本文汇总了使用数据灾备(DBS)时,产生的一些常见问题的处理方式以及解答。
计费常见问题
如果购买了DBS备份计划,后续可能会产生哪些计费项?
备份计划规格费用:您需要在购买包年包月备份计划时支付规格费用。不同的备份计划规格提供不同的备份性能(备份、恢复速度)、免费数据量额度以及收费标准,规格费用详情,请参见规格费用。
备份计划存储费用(可选):配置包年包月备份计划时,当备份目标存储类型选择为DBS内置存储,系统将根据存入DBS内置存储中的实际数据量的大小与时长收取存储费用。费用详情,请参见存储费用。
备份计划备份费用(可选):若备份计划备份的数据超过当前规格的免费额度时,DBS会根据超出的备份数据量进行计费。各规格备份计划的免费数据量额度以及超出部分收费标准,请参见备份费用。
DBS沙箱费用(可选):DBS支持创建用于自建MySQL应急恢复的沙箱实例功能。
开启沙箱功能后,DBS会根据沙箱存储中的数据量产生沙箱存储费用。
创建沙箱实例后,DBS会根据沙箱实例规格及使用时长产生沙箱实例费用。费用详情,请参见计费项。
不支持直接创建按量付费的备份计划。
DBS存储包和DBS网络包可以抵扣哪些计费项?
DBS存储包
DBS提供如下三种存储包类型,同时提供多种规格(100 GB、500 GB、1 TB、500 TB等)、多种时长(1个月、6个月、1年等)的存储包供您选择。若您的存储容量超出购买的存储包限额,超出部分将以按量付费的形式进行收费。
存储包类型 | 抵扣对象 |
云数据库备份存储包 |
|
CDM沙箱存储包 | 用于抵扣同一账号下开启CDM沙箱功能的存储费用。有关沙箱存储费用,请参见沙箱费用。 |
备份实例存储包 | 用于抵扣同一账号下DBS备份计划实例的内置存储费用。更多信息,请参见内置存储与用户OSS。 |
DBS网络包
抵扣对象 | 说明 |
跨地域备份网络用量 | DBS网络包当前全球地域通用,您可在购买后用于抵扣不同地域的RDS MySQL、RDS PostgreSQL、RDS SQL Server、PolarDB MySQL版、PolarDB PostgreSQL版和MongoDB跨地域备份网络费用,具体将根据不同地域以不同的系数进行抵扣。 |
下载备份集网络用量 | DBS网络包当前全球地域通用,您可在购买后用于抵扣不同地域RDS MySQL、RDS PostgreSQL、RDS SQL Server下载备份集所产生的网络费用,具体将根据不同地域以不同的系数进行抵扣。 |
按量付费和包年包月的备份计划不使用也会收费吗?
按量付费和包年包月的备份计划即使不使用(备份计划已不再产生新的备份集),历史备份集也会一直占用存储资源,所以仍然会收取存储费用。
按量付费(后付费):若长期不使用按量付费备份计划,建议您在保存数据并下载备份集后释放该备份计划,释放后将不会再产生备份费用和存储费用。具体操作,请参见释放或退订备份计划。
包年包月(预付费):若长期不使用包年包月备份计划,但期望:
系统能保留历史备份集,但无需产生新的备份集。建议您可以暂停或重启备份计划,暂停后不再产生备份费用,但存储类型为DBS内置存储的包年包月备份计划仍然会产生存储费用。
系统无需保留历史备份集,并且无需产生新的备份集。您可退订包年包月备份计划,退订后将不会有备份费用和存储费用产生。
处于运行中的包年包月备份计划暂停后,备份计划购买时长不会受到影响。
仅包年包月备份计划的存储类型为DBS内置存储时,会产生存储费用。
包年包月和按量付费可以互相转换吗?
暂不支持互相转换。
按量付费的备份计划可以释放吗?
可以释放。详情请参见释放备份计划。
包年包月的备份计划可以释放吗?
包年包月备份计划不支持释放。
数据灾备(DBS)不支持退订,老用户DBS备份计划支持退订。
详情请参见退款说明。
DBS存储包或DBS网络包到期后有什么影响?
DBS存储包和DBS网络包是DBS推出的一种预付费资源包。到期后将会自动失效,后续无法用于抵扣存储费用或网络费用,不影响备份计划以及已有备份数据。
备份计划到期或者欠费有什么影响?
详情请参见到期、欠费说明。
如何减少包年包月DBS备份计划的费用?
购买DBS存储包抵扣同一账号下DBS备份计划的内置存储费用。更多详情,请参见内置存储与用户OSS。
没有使用过DBS控制台的备份服务,账单中出现的数据库备份DBS的计费项是什么?
云数据库RDS、云原生数据库PolarDB、云数据库MongoDB、云数据库Redis、云原生内存数据库Tair、云原生数据仓库AnalyticDB for PostgreSQL产品的备份恢复功能均由DBS提供,您可确认下该备份计费项是否因为您使用了上述产品的备份恢复服务所产生。更多详情,请参见DBS计费概述。
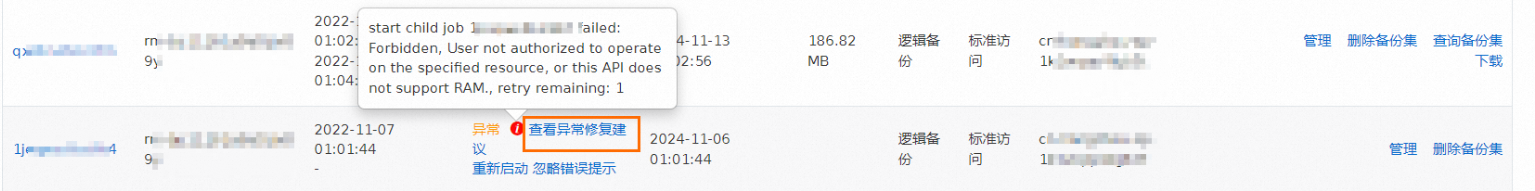
如何修复异常DBS备份计划?
