描述
阿里云上的Salesforce 将限制 Uninstalled Connected App 的使用。此使用限制将阻止最终用户使用 Uninstalled Connected App。此项变更是阿里云上的Salesforce 致力于加强产品和服务的默认安全性的一部分。
为了最大限度地减少对现有应用使用的干扰,仅当同时满足以下两个条件时,最终用户才能继续使用未安装的应用:
用户之前已授权该应用。
该应用未使用 OAuth 2.0 Device Flow身份验证。
变更生效后:
任何新用户都将无法访问这些未安装的应用。
所有使用 OAuth 2.0 Device Flow 的未安装应用都将被阻止,即使之前已授权该应用的特定用户也无法访问。
在更改之前安装的 Connected App 将继续正常运行,不会中断。
只有拥有特定权限的高度受信任的用户才能使用 Uninstalled Connected App。所需的权限取决于是否启用了 API 访问控制:
如果启用了 API 访问控制,则只有拥有“Use Any API Client” 权限的用户才能访问未安装的应用。
如果未启用 API 访问控制,则拥有“Approve Uninstalled Connected Apps”权限的受信任用户可以使用未安装的应用。此新权限在 Summer '25 中添加,允许受信任的用户自行授权并使用 Uninstalled Connected App。
由于这些权限允许用户绕过 Uninstalled Connected App 的使用限制,建议谨慎分配。例如,仅将这些权限授予负责管理 Connected App,并在将其安装到组织供其他用户访问前进行测试的管理员或开发人员。
安装新的 Connected App 所需的用户权限没有变化,仍然是 Customize Application 以及 Modify All Data 或 Manage Connected Apps 。请审查并安装您希望最终用户可以访问的 Connected App,并阻止不信任的应用。
解决方案
新的“Approve Uninstalled Connected Apps”用户权限
此新用户权限会自动分配给系统管理员标准配置文件。自定义配置文件不会自动更新,包括之前从系统管理员标准配置文件克隆的配置文件。
强制执行 Connected App 使用限制后,此用户权限将授予使用 Uninstalled Connected App 的访问权限,从而绕过新的使用限制。该权限应该只分配给高度受信任的用户,例如管理员和参与管理或测试 Connected App 集成的用户。
“Use Any API Client”用户权限
此用户权限允许用户通过任何 API 客户端访问 Salesforce,包括 Uninstalled Connected App 和被阻止的 Connected App。与“Approve Uninstalled Connected Apps”用户权限一样,此权限也应仅分配给高度受信任的用户,例如需要使用 Uninstalled Connected App 的管理员。如果您启用了 API 访问控制,则需要此权限才能使用 Uninstalled Connected App。如果您未启用 API 访问控制,我们建议您改用“Approve Uninstalled Connected Apps”用户权限。
