您可以通过Terraform创建并管理凭据。本文以创建凭据为例进行介绍。
概述
KMS使用指定的密钥对凭据进行加密保护,因此在创建凭据前,请先创建密钥。关于凭据的更多信息,请参见凭据管理概述。
当前示例代码支持一键运行,您可以直接运行代码。一键运行
前提条件
由于阿里云账号(主账号)具有资源的所有权限,一旦发生泄露将面临重大风险。建议您使用RAM用户,并为该RAM用户创建AccessKey,具体操作方式请参见创建RAM用户和创建AccessKey。
使用以下示例为RAM用户授权,需要为该RAM用户授予以下权限:AliyunKMSFullAccess(管理密钥管理服务)和AliyunRAMFullAccess(管理访问控制RAM的权限)。具体操作方式请参见为RAM用户授权。
{ "Version": "1", "Statement": [ { "Action": "kms:*", "Resource": "*", "Effect": "Allow" }, { "Action": "ram:CreateServiceLinkedRole", "Condition": { "StringEquals": { "ram:ServiceName": [ "secretsmanager-rds.kms.aliyuncs.com", "keystore.kms.aliyuncs.com" ] } }, "Resource": "*", "Effect": "Allow" } ] }准备Terraform运行环境,您可以选择以下任一方式来使用Terraform。
在Terraform Explorer中使用Terraform:阿里云提供了Terraform的在线运行环境,您无需安装Terraform,登录后即可在线使用和体验Terraform。适用于零成本、快速、便捷地体验和调试Terraform的场景。
Cloud Shell:阿里云Cloud Shell中预装了Terraform的组件,并已配置好身份凭证,您可直接在Cloud Shell中运行Terraform的命令。适用于低成本、快速、便捷地访问和使用Terraform的场景。
在本地安装和配置Terraform:适用于网络连接较差或需要自定义开发环境的场景。
请确保Terraform版本不低于v0.12.28。如需检查现有版本,请运行terraform --version命令。
使用的资源
alicloud_kms_secret:创建并管理凭据。
alicloud_vpc:创建专有网络VPC。
alicloud_vswitch:创建虚拟交换机(vSwitch)为VPC划分一个或多个子网。
alicloud_kms_instance:购买并启用KMS软件密钥管理实例。
alicloud_kms_key:创建并管理应用身份凭证。
alicloud_kms_alias:创建并管理别名。
通过Terraform创建凭据
建议您对secret_data(凭据值)设置sensitive = true以避免将敏感的凭据值在日志或控制台中打印。更多介绍请参考保护敏感输入变量(Protect Sensitive Input Variables)。
本示例将创建一个通用凭据。
创建一个工作目录,并且在工作目录中创建以下名为
main.tf的配置文件。在
main.tf中增加以下内容,在此之前,请确保您已创建KMS实例和密钥:重要加密凭据值的密钥必须为对称密钥。
创建KMS实例:
variable "region" { default = "cn-heyuan" } provider "alicloud" { region = var.region } variable "instance_name" { default = "tf-kms-vpc-172-16" } # 创建VPC resource "alicloud_vpc" "vpc" { vpc_name = var.instance_name cidr_block = "192.168.0.0/16" } # 创建一个Vswitch CIDR 块为 192.168.10.0.24 resource "alicloud_vswitch" "vsw" { vpc_id = alicloud_vpc.vpc.id cidr_block = "192.168.10.0/24" zone_id = "cn-heyuan-a" vswitch_name = "terraform-example-1" } # 创建另一个Vswitch CIDR 块为 192.168.20.0/24 resource "alicloud_vswitch" "vsw1" { vpc_id = alicloud_vpc.vpc.id cidr_block = "192.168.20.0/24" zone_id = "cn-heyuan-b" vswitch_name = "terraform-example-2" } # 创建KMS软件密钥管理实例,并使用网络参数启动 resource "alicloud_kms_instance" "default" { # 软件密钥管理实例 product_version = "3" vpc_id = alicloud_vpc.vpc.id # 规定 KMS 实例所在的可用区,使用前面获取的可用区 ID zone_ids = [ "cn-heyuan-a", "cn-heyuan-b", ] # 交换机id vswitch_ids = [ alicloud_vswitch.vsw.id,alicloud_vswitch.vsw1.id ] # 计算性能、密钥数量、凭据数量、访问管理数量 vpc_num = "1" key_num = "1000" secret_num = "100" spec = "1000" # 为KMS实例关联其他VPC,可选参数 # 如果VPC与KMS实例的VPC属于不同阿里云账号,您需要先共享交换机。 #bind_vpcs { #vpc_id = "vpc-j6cy0l32yz9ttxfy6****" #vswitch_id = "vsw-j6cv7rd1nz8x13ram****" #region_id = "cn-shanghai" #vpc_owner_id = "119285303511****" #} #bind_vpcs { #vpc_id = "vpc-j6cy0l32yz9ttd7g3****" #vswitch_id = "vsw-3h4yrd1nz8x13ram****" #region_id = "cn-shanghai" #vpc_owner_id = "119285303511****" #} } # 保存KMS实例CA证书到本地文件 resource "local_file" "ca_certificate_chain_pem" { content = alicloud_kms_instance.default.ca_certificate_chain_pem filename = "ca.pem" }KMS实例中创建密钥:
#密钥规格为Aliyun_AES_256,密钥用途是加密解密(ENCRYPT/DECRYPT) resource "alicloud_kms_key" "kms_software_key_encrypt_decrypt" { description = "default_key_encrypt_decrypt description" # 密钥的使用方式。默认值:ENCRYPT/DECRYPT。有效值:ENCRYPT/DECRYPT: 加密或解密数据。 key_usage = "ENCRYPT/DECRYPT" # 密钥的规格。默认值:Aliyun_AES_256。 key_spec = "Aliyun_AES_256" # KMS 实例的 ID。 dkms_instance_id = alicloud_kms_instance.default.id pending_window_in_days = 7 # 要分配给资源的标签映射,可选 # tags = { # "Environment" = "Production" # "Name" = "KMS-01" # "SupportTeam" = "PlatformEngineering" # "Contact" = "ali***@test.com" # } } #密钥别名为alias/kms_software_key_encrypt_decrypt,在整个阿里云账号下唯一。 resource "alicloud_kms_alias" "kms_software_key_encrypt_decrypt_alias" { # 别名 alias_name = "alias/kms_software_key_encrypt_decrypt" # 密钥id key_id = alicloud_kms_key.kms_software_key_encrypt_decrypt.id }在
main.tf中增加以下内容,创建凭据。通用凭据
# 创建通用凭据,凭据名称为kms_secret_general1,凭据值为secret_data_kms_secret_general1 resource "alicloud_kms_secret" "kms_secret_general" { # 名称 secret_name = "kms_secret_general1" # 描述 description = "secret_data_kms_secret_general" # 类型 secret_type = "Generic" # 指定是否立即删除。默认值:false。有效值:true,false。 force_delete_without_recovery = true # KMS 实例的 ID。 dkms_instance_id = alicloud_kms_instance.default.id # KMS 密钥的 ID encryption_key_id = alicloud_kms_key.kms_software_key_encrypt_decrypt.id # 版本号 version_id = "v1" # 值的类型。默认值:text。有效值:text,binary。 secret_data_type = "text" # 数据 secret_data = "secret_data_kms_secret_general1" }RAM凭据
# 创建RAM凭据示例 # 前提条件是您创建需要托管RAM凭据的RAM用户和AccessKey。 # 共分为2个步骤。 # 步骤1:授予KMS管理RAM用户的Accesskey的权限 # 1.1 创建自定义权限策略AliyunKMSManagedRAMCrendentialsRolePolicy resource "alicloud_ram_policy" "AliyunKMSManagedRAMCrendentialsRolePolicy" { policy_name = "AliyunKMSManagedRAMCrendentialsRolePolicy" policy_document = <<EOF { "Version": "1", "Statement": [ { "Effect": "Allow", "Action": [ "ram:ListAccessKeys", "ram:CreateAccessKey", "ram:DeleteAccessKey", "ram:UpdateAccessKey" ], "Resource": "*" } ] } EOF description = "AliyunKMSManagedRAMCrendentialsRolePolicy" force = true } # 1.2 创建RAM角色AliyunKMSManagedRAMCrendentialsRole resource "alicloud_ram_role" "AliyunKMSManagedRAMCrendentialsRole" { name = "AliyunKMSManagedRAMCrendentialsRole" description = "AliyunKMSManagedRAMCrendentialsRole" document = <<EOF { "Statement": [ { "Action": "sts:AssumeRole", "Effect": "Allow", "Principal": { "Service": [ "kms.aliyuncs.com" ] } } ], "Version": "1" } EOF force = true } # 1.3 为RAM角色AliyunKMSManagedRAMCrendentialsRole授权AliyunKMSManagedRAMCrendentialsRolePolicy resource "alicloud_ram_role_policy_attachment" "attach" { policy_name = alicloud_ram_policy.AliyunKMSManagedRAMCrendentialsRolePolicy.policy_name policy_type = alicloud_ram_policy.AliyunKMSManagedRAMCrendentialsRolePolicy.type role_name = alicloud_ram_role.AliyunKMSManagedRAMCrendentialsRole.name } # 步骤2:创建RAM凭据 resource "alicloud_kms_secret" "kms_secret_RAMCredentials" { # 凭据名称 secret_name = "my_secret" # 描述 description = "secret_kms_secret_RAMCredentials" # 凭据的类型 secret_type = "RAMCredentials" # KMS实例ID dkms_instance_id = alicloud_kms_instance.default.id # 用于加密凭据值的密钥ID。 encryption_key_id = alicloud_kms_key.kms_software_key_encrypt_decrypt.id # 是否立即删除一个凭据。默认值:false。有效值:true,false。 force_delete_without_recovery = true # 指定是否启用自动轮换。默认值:false。有效值:true,false。 enable_automatic_rotation = true # 自动轮换的间隔。 rotation_interval = "7d" # 扩展配置。替换为您的UserName extended_config = "{\"SecretSubType\":\"RamUserAccessKey\", \"UserName\":\"testuser\"}" # 版本 version_id = "V1" # 凭据值的类型。默认值:文本。有效值:文本,二进制。 secret_data_type ="text" # 数据 secret_data = "{\"AccessKeys\":[{\"AccessKeyId\":\"LTAI****************\",\"AccessKeySecret\":\"yourAccessKeySecret\"}]}" }RDS凭据
以“双账号托管”方式为例介绍如何创建RDS凭据。
variable "region" { default = "cn-hangzhou" } provider "alicloud" { region = var.region } variable "zone_id" { default = "cn-hangzhou-b" } variable "instance_type" { default = "pg.n2.2c.2m" } # 创建VPC resource "alicloud_vpc" "main" { vpc_name = "alicloud" cidr_block = "172.16.0.0/16" } # 创建交换机 resource "alicloud_vswitch" "main" { vpc_id = alicloud_vpc.main.id cidr_block = "172.16.192.0/20" zone_id = var.zone_id depends_on = [alicloud_vpc.main] } # 创建RDS PostgreSQL实例 resource "alicloud_db_instance" "instance" { engine = "PostgreSQL" engine_version = "13.0" instance_type = var.instance_type instance_storage = "30" instance_charge_type = "Postpaid" vswitch_id = alicloud_vswitch.main.id } # 创建RDS凭据 resource "alicloud_kms_secret" "kms_secret_RDS_MYSQL" { # 凭据名称 secret_name = "rds_secret/${alicloud_db_instance.id}" # 类型 secret_type = "Rds" # KMS实例ID dkms_instance_id = alicloud_kms_instance.default.id # 用于加密凭据值的密钥ID。 