问题描述
备份计划列表页显示DBS备份计划状态异常。
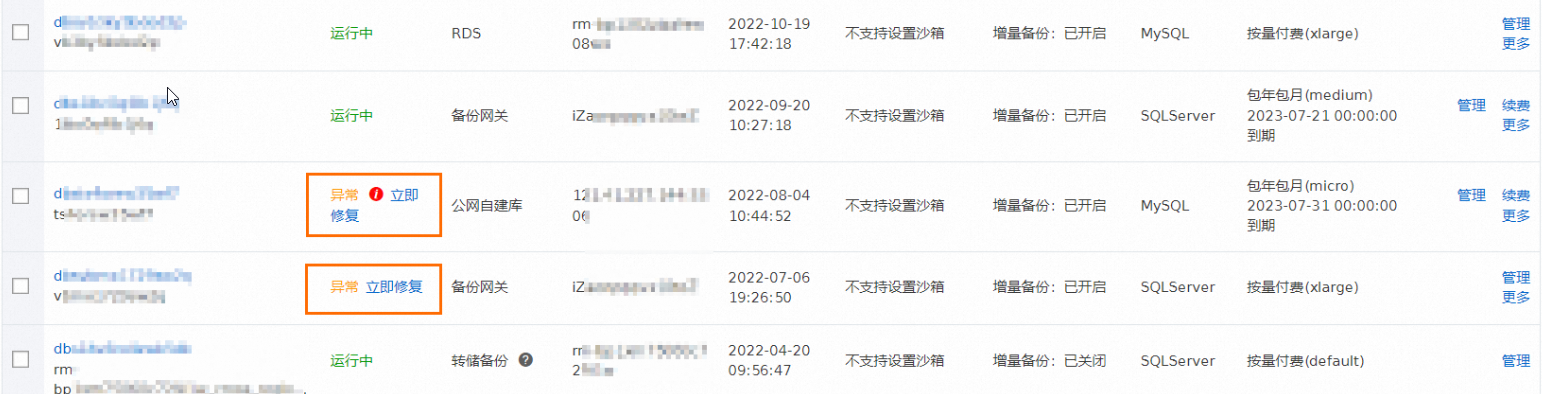
问题原因
DBS备份计划状态显示异常,表示该DBS备份计划下至少存在一个异常任务,通常可能是全量备份任务异常或增量备份任务异常,也可能是其他类型任务出现异常。
任务出现异常时,DBS不会直接启动异常任务,以免影响客户业务。
为了确保您的业务正常进行,备份计划出现异常时,建议您及时排查问题原因。如果参考本文提供的解决方案后仍无法解决问题,请到DBS客户咨询群(钉钉群号:35585947)进行咨询。
解决方案
针对异常的备份任务,DBS提供如下几种解决方案供您参考。
场景及解决方案 | 注意事项 |
若您已确定任务异常的原因,并已成功解决了问题,那么您可以选择单击重新启动来进行修复。 例如备份异常是由于源实例停机导致的,您可以在启动源实例后尝试重启异常任务以解决问题。 |
|
若您已确定任务异常的原因,并已成功解决了问题,那么您可以选择单击忽略错误提示。 例如备份异常是由于客户备份实例关机、服务异常等原因导致,但现已恢复正常,您也可以选择忽略错误提示,下次备份窗口将正常进行备份。 | 若问题已成功修复,忽略操作发起后任务状态将转变为完成。此时如果该备份计划下只有这一条异常任务,那么该备份计划状态会恢复为运行中;如果备份计划仍显示异常,请进一步排查是否存在其他异常任务。 |
若您无法确定异常原因或无法自主确认解决方案,您可以将鼠标停留在感叹号图标上,查看异常信息,并在数据灾备(DBS)常见报错处理文档中搜索异常信息,尝试自行修复。 | 若在常见报错一文中未找到您遇到的异常,或按照文中修复建议仍未解决您的问题,请到DBS客户咨询群(钉钉群号:35585947)进行咨询。 |
操作步骤
单击备份计划状态列下的立即修复,页面将跳转至异常备份任务页面。
若异常任务来源是全量备份任务,则跳转至全量数据备份页;若异常任务来源是增量备份任务,则跳转至增量数据备份页。
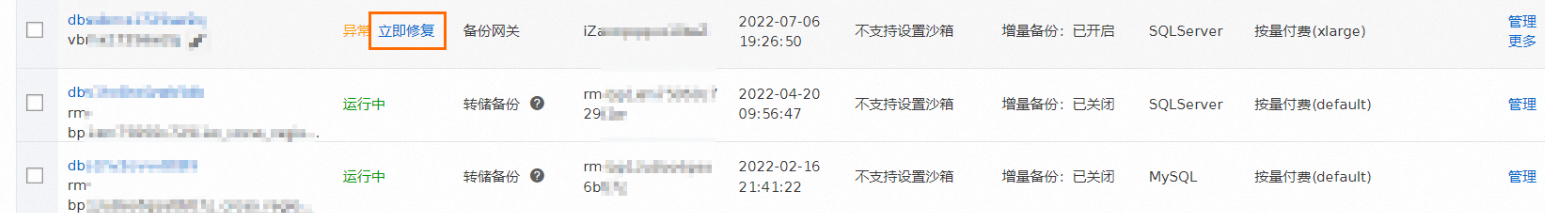
请根据具体的业务异常备份任务,选择适合的解决方案进行修复。
如果您选择重启异常备份任务,请单击重新启动。
说明如果您正在进行全量备份,在重启异常任务前,请注意备份操作对源库的影响,建议您在业务低峰期进行操作。
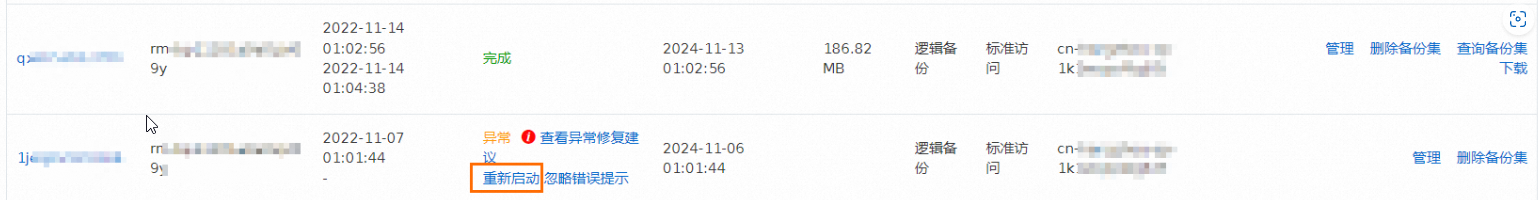
如果您选择忽略异常报错,请单击忽略错误提示。
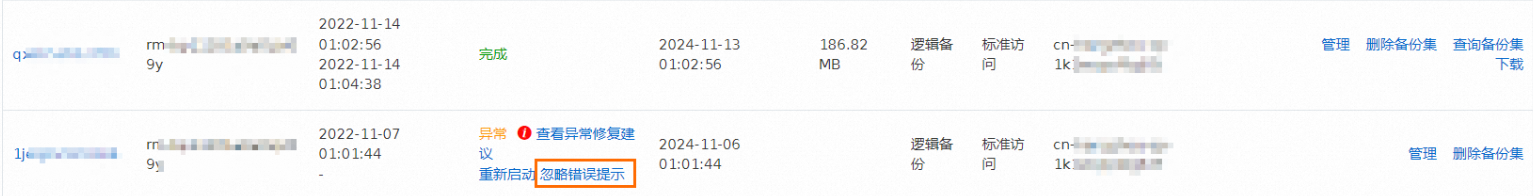
如果您选择自行修复异常的备份任务,可以将鼠标停留在感叹号图标上,查看异常信息。同时请单击查看异常修复建议(异常全量备份任务)或查看增量异常修复建议(异常增量备份任务),页面将跳转至常见报错文档。在该文档中搜索异常信息,并尝试自行修复。
说明若您无法定位异常信息,可能是其他类型任务出现异常,请到DBS客户咨询群(钉钉群号:35585947)进行咨询。
如何开通数据灾备(DBS)服务?
初次使用数据灾备(DBS)时,您需要将角色权限(AliyunDBSDefaultRole)授权给数据灾备(DBS),并开通对象存储OSS,以允许DBS访问、查询和管理您的数据库,并将数据库实时备份到OSS。该授权操作是为了确保数据灾备(DBS)备份恢复服务的正常运行,对数据灾备(DBS)备份实例的性能不产生任何影响。
步骤一:授权数据灾备(DBS)服务关联角色
数据灾备(DBS)服务关联角色(AliyunServiceRoleForDBS)是具备其他云服务访问权限的RAM角色。当数据灾备(DBS)接入您在阿里云购买的云数据库(如RDS、MongoDB、 Redis、PolarDB)或阿里云ECS上自建的数据库时,需通过AliyunServiceRoleForDBS获取访问权限。更多信息,请参见服务关联角色。
初次使用数据灾备(DBS)时,您需要将服务关联角色(AliyunServiceRoleForDBS)授权给数据灾备(DBS)。权限详情,请参见附录:AliyunServiceRoleForDBS介绍。
- 登录数据管理DMS 5.0。
在顶部菜单栏中,选择安全与规范(DBS) > 数据灾备(DBS) > 灾备数据源。
说明若您使用的是极简模式的控制台,请单击控制台左上角的
 图标,选择全部功能 > 安全与规范(DBS) > 数据灾备(DBS) > 灾备数据源。
图标,选择全部功能 > 安全与规范(DBS) > 数据灾备(DBS) > 灾备数据源。在弹出的提示对话框中,单击授权DBS服务关联角色。
说明若登录数据灾备(DBS)控制台后,没有弹出提示授权的对话框,则无需执行本文后续操作,您可以开始创建备份。具体操作,请参见通过灾备数据源管理备份或通过备份计划列表创建备份。
单击确定。
此时,您已创建数据灾备(DBS)服务关联角色(AliyunServiceRoleForDBS),若您需要删除服务关联角色(AliyunServiceRoleForDBS),请参见删除RAM角色。
步骤二:开通对象存储OSS
开通对象存储OSS不会产生费用。开通后,您使用数据灾备(DBS)进行备份时,数据灾备(DBS)才能将备份数据存入OSS(云存储)中。
登录数据管理DMS 5.0。
在顶部菜单栏中,选择安全与规范(DBS) > 数据灾备(DBS) > 备份计划。
说明若您使用的是极简模式的控制台,请单击控制台左上角的
 图标,选择全部功能 > 安全与规范(DBS) > 数据灾备(DBS) > 备份计划。