准备迎接变更
沟通计划
客户管理员或负责管理 Connected App 的用户需要:
将此变更告知最终用户,以防止用户无法访问 Connected App 时出现问题。例如:“由于阿里云上的Salesforce 将限制访问未安装应用,您可能无法访问某些 Connected App。请联系您的 Salesforce 组织管理员,提供您尝试访问的应用名称以及访问请求的原因。”
遵循最小权限原则,建立处理最终用户对未安装应用的新访问请求的流程。
对于 Signature 和 Premier 客户,请更新您的安全联系人,以便他们在未来随时了解安全变更。有关更详细的指导,请参阅文章:管理 Salesforce 组织的安全联系人。
审查 Connected App 的 OAuth 使用情况
客户管理员或负责管理 Connected App 的用户应该审查 Connected App 的 OAuth 使用情况,以识别当前正在使用的未安装应用,并确定他们是否受信任且需要安装,或者是否是不受信任的应用并且应该被阻止。
在变更之前执行这些步骤并安装受信任的应用有助于确保用户持续访问,最大限度地减少中断。如果您不安装受信任的应用,大多数最终用户将在变更生效时被阻止使用这些应用。审查过程也可以在变更之后进行,建议定期审查 Connected App 的使用情况以维护最小权限原则。
1. 在“设置(Setup)”中,找到并选择“已连接应用程序 OAuth 使用情况(Connected Apps OAuth Usage)”。
2. 查看“操作(Action)”列。如果应用未安装,“操作(Action)”列将显示“安装(Install)”按钮。
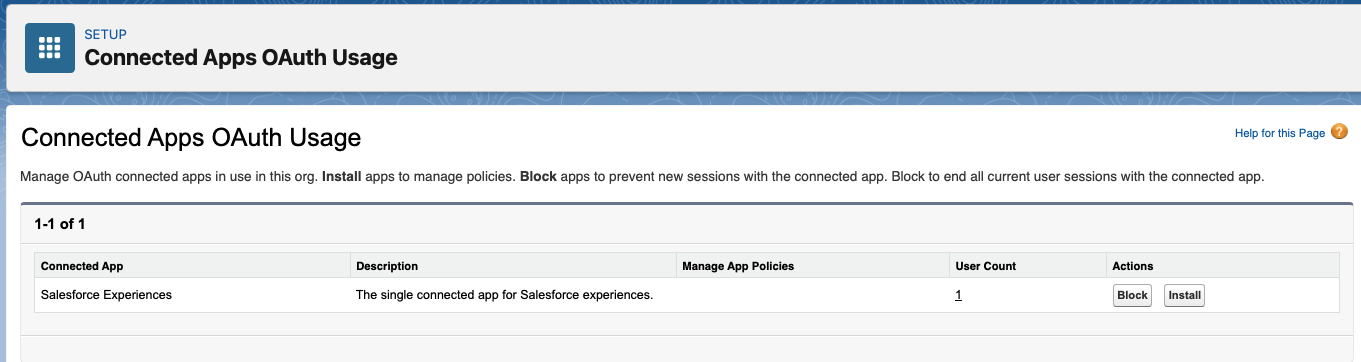
3. 对于每个显示“安装(Install)”按钮的应用,查看应用详细信息和用户数。
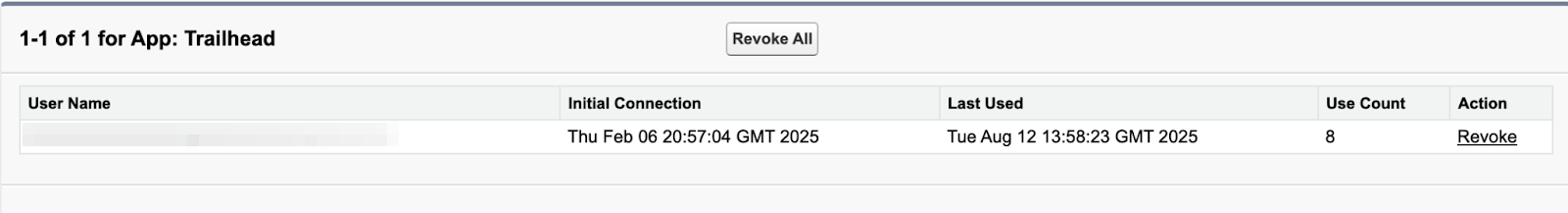
4. 要查看有关哪些用户正在使用应用的更多信息,请单击“用户数(Use Count)”列中的数字。您可以查看哪些用户正在使用该应用、他们首次连接的时间、他们上次使用该应用的时间以及他们的使用次数。
5. 将未安装的应用分为两类:
a. 受信任的应用
b. 不受信任的应用 - 查找您不认识的应用名称和异常的使用模式。
安装受信任的 Connected App
在“设置(Setup)”中,找到并选择“已连接应用程序 OAuth 使用情况(Connected Apps OAuth Usage)”。
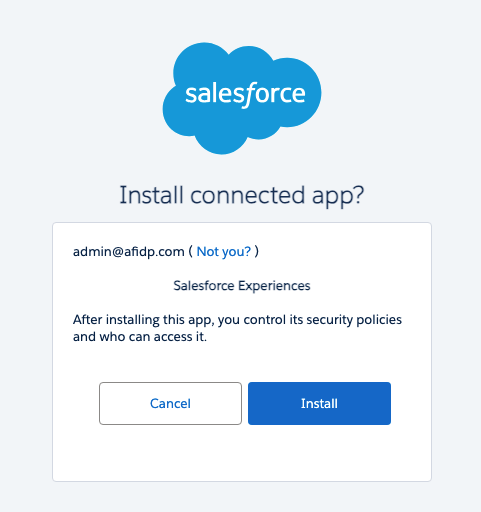
对于每个受信任的应用,单击“安装(Install)”。Salesforce 将显示一个安装页面。
再次单击“安装(Install)”。
管理已安装 Connected App 的访问权限
在您的组织中安装 Connected App 后,您可以管理对它的访问权限。要配置哪些用户可以访问 Connected App,请选择“允许的用户(Permitted Users)”设置。
