通过Terraform增加RDS PostgreSQL实例的数据安全性
本文介绍如何使用Terraform修改安全组、修改IP白名单、修改SSL配置以及切换高安全模式。
本教程所含示例代码支持一键运行,您可以直接运行代码。一键运行
前提条件
已创建RDS PostgreSQL实例,详情请参见创建RDS PostgreSQL实例。
实例状态为运行中,您可以通过如下两种方式查看:
由于阿里云账号(主账号)具有资源的所有权限,一旦发生泄露将面临重大风险。建议您使用RAM用户,并为该RAM用户创建AccessKey,具体操作方式请参见创建RAM用户和创建AccessKey。
通过RAM授权,RAM用户可以有效地管理其云资源访问权限,适应多用户协同工作的需求,并且能够按需为用户分配最小权限,避免权限过大导致的安全漏洞。具体操作方式请参见为RAM用户授权。
{ "Version": "1", "Statement": [ { "Effect": "Allow", "Action": [ "vpc:DescribeVpcAttribute", "vpc:DescribeRouteTableList", "vpc:DescribeVSwitchAttributes", "vpc:DeleteVpc", "vpc:DeleteVSwitch", "vpc:CreateVpc", "vpc:CreateVSwitch", "vpc:DescribeVSwitches", "ecs:CreateSecurityGroup", "ecs:ModifySecurityGroupPolicy", "ecs:DescribeSecurityGroups", "ecs:ListTagResources", "ecs:DeleteSecurityGroup", "ecs:DescribeSecurityGroupAttribute", "ecs:AuthorizeSecurityGroup", "ecs:RevokeSecurityGroup" ], "Resource": "*" }, { "Action": "rds:*", "Resource": "*", "Effect": "Allow" }, { "Action": "dbs:*", "Resource": "acs:rds:*:*:*", "Effect": "Allow" }, { "Action": "hdm:*", "Resource": "acs:rds:*:*:*", "Effect": "Allow" }, { "Action": "dms:LoginDatabase", "Resource": "acs:rds:*:*:*", "Effect": "Allow" }, { "Effect": "Allow", "Action": "ram:CreateServiceLinkedRole", "Resource": "*", "Condition": { "StringEquals": { "ram:ServiceName": [ "backupencryption.rds.aliyuncs.com" ] } } }, { "Effect": "Allow", "Action": "bss:ModifyAgreementRecord", "Resource": "*" }, { "Effect": "Allow", "Action": [ "bss:DescribeOrderList", "bss:DescribeOrderDetail", "bss:PayOrder", "bss:CancelOrder" ], "Resource": "*" } ] }准备Terraform运行环境,您可以选择以下任一方式来使用Terraform。
在Terraform Explorer中使用Terraform:阿里云提供了Terraform的在线运行环境,您无需安装Terraform,登录后即可在线使用和体验Terraform。适用于零成本、快速、便捷地体验和调试Terraform的场景。
Cloud Shell:阿里云Cloud Shell中预装了Terraform的组件,并已配置好身份凭证,您可直接在Cloud Shell中运行Terraform的命令。适用于低成本、快速、便捷地访问和使用Terraform的场景。
在本地安装和配置Terraform:适用于网络连接较差或需要自定义开发环境的场景。
使用的资源
本教程示例包含的部分资源会产生一定费用,请在不需要时及时进行释放或退订。
alicloud_vpc:创建专有网络VPC。
alicloud_vswitch:创建专有网络交换机。
alicloud_db_instance:创建RDS PostgreSQL实例。
修改安全组
以修改实例安全组为sg-****为例。
创建一个工作目录,并在该工作目录中创建名为main.tf的配置文件,然后将以下代码复制到main.tf中。
创建前置资源。
variable "region" { default = "cn-shenzhen" } variable "zone_id" { default = "cn-shenzhen-c" } variable "instance_type" { default = "pg.n2.2c.2m" } provider "alicloud" { region = var.region } # 创建VPC resource "alicloud_vpc" "main" { vpc_name = "alicloud" cidr_block = "172.16.0.0/16" } # 创建交换机 resource "alicloud_vswitch" "main" { vpc_id = alicloud_vpc.main.id cidr_block = "172.16.192.0/20" zone_id = var.zone_id } # 新建安全组 resource "alicloud_security_group" "example" { name = "terraform-example" vpc_id = alicloud_vpc.main.id } # 创建RDS PostgreSQL实例 resource "alicloud_db_instance" "instance" { engine = "PostgreSQL" engine_version = "13.0" instance_type = var.instance_type instance_storage = "30" instance_charge_type = "Postpaid" vswitch_id = alicloud_vswitch.main.id }在main.tf文件的
resource "alicloud_db_instance" "instance" {}中增加security_group_ids配置项,具体配置如下。... resource "alicloud_db_instance" "instance" { ... security_group_ids = [alicloud_security_group.example.id] }