图标,选择全部功能 > 安全与规范(DBS) > 数据灾备(DBS) > 备份计划。在弹出的提示对话框中,单击立即开通使用OSS。
在弹出的对话框中,单击立即开通。
在对象存储OSS页面,阅读并勾选服务协议,单击立即开通。
至此,您已开通数据灾备(DBS)服务。
附录:AliyunServiceRoleForDBS介绍
角色名称:AliyunServiceRoleForDBS
角色权限策略:AliyunServiceRolePolicyForDBS
权限说明:
{
"Version": "1",
"Statement": [
{
"Action": [
"rds:DescribeDBInstanceNetInfo",
"rds:DescribeDBInstanceNetInfoForChannel",
"rds:DescribeTasks",
"rds:DescribeDBInstances",
"rds:DescribeFilesForSQLServer",
"rds:DescribeImportsForSQLServer",
"rds:DescribeSlowLogRecords",
"rds:DescribeBinlogFiles",
"rds:DescribeSQLLogRecords",
"rds:DescribeParameters",
"rds:DescribeParameterTemplates",
"rds:DescribeDBInstanceAttribute",
"rds:DescribeDatabases",
"rds:DescribeAccounts",
"rds:DescribeSecurityIPList",
"rds:DescribeSecurityIps",
"rds:DescribeDBInstanceIPArray",
"rds:DescribeDBInstanceIPArrayList",
"rds:DescribeDBInstanceSSL",
"rds:DescribeDBInstanceTDE",
"rds:CreateDBInstance",
"rds:CreateAccount",
"rds:CreateDatabase",
"rds:ModifySecurityIps",
"rds:GrantAccountPrivilege",
"rds:CreateMigrateTask",
"rds:CreateOnlineDatabaseTask",
"rds:DescribeMigrateTasks",
"rds:DescribeOssDownloads",
"rds:CreateBackup",
"rds:DescribeBackups",
"rds:DescribeBackupPolicy",
"rds:ModifyBackupPolicy",
"rds:DescribeBackupTasks",
"rds:DescribeBinlogFiles"
],
"Resource": "*",
"Effect": "Allow"
},
{
"Action": [
"ecs:DescribeInstance",
"ecs:DescribeInstances",
"ecs:DescribeVpcs",
"ecs:DescribeSecurityGroups",
"ecs:DescribeSecurityGroupAttribute",
"ecs:AuthorizeSecurityGroup",
"ecs:JoinSecurityGroup",
"ecs:RevokerSecurityGroup"
],
"Resource": "*",
"Effect": "Allow"
},
{
"Action": [
"kms:ListKeys"
],
"Resource": "*",
"Effect": "Allow"
},
{
"Action": [
"cms:PutEventRule",
"cms:PutEventTargets",
"cms:ListEventRules",
"cms:ListEventTargetsByRule",
"cms:DeleteEventRule",
"cms:DeleteEventTargets"
],
"Resource": "*",
"Effect": "Allow"
},
{
"Action": [
"polardb:DescribeDBClusterIPArrayList",
"polardb:DescribeDBClusterNetInfo",
"polardb:DescribeDBClusters",
"polardb:ModifySecurityIps",
"polardb:DescribeDBClusterEndpoints",
"polardb:DescribeDBClusterAccessWhitelist",
"polardb:ModifyDBClusterAccessWhitelist"
],
"Resource": "*",
"Effect": "Allow"
},
{
"Action": [
"dds:DescribeDBInstanceAttribute",
"dds:DescribeReplicaSetRole",
"dds:DescribeSecurityIps",
"dds:DescribeDBInstances",
"dds:ModifySecurityIps"
],
"Resource": "*",