在“设置(Setup)”中,在“快速查找(Quick Find)”框中输入“已连接应用程序(Connected App)”,然后选择“管理连接的应用程序(Manage Connected Apps)”。
单击您要配置访问权限的 Connected App 旁边的“编辑(Edit)”。
在“OAuth 策略(OAuth Policies)”下,单击“允许的用户(Permitted Users)”下拉菜单并选择以下选项之一。
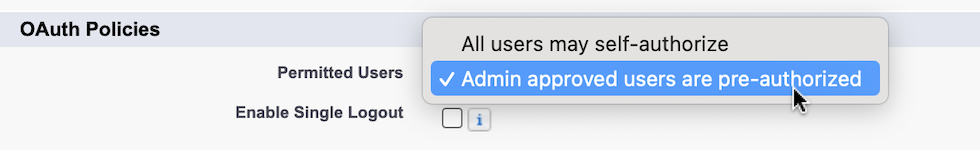
所有用户均可自行授权(All users may self-authorize)(默认):允许组织中的所有用户在成功登录后授权该应用。用户在首次访问应用时必须批准该应用。
管理员批准的用户已预先授权 (Admin approved users are pre-authorized):仅允许具有关联配置文件或权限集的用户在无需先授权的情况下访问该应用。选择此选项后,您需要通过编辑每个配置文件的“Connected App 访问权限”列表或通过编辑每个权限集的“已分配的 Connected App”列表来管理应用的访问权限。
注意:为了最大程度的控制 Connected App 的访问权限,Salesforce 建议使用“管理员批准的用户已预先授权(Admin approved users are pre-authorized)”设置,以便管理员通过配置文件和权限集明确授予访问权限。
有关管理对 Connected App 的访问权限的更多信息,请参考:管理 Connected App 的访问权限。
阻止不受信任的 Connected App
此步骤可确保用户无法再访问不受信任的应用。阻止应用将结束所有当前用户会话并阻止未来会话。
将应用访问权限的变更通知用户。
在“设置(Setup)”中,找到并选择“已连接应用程序 OAuth 使用情况(Connected Apps OAuth Usage)”。
对于每个不受信任的应用,单击“阻止(Block)”。
最终用户错误消息
被阻止访问 Uninstalled Connected App 的用户将看到一条错误消息。错误行为取决于组织中是否启用了 API 访问控制。
错误场景:未启用 API 访问控制
如果未启用 API 访问控制,则最终用户在尝试访问未安装的应用时会在 UI 中看到以下错误消息:“由于 OAuth 错误,我们无法授权您。有关更多信息,请联系您的 Salesforce 管理员。”以及 OAUTH_APPROVAL_ERROR_GENERIC 消息。
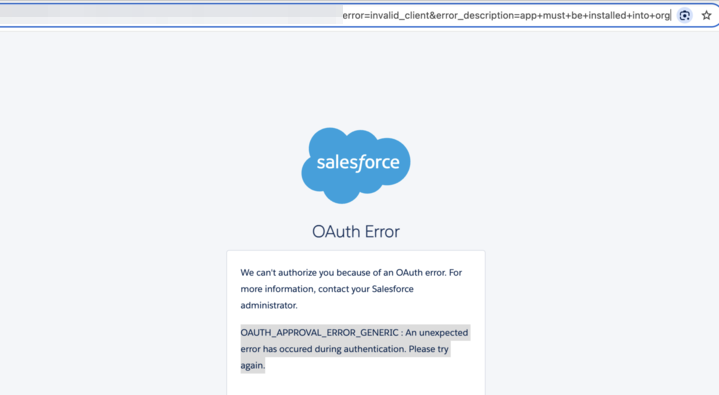
该 URL 使用以下参数更详细地描述了错误:
error=invalid_client
error_description=app must be installed into org
以下是包含此错误的 URL 示例:
https://example[.]com?error=invalid_client&error_description=app+must+be+installed+into+org错误场景:已启用 API 访问控制
如果启用了 API 访问控制,最终用户将被重定向到回调 URL,也称为在 Connected App OAuth 设置中配置的 redirect_uri。
