM角色的Kubernetes RBAC权限配置
Kubernetes RBAC授权能力
您需要登录RAM管理控制台,为指定RAM用户或RAM角色授予相应的RAM权限,具体操作,请参见为RAM用户或RAM角色授予RAM权限。RAM自定义策略内容示例如下所示。
{ "Statement": [ { "Effect": "Allow", "Action": [ "acc:DescribeCommodityStatus", "acc:CheckServiceRole", "acc:DescribeCloudProducts", "acc:DescribeRegions", "acc:DescribeZones", "acc:GetInstancePrice", "acc:RecommendZones" ], "Resource": "*" }, { "Effect": "Allow", "Action": "bssapi:GetPayAsYouGoPrice", "Resource": "*" }, { "Action": [ "ram:Get*", "ram:List*", "cs:GetUserPermissions", "cs:GetSubUsers", "cs:GrantPermission", "cs:CheckServiceRole" ], "Resource": "*", "Effect": "Allow" }, { "Action": [ "ram:AttachPolicyToUser", "ram:AttachPolicyToRole" ], "Effect": "Allow", "Resource": [ "acs:ram:*:*:policy/xxxx", # xxxx需要替换成您需要绑定的RAM策略名称。如果您替换成*,表示授权对象拥有所有RAM策略的授权绑定能力。 "acs:*:*:*:user/*" ] }, { "Action": [ "vpc:ListEnhanhcedNatGatewayAvailableZones", "vpc:DescribeEipAddresses" ], "Effect": "Allow", "Resource": "*" } ], "Version": "1" }RBAC授权
在容器计算服务控制台左侧边栏点击授权管理页面,然后在右侧子账号或RAM角色页签选择授权对象,接着点击管理权限。
在弹窗页面中点击+添加权限,配置目标集群和对应命名空间的权限管理为管理员或者自定义角色中的cluster-admin,最后点击提交授权完成配置。
说明阿里云账号(即主账号)和集群创建者会默认绑定cluster-admin,拥有集群内所有Kubernetes资源对象的访问权限。
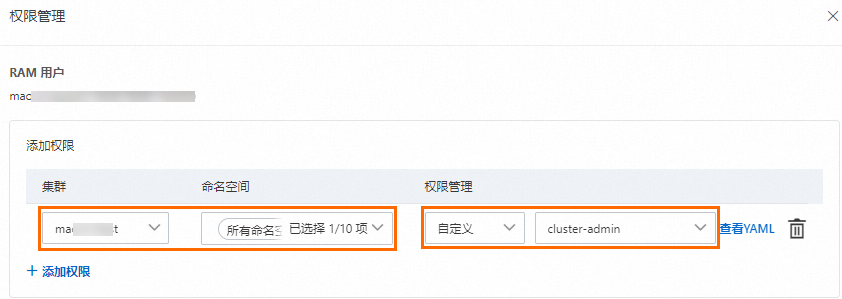
当您对授权对象完成了上述RAM授权和RBAC授权后,即可拥有对其他RAM用户或RAM角色在指定权限范围内的RBAC授权管理能力。具体操作,请参见为RAM用户或RAM角色授予RAM权限。
鉴权Action说明
权限名称(Action) | 说明 |
acc:CheckServiceRole | 检查账号是否授权产品通过角色扮演,访问其他云资源账号的ServiceRole。 |
acc:DescribeCommodityStatus | 检查账号是否已开通ACS产品。 |
权限名称(Action) | 说明 |
bssapi:GetPayAsYouGoPrice | 查询后付费产品询价服务。 |
ram:ListUserBasicInfos | 查询所有RAM用户的基本信息。 |
ram:ListRoles | 查询所有RAM角色的基本信息。 |