"Effect": "Allow"
},
{
"Action": [
"kvstore:DescribeSecurityIps",
"kvstore:DescribeInstances",
"kvstore:DescribeAccounts",
"kvstore:DescribeDBInstanceNetInfo",
"kvstore:CreateAccount",
"kvstore:ModifySecurityIps",
"kvstore:DescribeInstanceAttribute",
"kvstore:AllocateInstancePrivateConnection",
"kvstore:DescribeLogicInstanceTopology"
],
"Resource": "*",
"Effect": "Allow"
},
{
"Action": [
"drds:DescribeDrdsDB",
"drds:DescribeDrdsDBs",
"drds:DescribeDrdsDbInstance",
"drds:DescribeDrdsDbInstances",
"drds:DescribeDrdsDBIpWhiteList",
"drds:DescribeDrdsInstances",
"drds:ModifyDrdsIpWhiteList",
"drds:CreateDrdsDB",
"drds:DescribeTable",
"drds:DescribeTables",
"drds:ModifyRdsReadWeight",
"drds:ChangeAccountPassword",
"drds:CreateDrdsInstance",
"drds:CreateInstanceAccount",
"drds:CreateInstanceInternetAddress",
"drds:DescribeInstanceAccounts"
],
"Resource": "*",
"Effect": "Allow"
},
{
"Action": [
"vpc:DescribeVpcs"
],
"Resource": "*",
"Effect": "Allow"
},
{
"Action": [
"bssapi:QueryResourcePackageInstances"
],
"Resource": "*",
"Effect": "Allow"
},
{
"Action": "hdm:AddHDMInstance",
"Resource": "*",
"Effect": "Allow"
},
{
"Action": "ram:DeleteServiceLinkedRole",
"Resource": "*",
"Effect": "Allow",
"Condition": {
"StringEquals": {
"ram:ServiceName": "dbs.aliyuncs.com"
}
}
}
]
}账号权限说明
MySQL账号权限
功能类型 | 权限要求 |
备份 |
|
恢复 | SELECT、INSERT、UPDATE、DELETE、CREATE、DROP、INDEX、ALTER、CREATE VIEW、SHOW VIEW、CREATE ROUTINE、ALTER ROUTINE、EVENT、TRIGGER。 |
在MySQL数据库中进行增量备份操作需要使用
show binary logs语句,MySQL 5.5.24及以前版本需要具备super权限的账号才能执行。但从MySQL 5.5.25版本开始,只需要具备REPLICATION CLIENT权限的账号就可以执行该语句。对于RDS数据库备份和恢复的不同需求,需要使用不同权限的账号来进行操作,只读权限账号可以满足备份要求,读写权限账号可以满足备份和恢复的要求。
SQL Server账号权限
功能类型 | 权限要求 |
备份 | SELECT、VIEW DEFINITION |
恢复 | SELECT、INSERT、ALTER Database、REFERENCES、VIEW DEFINITION |
PostgreSQL账号权限
功能类型 | 权限要求 |
备份 | SELECT或SUPER角色 |
恢复 | CREATE、INSERT、USAGE、REFERENCES、TRIGGER |
如何实现恢复数据一致性?
针对逻辑备份方式,为了尽可能降低对数据库性能的影响,数据灾备(DBS)在全量备份过程中采用无锁备份方式,并行拉取数据并备份到对象存储服务(OSS)上,全量备份会产生不同时间点的数据备份,在恢复数据时,先恢复全量备份数据,然后恢复增量备份数据,通过增量备份的幂等性来实现恢复数据的一致性。
增量备份 | 恢复数据一致性 |
已开启 | 支持 |
未开启 | 不支持 |
如何管理生命周期?
生命周期说明
备份集的生命周期范围为7天到3650天(10年),数据灾备(DBS)会自动清理符合条件的过期备份集,无需用户干预。
根据过期备份集的清理策略,当备份计划的全量备份集数量大于3个时(不包括3个),数据灾备(DBS)会自动删除过期的全量备份集和增量备份集。如果未满足该条件,备份集清理机制将不会被触发。
修改并应用生命周期
具体操作,请参见修改备份计划内的备份策略或修改备份生命周期。
相关操作
查看备份大小以及减少数据备份的方法,请参见删除或减少备份。
常见问题
Q:我的备份计划的生命周期设置为了7天,但为什么到期后备份集没有被删除?