该错误在 URL 中使用以下参数反映:
error=OAUTH_APP_BLOCKED
error_description=this+app+is+blocked+by+admin
以下是包含此错误的 URL 示例:
https://example.com?error=OAUTH_APP_BLOCKED&error_description=this+app+is+blocked+by+admin常见问题(FAQ)
此功能变更有哪些好处?
此更新增强了您对 Connected App 的控制,并降低了未经授权访问 Connected App 的风险。
此变更会影响哪些方面?
用户将被阻止访问 Uninstalled Connected App。要访问新的 Connected App,必须先将应用安装到组织中。之前已授权Uninstalled Connected App 的用户可以继续使用,但新用户将无法访问。此外,所有使用 OAuth 2.0 Device Flow 的未安装应用都将被阻止,即使用户之前已授权该应用也是如此。
现在需要特定的用户权限(“Approve Uninstalled Connected Apps”和“Use Any API Client”)才能使用 Uninstalled Connected App。Salesforce 建议谨慎分配这些权限,因为它们允许用户绕过对使用 Uninstalled Connected App 的限制。例如,仅授予管理员以及在将应用安装到组织供其他用户访问前需要测试 Connected App 的用户。
此变更不会影响哪些方面?
在此变更之前安装的 Connected App 将继续正常运行,不会中断。
如果 Salesforce 最终用户在此变更之前已授权 Connected App,则即使该应用未安装在组织中,用户也可以继续使用。
API 访问控制和新的 Connected App 使用限制之间有什么区别?
API 访问控制是一项现有的可选功能,您可以使用它来限制用户访问 Salesforce API。启用此功能后,用户只能通过您列入允许列表的特定 Connected App 访问 Salesforce API。您自行决定允许列表的标准。要启用 API 访问控制,您必须联系 Salesforce 客户支持。
新的 Connected App 使用限制是一项新的强制限制,将自动为所有组织启用。它无法关闭并限制最终用户访问 Uninstalled Connected App。
什么是“Uninstalled Connected App”,如何识别正在使用的未安装应用?
“Uninstalled Connected App”是指未由系统管理员明确安装到 Salesforce 组织中的应用。相反,Salesforce 最终用户可登录并通过 OAuth 授权页面来直接授权。
要查找 Uninstalled Connected App,请在“设置”中导航到“OAuth Connected App Usage”页面。查找在“操作”列中显示“安装”按钮的应用程序。这些应用将受到新限制的影响。请注意,最近未使用的应用可能不会显示在此页面上。
此变更对在组织内创建和管理的 Connected App 有什么影响?