说明修改安全组会覆盖原有安全组,后续修改时请在
[]中追加即可,使用,分隔。执行以下命令,初始化Terraform运行环境。
terraform init返回如下信息,表示Terraform初始化成功。
Initializing the backend... Initializing provider plugins... - Checking for available provider plugins... - Downloading plugin for provider "alicloud" (hashicorp/alicloud) 1.90.1... ... You may now begin working with Terraform. Try running "terraform plan" to see any changes that are required for your infrastructure. All Terraform commands should now work. If you ever set or change modules or backend configuration for Terraform, rerun this command to reinitialize your working directory. If you forget, other commands will detect it and remind you to do so if necessary.创建执行计划,并预览变更。
terraform plan执行以下命令,创建资源。
terraform apply在执行过程中,根据提示输入
yes并按下Enter键,等待命令执行完成,若出现以下信息,则表示运行成功。alicloud_db_instance.instance: Modifying... [id=pgm-****] alicloud_db_instance.instance: Modifications complete after 4s [id=pgm-****] Apply complete! Resources: 0 added, 1 changed, 0 destroyed.验证结果。
执行terraform show命令
您可以使用以下命令查看安全组
terraform show# alicloud_db_instance.instance: resource "alicloud_db_instance" "instance" { client_ca_enabled = 0 client_crl_enabled = 0 connection_string = "pgm-****.pg.rds.aliyuncs.com" connection_string_prefix = "pgm-****" db_instance_storage_type = "cloud_essd" db_time_zone = "Asia/shenzhen" deletion_protection = false engine = "PostgreSQL" engine_version = "13.0" force_restart = false ha_config = "Manual" id = "pgm-****" instance_charge_type = "Postpaid" instance_name = "terraformtest" instance_storage = 50 instance_type = "pg.n2.2c.2m" maintain_time = "05:00Z-06:00Z" manual_ha_time = "2022-09-30T09:00:00Z" monitoring_period = 300 period = 0 port = "5432" private_ip_address = "192.168.XX.XX" resource_group_id = "rg-****" security_group_id = "sg-****" security_group_ids = [ "sg-****", ] security_ip_mode = "normal" security_ips = [ "127.0.0.1", ] sql_collector_config_value = 30 sql_collector_status = "Disabled" storage_auto_scale = "Enable" storage_threshold = 30 storage_upper_bound = 100 target_minor_version = "rds_postgres_1300_20220830" tcp_connection_type = "SHORT" vpc_id = "vpc-****" vswitch_id = "vsw-****" zone_id = "cn-hangzhou-j" pg_hba_conf { address = "127.0.0.1" database = "all" method = "md5" priority_id = 1 type = "host" user = "all" } }登录RDS管理控制台
登录RDS管理控制台查看安全组。
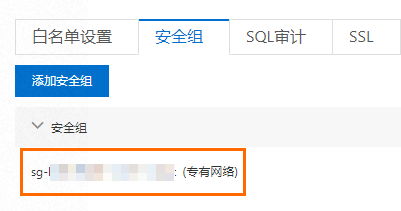
修改IP白名单
以修改白名单为0.0.0.0/0为例。
在main.tf文件的
resource "alicloud_db_instance" "instance" {}中增加security_ips配置项,具体配置如下。... resource "alicloud_db_instance" "instance" { ... security_ips = ["0.0.0.0/0"] }说明修改白名单会覆盖原有默认白名单,后续修改时请在
[]中追加即可,使用,分隔。执行以下命令。
terraform apply在执行过程中,根据提示输入
yes并按下Enter键,等待命令执行完成,若出现以下信息,则表示运行成功。alicloud_db_instance.instance: Modifying... [id=pgm-****] alicloud_db_instance.instance: Modifications complete after 6s [id=pgm-****] Apply complete! Resources: 0 added, 1 changed, 0 destroyed.验证结果。
执行terraform show命令
您可以使用以下命令查看IP白名单。