A:当备份计划的全量备份集数量小于等于3个,备份集的清理策略将不会被触发,因此过期备份集不会被自动删除。
Q:备份集生命周期已经过期了,但为什么增量备份还占用存储空间?
A:可能是用户此前手动删除了全量备份集,导致全量备份集数量小于等于3个,清理策略未成功触发。具体详情,请参见生命周期说明。
什么是备份数据量?
备份数据量,是指通过DBS备份链路的数据量。
常见概念
在数据库备份场景下,有4个概念:数据库磁盘空间、数据文件空间、备份数据量、存储数据量。
| 数据量 | 说明 |
| 数据库磁盘空间 | 由数据库的数据文件空间、数据库的日志文件空间、操作系统文件空间和空闲空间组成。 说明
|
| 数据文件空间 | 数据库的数据文件在服务器上占用磁盘空间。 如何查看数据文件大小:
|
| 备份数据量 | 通过备份链路的实际数据大小,与数据文件空间不同,备份数据量取决于数据库类型、备份方式、备份粒度等因素。 |
| 存储数据量 | 存放存储介质的实际数据大小,与备份数据量不同,存储数据量取决于备份数据量、备份数据存储格式、压缩算法等因素。 |
空间大小:数据库磁盘空间(RDS/ECS)> 数据文件空间(实际使用)> 备份数据量(DBS)> 存储数据量(内置存储)。
综上所述,您可通过调整DBS提供的备份粒度、备份周期等方法降低备份数据量,进而降低数据灾备(DBS)费用;您也可通过数据灾备(DBS)提供的紧凑存储格式、压缩、自动转存清理策略降低存储数据量,进而降低OSS费用。
如何查看备份使用量?
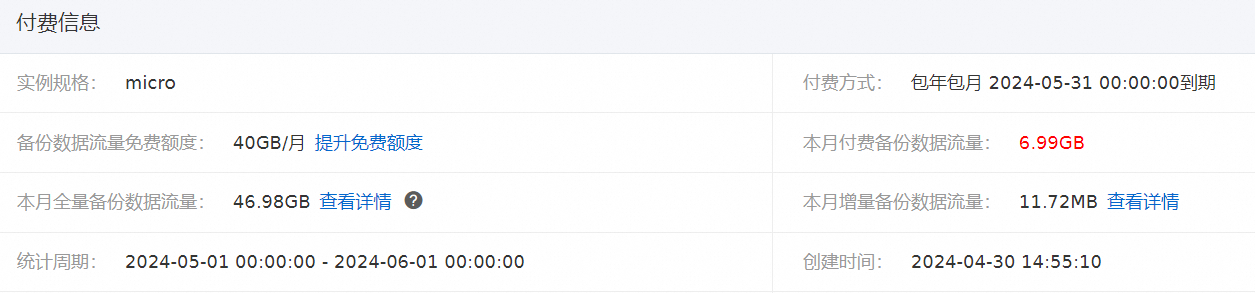
单击目标备份计划操作列下的管理。
您可以在付费信息模块,查看实际备份数据量。
字段名称
说明
实例规格