此变更对在组织内创建和管理的 Connected App 没有影响。
我如何知道这些变更何时应用于我的组织?
当客户管理员在“设置”中看到新的“Approve Uninstalled Connected Apps”用户权限已分配给标准系统管理员配置文件时,即可确认这些变更已在其组织中生效。
这对浏览器扩展程序有什么影响?
浏览器扩展程序的行为类似于其他 Connected App,并受相同的限制。
这些变更将如何影响之前已授权未安装应用的现有用户与首次尝试访问它的新用户?
现有用户:之前已授权未安装应用(且该应用未使用 OAuth 2.0 Device Flow)的用户将能够继续使用它,而不会立即受到干扰。
新用户:尝试访问这些未安装应用的新用户都将被阻止。
使用 OAuth 2.0 Device Flow 的应用:所有使用 OAuth 2.0 Device Flow 的未安装应用都将被阻止访问,即使用户在此变更之前已授权该应用也是如此。Device Flow 通常用于输入功能受限的设备。
Description
Salesforce on Alibaba Cloud will restrict the use of uninstalled connected apps. This usage restriction will block end users from using uninstalled connected apps. This change is part of Salesforce on Alibaba Cloud's commitment to making our products and services secure-by-default.
To minimize disruption to existing app usage, end users can continue to use uninstalled apps only if both of these criteria apply.
The user has previously authorized the app.
The app isn't using the OAuth 2.0 device flow.
Once the changes are active:
Any new user trying to access these same uninstalled apps will be blocked.
All uninstalled apps that use the OAuth 2.0 device flow will be blocked, even for specific users who have previously authorized the app.
Connected apps installed before the change will continue to function without interruption.
Only highly trusted users with certain permissions can use uninstalled connected apps. The required permissions depend on whether API Access Control is enabled.
If API Access Control is enabled, only the "Use Any API Client" permission gives access to use uninstalled apps.
If API Access Control isn't enabled, trusted users can use uninstalled apps if they have the "Approve Uninstalled Connected Apps" permission: This new permission, added in Summer '25, allows trusted users to self-authorize and use uninstalled connected apps.
Salesforce recommends using care when assigning these permissions as they allow users to bypass the restriction on using uninstalled connected apps. For example, you might only give these permissions to users, such as an admin or developer, who manage connected apps and need to test the apps before installing them on the org for access by other end users.
There is no change to user permissions required to install new connected apps, which are Customize Application AND either Modify All Data OR Manage Connected Apps. Take steps to review and install connected apps that you want to make accessible for end-users. Block any apps that you do not trust.
Resolution
New Approve Uninstalled Connected Apps user permission
This new user permission is automatically assigned to the System Administrator standard profile. Custom profiles aren't automatically updated, including those previously cloned from the System Administrator standard profile.
After the connected app usage restriction is enforced, this user permission grants access to use uninstalled connected apps, bypassing the new usage restriction. It should only be assigned to highly trusted users, such as administrators and those involved in managing or testing connected app integrations.
Use Any API Client user permission
This user permission allows users to access Salesforce via any API client, including uninstalled connected apps and blocked connected apps. Like the "Approve Uninstalled Connected Apps" user permission, this permission should only be assigned to highly trusted users, such as admins, who need to use uninstalled connected apps.This permission is required to use uninstalled apps if you have API Access Control enabled. If you don't have API Access Control enabled, we recommend that you use the "Approve Uninstalled Connected Apps" user permission instead.
Prepare for the Change
Communication Plan
Customer Admins or users responsible for managing connected apps should:
Communicate this change to end-users to prevent issues if users can't access connected apps. For example: "You may face issues accessing some connected apps since restrictions were put in place for accessing uninstalled apps. Please contact your Salesforce on Alibaba Cloud Org Admin, provide with the name of the application you are trying to access, and reason for the access request. "
Establish a process for handling new end-user access requests for uninstalled apps following the least privileged principle.