terraform show# alicloud_db_account.account: resource "alicloud_db_account" "account" { account_name = "tf_account_test" account_password = (sensitive value) account_type = "Normal" db_instance_id = "pgm-****" id = "pgm-****:tf_account_test" instance_id = "pgm-****" name = "tf_account_test" status = "Available" type = "Normal" } # alicloud_db_instance.instance: resource "alicloud_db_instance" "instance" { client_ca_enabled = 0 client_crl_enabled = 0 connection_string = "pgm-****.pg.rds.aliyuncs.com" connection_string_prefix = "pgm-****" db_instance_storage_type = "cloud_essd" db_time_zone = "Asia/shenzhen" deletion_protection = false engine = "PostgreSQL" engine_version = "13.0" force_restart = false ha_config = "Auto" id = "pgm-****" instance_charge_type = "Postpaid" instance_name = "terraformtest" instance_storage = 50 instance_type = "pg.n2.2c.2m" maintain_time = "05:00Z-06:00Z" monitoring_period = 300 period = 0 port = "5432" private_ip_address = "172.16.XX.XX" resource_group_id = "rg-****" security_group_ids = [] security_ip_mode = "normal" security_ips = [ "127.0.0.1", ] sql_collector_config_value = 30 sql_collector_status = "Disabled" storage_auto_scale = "Enable" storage_threshold = 30 storage_upper_bound = 100 target_minor_version = "rds_postgres_1300_20220730" tcp_connection_type = "SHORT" vpc_id = "vpc-****" vswitch_id = "vsw-****" zone_id = "cn-heyuan-j" pg_hba_conf { address = "127.0.0.1" database = "all" method = "md5" priority_id = 1 type = "host" user = "all" } }登录RDS管理控制台
登录RDS管理控制台查看IP白名单。
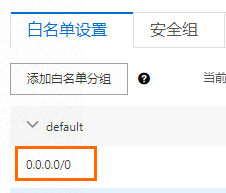
修改SSL设置
以开启SSL加密为例。
在main.tf文件的
resource "alicloud_db_instance" "instance" {}中增加ssl_action配置项,具体配置如下:... resource "alicloud_db_instance" "instance" { ... ssl_action = "Open" }执行以下命令。
terraform apply在执行过程中,根据提示输入
yes并按下Enter键,等待命令执行完成,若出现以下信息,则表示运行成功。alicloud_db_instance.instance: Modifying... [id=pgm-****] alicloud_db_instance.instance: Still modifying... [id=pgm-****, 10s elapsed] ... alicloud_db_instance.instance: Still modifying... [id=pgm-****, 6m31s elapsed] alicloud_db_instance.instance: Modifications complete after 6m35s [id=pgm-****] Apply complete! Resources: 0 added, 1 changed, 0 destroyed.验证结果。
执行terraform show命令
您可以使用以下命令查看SSL设置。
terraform show# alicloud_db_instance.instance: resource "alicloud_db_instance" "instance" { acl = "prefer" ca_type = "aliyun" client_ca_enabled = 0 client_crl_enabled = 0 connection_string = "pgm-****.pg.rds.aliyuncs.com" connection_string_prefix = "pgm-****" db_instance_storage_type = "cloud_essd" db_time_zone = "Asia/shenzhen" deletion_protection = false engine = "PostgreSQL" engine_version = "13.0" force_restart = false ha_config = "Auto" id = "pgm-****" instance_charge_type = "Postpaid" instance_name = "terraformtest" instance_storage = 50 instance_type = "pg.n2.2c.2m" maintain_time = "05:00Z-06:00Z" monitoring_period = 300 period = 0 port = "5432" private_ip_address = "192.168.XX.XX" replication_acl = "prefer" resource_group_id = "rg-****" security_group_id = "sg-****" security_group_ids = [ "sg-****", ] security_ip_mode = "normal" security_ips = [ "0.0.0.0/0", ] server_cert = <<-EOT -----BEGIN CERTIFICATE----- MIIE7jCCA9agAwIBAgICO3****2 