DBS支持多种规格:serverless、micro、small、medium、large、xlarge。更多详情,请参见如何选择备份计划规格。
付费方式
DBS支持按量计费和包年包月(预付费)两种计费方式。更多详情,请参见计费项。
备份数据流量免费额度
不同的规格提供不同的免费数据量额度、收费标准以及备份与恢复性能(备份恢复的速度)。更多信息,请参见计费项。
本月付费备份数据流量
超出免费额度部分,需要额外付费,规格越高,备份恢复的性能越好且单价越低。
本月全量备份数据流量
全量备份任务累计的备份数据量。
本月增量备份数据流量
增量备份任务累计的备份数据量。
统计周期
按照自然月统计。
创建时间
备份计划的创建时间。
如何修改备份源数据库?
使用场景
原数据库迁移或下线,需切换为新数据库备份。
测试阶段结束,需切换为生产数据库备份。
源账号密码配置错误获取权限不足,需要修改账号密码。
源数据库的库表发生变动,需要重新配置备份对象。
操作步骤
修改数据库账号及密码/备份数据库对象
前提条件
备份实例的备份方式为逻辑备份。
备份源实例的数据库账号必须具备数据备份和恢复的权限。更多详情,请参见账号权限说明。
操作步骤
单击目标备份计划操作列的管理,进入备份任务配置页面。
单击基本信息区域的备份源设置。各数据库的备份源设置详情,请参见配置备份计划及恢复数据。
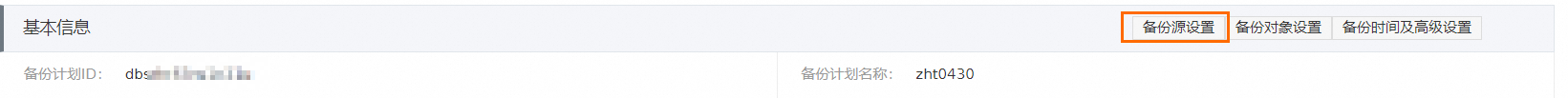
设置待修改的备份源信息,测试通过后单击下一步。
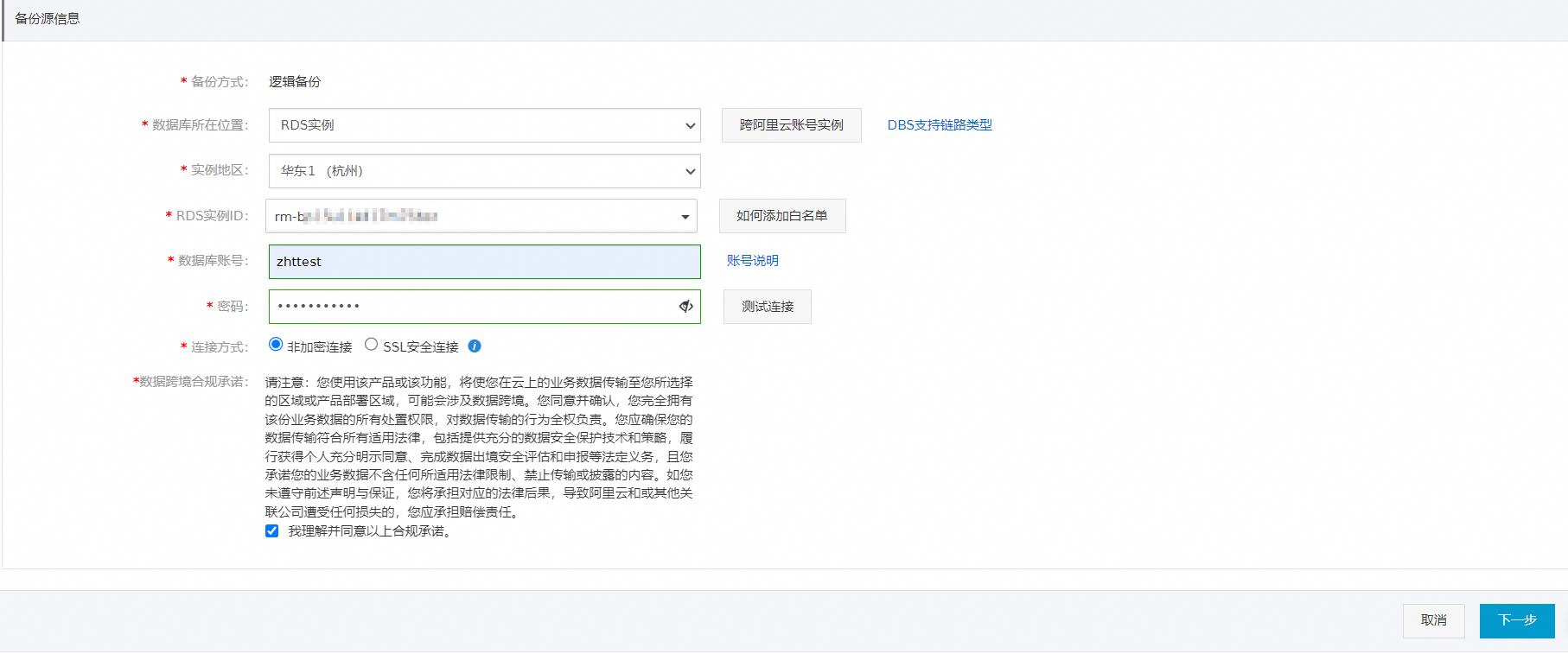
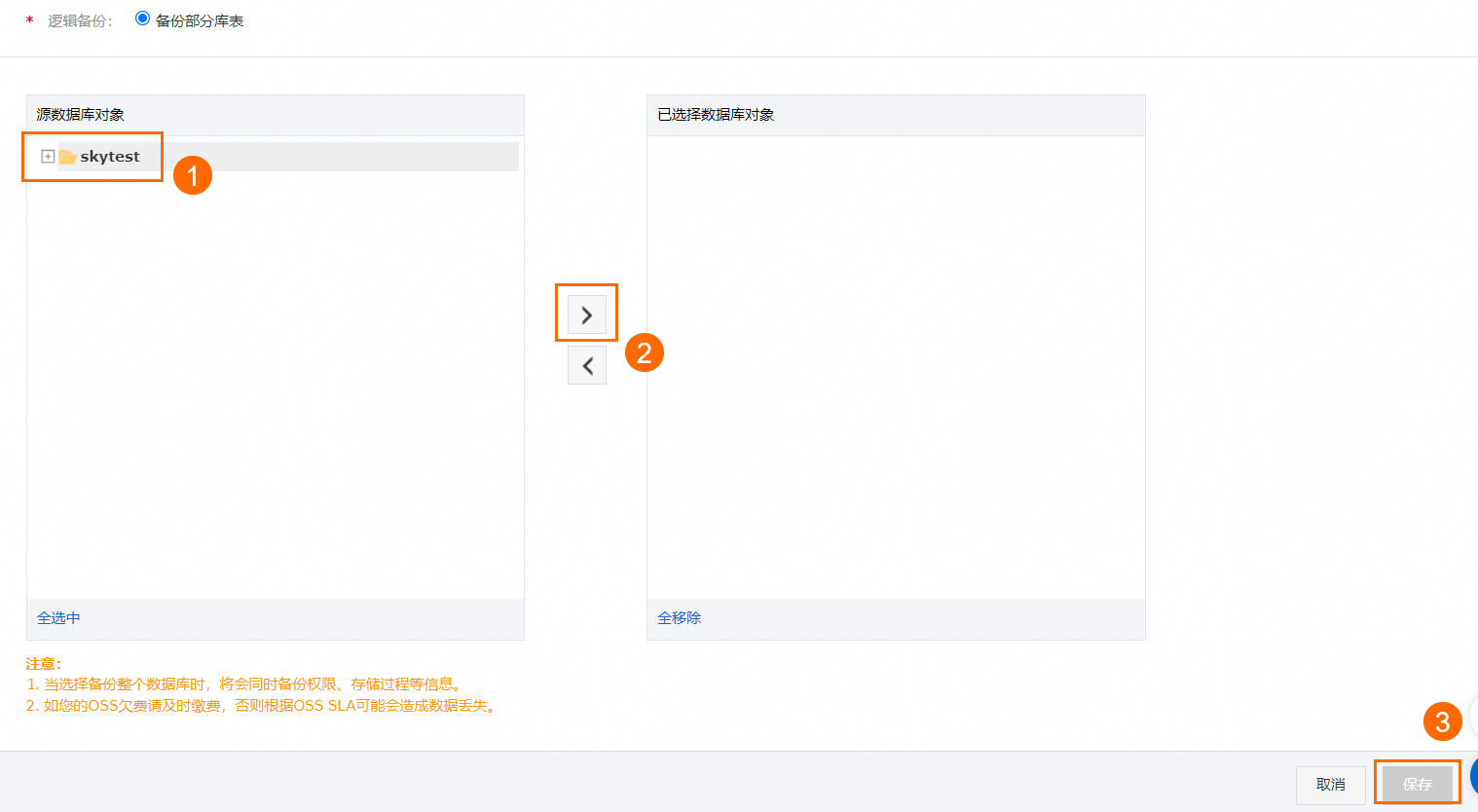
设置待备份的数据库对象,并单击保存。