For Signature & Premier customers, update your Security contacts to keep them informed on security changes in the future. For more detailed guidance, refer to the article: Manage Security Contacts for Your Salesforce Organization.
Review OAuth Usage for Connected Apps
Customer Admins or users responsible for managing connected apps should review connected app OAuth Usage to identify uninstalled apps currently being used, and determine if they are trusted and need installed or if they are untrusted apps and should be blocked.
Performing these steps before the change and installing trusted apps helps ensure continued user access, minimizing disruption. If you don't install trusted apps, most end users will be blocked from using these apps when this change takes effect. The review process can also occur after the change, and regular reviews of connected app usage are recommended to uphold the principle of least privilege.
1. In Setup, find and select Connected Apps OAuth Usage.
2. Review the Action column. If an app is uninstalled, the action column displays an Install button.
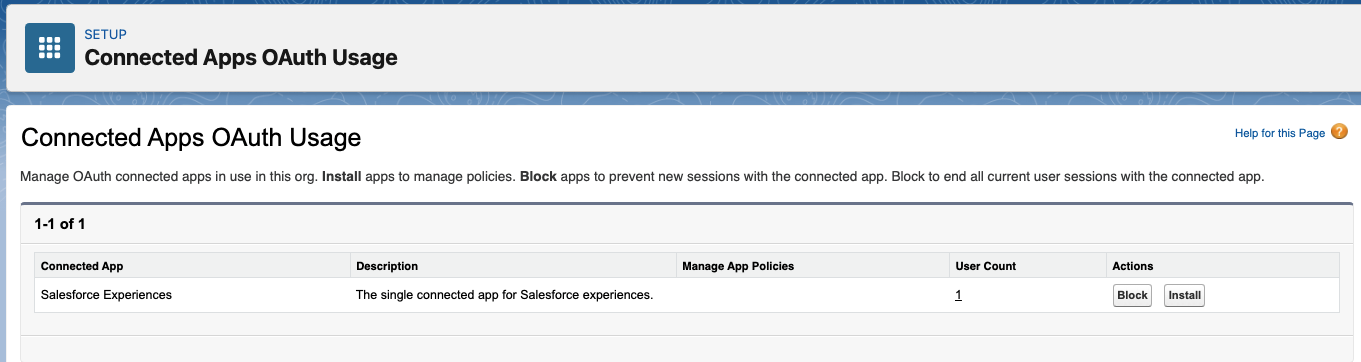
3. For each app that displays an Install button, review the app details and the User Count.
4. To see more information about which users are using an app, click the number in the User Count column. You can see which users are using the app, when they first connected, when they last used the app, and their use count.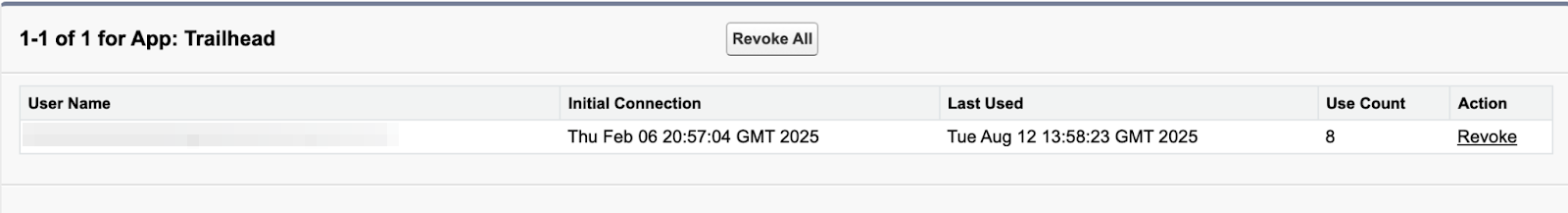
5. Group uninstalled apps into two categories:
a. Trusted apps
b. Untrusted apps - Look for app names that you don't recognize, and unusual usage patterns.
Install Trusted Connected Apps
In Setup, find and select Connected Apps OAuth Usage.