encryption_key_id = alicloud_kms_key.kms_software_key_encrypt_decrypt.id # 指定是否启用自动轮换。默认值:false。有效值:true,false。 enable_automatic_rotation = true # 自动轮换的间隔。 rotation_interval = "7d" # 指定是否立即删除。默认值:false。有效值:true,false。 force_delete_without_recovery = true # 配置 extended_config = "{\"SecretSubType\":\"DoubleUsers\", \"DBInstanceId\":\"rm-7xv1450tq4pj4****\" ,\"CustomData\": {}}" # 版本 version_id = "V1" # 凭据值的类型。默认值:文本。有效值:文本,二进制。 secret_data_type = "text" # 数据 secret_data = "{\"Accounts\":[{\"AccountName\":\"rdsuser1\",\"AccountPassword\":\"Admin****\"},{\"AccountName\":\"rdsuser2\",\"AccountPassword\":\"Admin****\"}]}" }
执行以下命令,初始化
Terraform运行环境。terraform initTerraform has created a lock file .terraform.lock.hcl to record the provider selections it made above. Include this file in your version control repository so that Terraform can guarantee to make the same selections by default when you run "terraform init" in the future. Terraform has been successfully initialized! You may now begin working with Terraform. Try running "terraform plan" to see any changes that are required for your infrastructure. All Terraform commands should now work. If you ever set or change modules or backend configuration for Terraform, rerun this command to reinitialize your working directory. If you forget, other commands will detect it and remind you to do so if necessary.创建执行计划,并预览变更。
terraform plan执行以下命令,创建通用凭据。
terraform apply在执行过程中,根据提示输入
yes并按下Enter键,等待命令执行完成,若出现以下信息,则表示通用凭据创建成功。Do you want to perform these actions? Terraform will perform the actions described above. Only 'yes' will be accepted to approve. Enter a value: yes ... alicloud_kms_key.kms_software_key_encrypt_decrypt: Creation complete after 0s [id=key-shh6715c21812y8i7z***] alicloud_kms_alias.kms_software_key_encrypt_decrypt_alias: Creating... alicloud_kms_secret.kms_secret_general: Creating... alicloud_kms_alias.kms_software_key_encrypt_decrypt_alias: Creation complete after 0s [id=alias/kms_secret] alicloud_kms_secret.kms_secret_general: Creation complete after 1s [id=kms_secret_general1] ... Apply complete! Resources: 2 added, 0 changed, 0 destroyed.验证结果
执行terraform show命令
您可以使用以下命令查询Terraform已创建的资源详细信息:
terraform show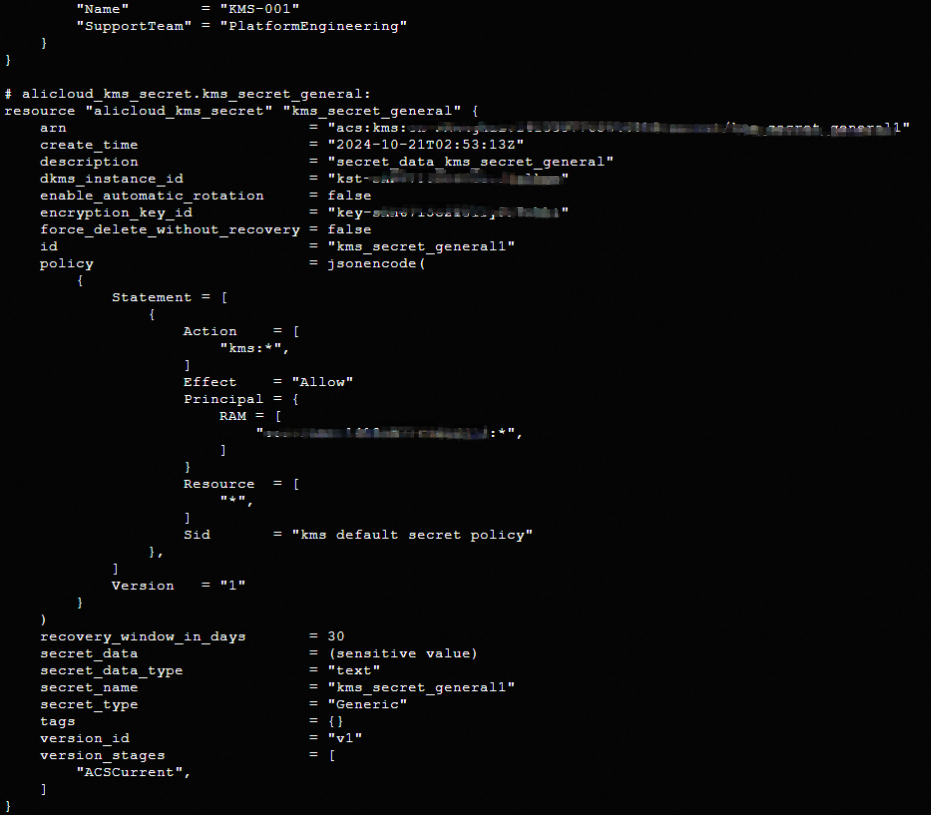
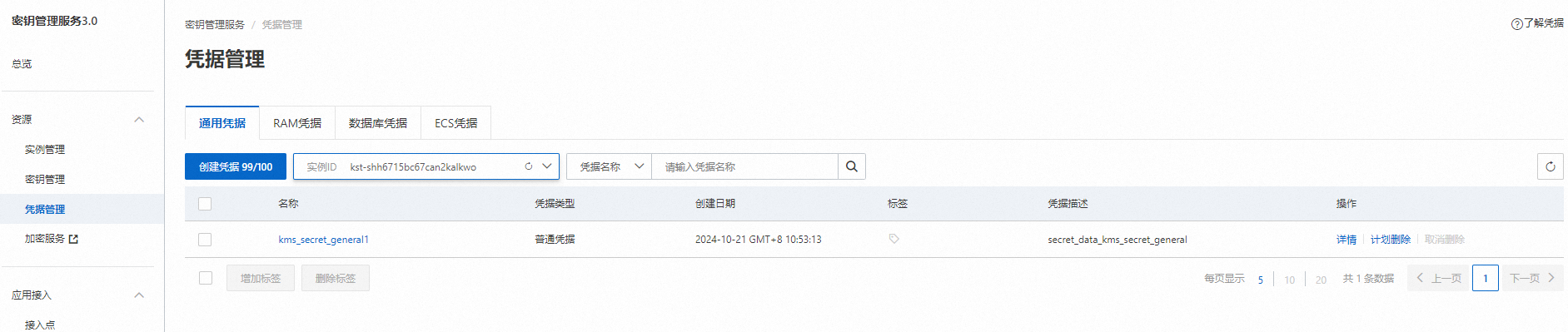
登录密钥管理服务控制台
登录密钥管理服务控制台,查看已创建的凭据。
清理资源
当您不再需要上述通过Terraform创建或管理的资源时,请运行以下命令以释放资源。关于terraform destroy的更多信息,请参见Terraform常用命令。
terraform destroy完整示例
当前示例代码支持一键运行,您可以直接运行代码。一键运行