添加新的源数据库:在左侧源数据库对象区域中选择目标数据库,并单击
 。
。删除此前已选择的数据库:在右侧已选择数据库对象区域中选择目标数据库,并单击
 。
。
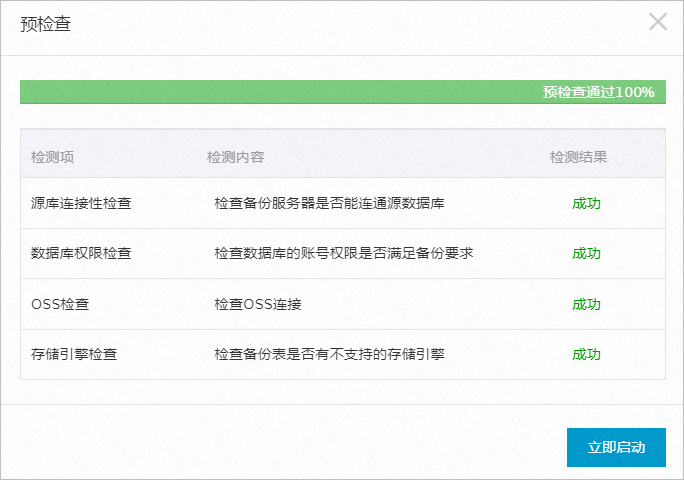
等待预检查通过后,单击立即启动,新备份配置将修改成功。
 说明
说明单击立即启动后,如果原备份计划有运行中增量备份任务,该增量任务会被置为完成,并使用新账号和密码重新调度发起一个新的增量备份任务。
如果当前没有运行中的全量备份任务,此时系统会立即发起一次全量备份任务。请注意对源库影响,建议您在业务低峰修改配置。
如果当前存在运行中的全量备份任务,本次备份任务的配置不会被更新,到下次调度全量任务或者下次发起全量备份任务时才会使用新的配置信息进行备份。
仅修改备份数据库对象
单击目标备份计划操作列的管理,进入备份任务配置页面。
单击基本信息区域的备份对象设置。
修改备份对象,并单击保存。
添加新的源数据库:在左侧源数据库对象区域中选择目标数据库,并单击
 。
。删除此前已选择的数据库:在右侧已选择数据库对象区域中选择目标数据库,并单击
 。
。
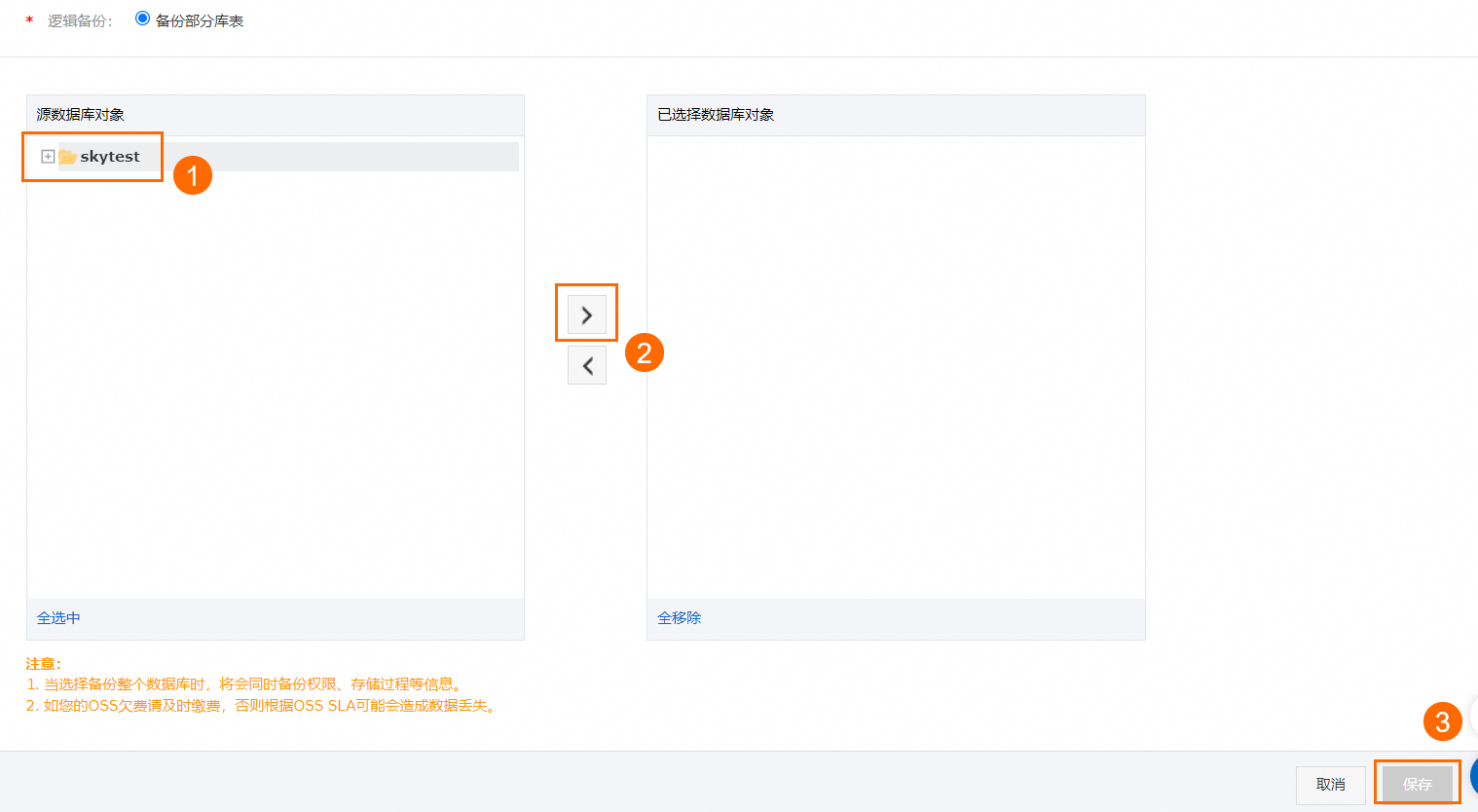
在弹出的发起全量备份对话框中,单击确定或关闭。
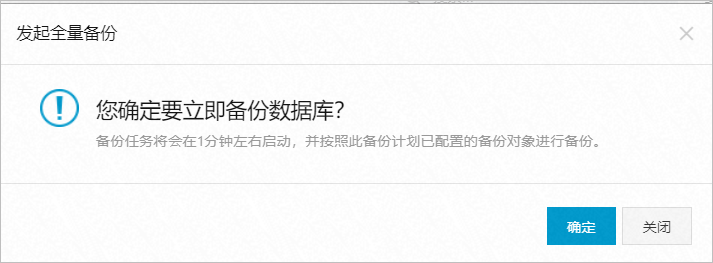
单击确定:备份任务将会在1分钟左右启动,并按照此备份计划已配置的备份对象进行备份。请注意对源库的影响,建议您选择业务低峰期进行该操作。
单击关闭:本次配置系统默认会修改成功,但不会立即发起一次全量备份,等到下次调度时系统将按照最新的配置进行备份。
什么是RDS跨地域备份产生的转储备份计划?