For each trusted app, click Install. Salesforce displays an installation page.
Click Install again.
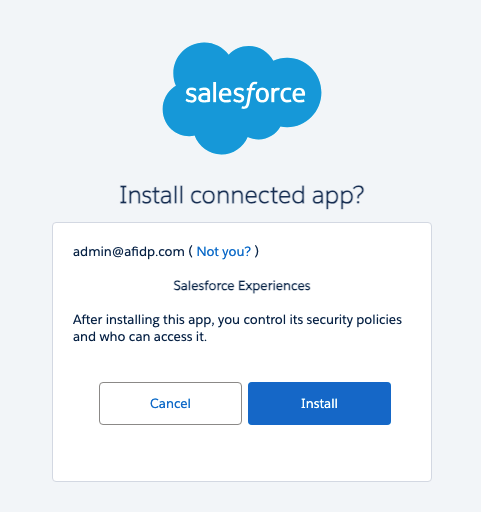
Mange Access to a Connected App After Install
After a connected app is installed in your org, you can manage access to it. To configure which users can access the connected app, select a Permitted Users setting.
From Setup, enter Connected Apps in the Quick Find box, then select Manage Connected Apps.
Click Edit next to the connected app that you are configuring access for.
Under OAuth Policies, click the Permitted Users dropdown menu and select one of the following options.

All users may self-authorize—Default. Allows all users in the org to authorize the app after successfully signing in. Users must approve the app the first time they access it.
Admin approved users are pre-authorized—Allows only users with the associated profile or permission set to access the app without first authorizing it. After selecting this option, manage profiles for the app by editing each profile's Connected App Access list. Or manage permission sets for the app by editing each permission set's Assigned Connected App list.
Note: Salesforce recommends the Admin approved users are pre-authorized setting as this provides the most control over who can access the connected app by allowing the Admin to explicitly grant access through profiles and permission sets, restricting access to only authorized users.
See the help article Manage Access to a Connected App for more information.
Block Untrusted Connected Apps
This step ensures that users can no longer access untrusted apps. Blocking an app ends all current user sessions and prevents future sessions.
Notify users about changes to their app access.
In Setup, find and select Connected Apps OAuth Usage.
For each untrusted app, click Block.
End User Error Messages
Users who are blocked from accessing uninstalled connected apps will see an error message. The error behaviour depends on whether API Access Control is enabled in the org.
Error Scenario: API Access Control Isn't Enabled
If API Access control isn't enabled, end users see the following error message in the UI if they try to access an uninstalled app: "We can't authorize you because of an OAuth error. For more information, contact your Salesforce administrator." and the OAUTH_APPROVAL_ERROR_GENERIC message.
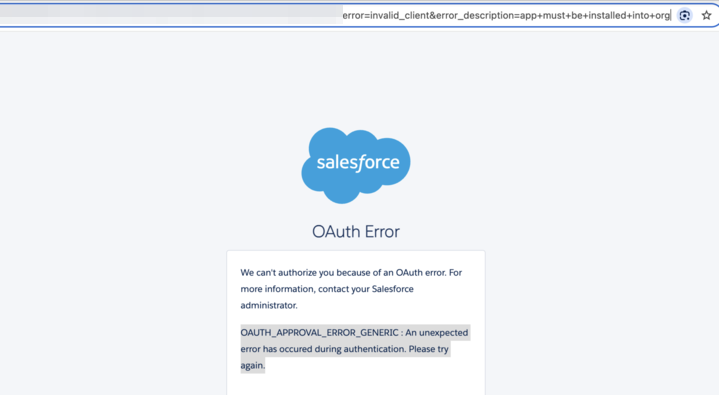
The URL describes the error in more detail using these parameters.
error=invalid_client
error_description=app must be installed into org
Here's an example URL with this error.
https://example[.]com?error=invalid_client&error_description=app+must+be+installed+into+orgError Scenario: API Access Control Is Enabled
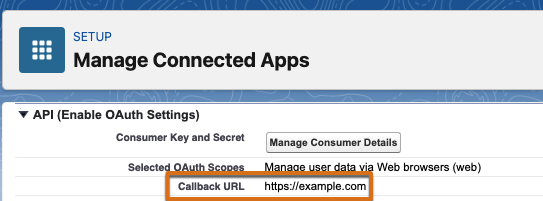
If API Access Control is enabled, end users are redirected to the Callback URL, also known as the redirect_uri configured in your connected app OAuth settings.