N9xwKlPQ65q/kux0yErtwhAD -----END CERTIFICATE----- EOT server_key = <<-EOT -----BEGIN RSA PRIVATE KEY----- MIIJKQIBAAKCAgEAux0yE****e+VAdGp -----END RSA PRIVATE KEY----- EOT sql_collector_config_value = 30 sql_collector_status = "Disabled" ssl_action = "Open" ssl_status = "0" storage_auto_scale = "Enable" storage_threshold = 30 storage_upper_bound = 100 target_minor_version = "rds_postgres_1300_20220830" tcp_connection_type = "SHORT" vpc_id = "vpc-****" vswitch_id = "vsw-****" zone_id = "cn-hangzhou-j" pg_hba_conf { address = "127.0.0.1" database = "all" method = "md5" priority_id = 1 type = "host" user = "all" } }登录RDS管理控制台
登录RDS管理控制台查看SSL设置。
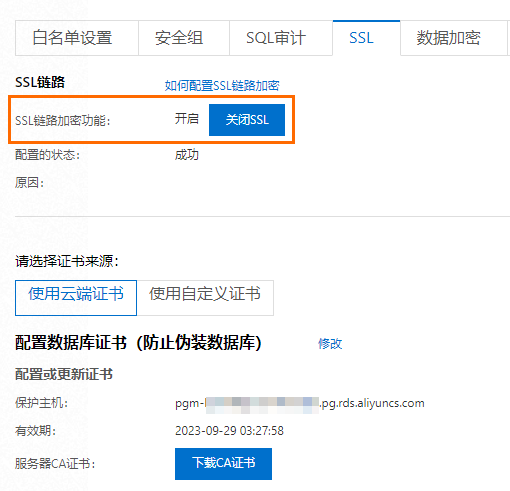
切换高安全白名单模式(仅高性能本地盘实例适用)
在main.tf文件的
resource "alicloud_db_instance" "instance" {}中增加security_ip_mode配置项,具体配置如下。... resource "alicloud_db_instance" "instance" { ... security_ip_mode = "safety" }说明高安全模式无法切换回通用模式。
执行以下命令。
terraform apply在执行过程中,根据提示输入
yes并按下Enter键,等待命令执行完成,若出现以下信息,则表示运行成功。alicloud_db_instance.instance: Modifying... [id=pgm-****] alicloud_db_instance.instance: Modifications complete after 3s [id=pgm-****] Apply complete! Resources: 0 added, 1 changed, 0 destroyed.验证结果。
执行terraform show命令
您可以使用以下命令查看白名单模式。
terraform show# alicloud_db_instance.instance: resource "alicloud_db_instance" "instance" { acl = "prefer" ca_type = "aliyun" client_ca_enabled = 0 client_crl_enabled = 0 connection_string = "pgm-****.pg.rds.aliyuncs.com" connection_string_prefix = "pgm-****" db_instance_storage_type = "cloud_essd" db_time_zone = "Asia/shenzhen" deletion_protection = false engine = "PostgreSQL" engine_version = "13.0" force_restart = false ha_config = "Auto" id = "pgm-****" instance_charge_type = "Postpaid" instance_name = "terraformtest" instance_storage = 50 instance_type = "pg.n2.2c.2m" maintain_time = "05:00Z-06:00Z" monitoring_period = 300 period = 0 port = "5432" private_ip_address = "192.168.XX.XX" replication_acl = "prefer" resource_group_id = "rg-****" security_group_id = "sg-****" security_group_ids = [ "sg-****", ] security_ip_mode = "safety" security_ip_mode = "normal" security_ips = [ "0.0.0.0/0", ] server_cert = <<-EOT -----BEGIN CERTIFICATE----- MIIE7jCCA9agAwIBAgICO3****2 N9xwKlPQ65q/kux0yErtwhAD -----END CERTIFICATE----- EOT server_key = <<-EOT -----BEGIN RSA PRIVATE KEY----- MIIJKQIBAAKCAgEAux0yE****e+VAdGp -----END RSA PRIVATE KEY----- EOT sql_collector_config_value = 30 sql_collector_status = "Disabled" ssl_action = "Open" ssl_status = "0" storage_auto_scale = "Enable" storage_threshold = 30 storage_upper_bound = 100 target_minor_version = "rds_postgres_1300_20220830" tcp_connection_type = "SHORT" vpc_id = "vpc-****" vswitch_id = "vsw-****" zone_id = "cn-hangzhou-j" pg_hba_conf { address = "127.0.0.1" database = "all" method = "md5" priority_id = 1 type = "host" user = "all" } }登录RDS管理控制台
登录RDS管理控制台查看账号信息。
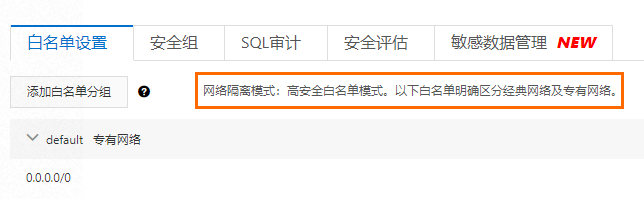
清理资源
当您不再需要上述通过Terraform创建或管理的资源时,请运行以下命令以释放资源。关于terraform destroy的更多信息,请参见Terraform常用命令。
terraform destroy完整示例
当前示例代码支持一键运行,您可以直接运行代码。一键运行
示例代码
如果您想体验更多完整示例,请前往更多完整示例中对应产品的文件夹查看。