The error is reflected in the URL using these parameters.
error=OAUTH_APP_BLOCKED
error_description=this+app+is+blocked+by+admin
Here's an example URL with this error.
https://example.com?error=OAUTH_APP_BLOCKED&error_description=this+app+is+blocked+by+adminFrequently Asked Questions (FAQ)
What are the benefits of this feature change?
This update enhances your control over connected apps, and reduces the risk of unauthorized connected app access.
What does this change impact?
Users will be blocked from accessing uninstalled connected apps. In order to access new connected apps, the apps must be installed on the org. While users who previously authorized the uninstalled connected app can continue using those apps, any new user trying to access the same uninstalled apps will be blocked. Also, all usage of uninstalled apps that use the OAuth 2.0 device flow will be blocked, even if the user has previously authorized the app.
Specific user permissions ("Approve Uninstalled Connected Apps" and "Use Any API Client") are now required to use uninstalled connected apps. Salesforce recommends using care when assigning these permissions as it allows users to bypass the restriction on using uninstalled connected apps. For example, you might only give these permissions to users, such as an admin or developer, who manage connected apps and need to test the apps before installing them on the org for access of other end users.
What does this change not impact?
Connected apps installed prior to this change will continue to function without interruption.
If a Salesforce end-user has authorized a connected app prior to this change, that user can continue using it without interruption, even when the app is not installed on the org.
What is the difference between API Access Control and the new connected app usage restriction?
API Access Control is an existing, optional feature that you can use to restrict users from accessing Salesforce APIs.
When this feature is enabled, users can access Salesforce APIs only though specific connected apps that you allowlist. You determine the criteria for the allowlist. To turn on API Access Control, you must contact Salesforce Customer Support.
The new connected app usage restriction is a new, required restriction that will be automatically enabled for all orgs. It can't be turned off. It restricts end users from accessing uninstalled connected apps.
What are "uninstalled connected apps" and how do I identify which ones are being used?
An "uninstalled connected app" is an application that was not explicitly installed by a System Administrator into your Salesforce org. Instead, a Salesforce end-user directly authorized it by logging in and granting access via an OAuth authorization page.
To find uninstalled connected apps, navigate to the "OAuth Connected App Usage" page in Setup. Look for applications that display an "Install" button in the "Actions" column. These are the apps that will be impacted by the new restrictions. Note that apps not used recently may not appear on this page.
What is the impact for connected apps created and managed within the Org?
There is no impact from this change to connected apps created and managed on the org.
How will I know when the changes are applied in my org?
Customer Admins can confirm that these changes are in effect for their org when they can see the new "Approve Uninstalled Connected Apps" user permission assigned to the standard System Administrator profile in Setup.
What is the impact on browser extensions?
Browser extensions behave like other Connected Apps and are subject to the same restrictions.
How will these changes affect existing users who have previously authorized an uninstalled app versus new users attempting to access it for the first time?
Existing Usage: Users who have previously authorized an uninstalled app (and it is not using the OAuth 2.0 device flow) will be able to continue using it without immediate disruption.
New Usage: However, all new users of these previously authorized uninstalled apps will be blocked.
OAuth 2.0 Device Flow Impact: All usage of uninstalled apps that specifically use the OAuth 2.0 device flow will be blocked, even if the user had authorized the app prior to this change. Device flow is typically used for devices with limited input capabilities.