当您在RDS控制台中开启跨地域备份功能时,数据灾备(DBS)会通过专线将RDS实例(RDS MySQL、RDS SQL Server、RDS PostgreSQL)的数据进行跨地域传输与备份,并在数据灾备(DBS)控制台中新增一条转储备份计划,您可以在转储备份计划详情页面查看源数据库信息。
RDS跨地域备份功能详情及计费说明,请参见:
常见问题
Q:如何关闭转储备份?
A:在RDS控制台关闭跨地域备份功能后,数据灾备(DBS)会自动关闭对应的转储备份计划。
Q:为什么关闭跨地域备份后还会扣费?
A:关闭跨地域备份之后,不会再收取流量费,也不会再产生新的备份,但已备份的数据不会马上删除,备份数据有至少保留7天的策略。您可以设置保留时间为7天,待7天后跨地域备份文件全部自动清除,就不会再收取跨地域备份的存储费用。
Q:转储备份的付费方式能否切换为包年包月?
A:转储备份计划的付费方式默认为按量付费,暂不支持切换为包年包月。
Q:RDS控制台关闭跨地域备份后,为什么在数据灾备(DBS)控制台还有转储备份计划?
A:暂时不会在数据灾备(DBS)控制台删除转储备份计划,但不会产生费用。
备份会对数据库产生什么影响?
数据灾备(DBS)对数据库执行备份时会造成一定影响,建议选择业务低峰期执行备份任务。
备份原理与影响
类目 | 逻辑备份 | 物理备份 |
全量备份原理 | 对每张表数据进行切分,然后在数据库上执行SQL语句,多线程并行读取数据。 | 在数据库所在服务器上安装DBS备份网关,然后通过备份网关将数据库文件进行备份(拷贝)。 |
增量备份原理 | 支持实时捕获数据库内存中的日志,实现实时增量备份,避免堆积数据,从而降低对数据库IO性能的影响。 | |
对数据库的影响 | 从数据库实例中读取数据,对数据库性能有一定影响,但不会造成锁表的情况。 | 从数据库磁盘中读取数据,对数据库IO性能有一定影响,但不会造成锁表的情况。 |
如何设置MySQL数据库备份的binlog_format?
数据灾备(DBS)提供数据全量备份、增量备份和数据恢复等能力。为了保证备份正常运行,您在配置备份实例时,数据灾备(DBS)对待备份的数据库配置和账号有一定要求。
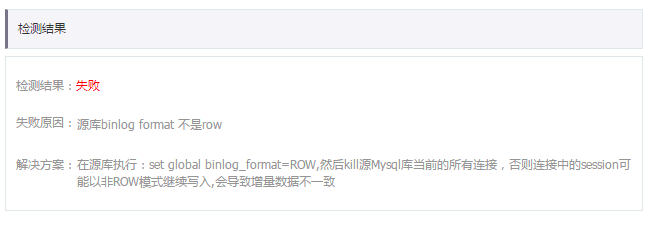
报错场景
在数据灾备(DBS)控制台配置备份计划的预检查阶段,预检查页面会显示检测结果失败,并提示失败原因是源库binlog_format不是ROW模式。更多详情,请参见云下及他云数据库备份管理。
使用说明
binlog_format需要设置为ROW,ROW模式下会将DML操作完整的前镜像和后镜像数据,便于数据恢复。binlog_format不推荐设置为statement、mixed模式,相比而言ROW模式更为稳定和可靠。将
binlog_format设置为ROW,只会改变binlog日志内容,不会影响数据库查询,但建议kill数据库当前所有连接,以保证ROW模式在所有数据库连接上生效。
操作步骤
使用高权限账号在源数据库中执行如下命令,将
binlog_format设置为ROW。SET GLOBAL binlog_format = 'ROW';您可以通过如下命令查看当前MySQL数据库的binlog_format参数取值:
SHOW GLOBAL VARIABLES LIKE 'binlog_format';kill当前数据库所有连接,否则连接中的进程可能会以非ROW模式继续写入,导致增量数据不一致。
如何恢复数据到其它数据库实例?
数据灾备(DBS)支持恢复已有备份数据到源备份数据库实例上,同时也支持恢复到其它已有数据库实例上,可用于误操作后恢复以及分析历史数据等场景。
不同数据库引擎的恢复配置略有不同,各类数据库恢复配置详情,请参见各类数据库引擎的详细配置案例。
单击目标数据源ID进入数据源详情页。
阿里云数据库:在备份数据 > 逻辑备份页面中,单击创建恢复任务。
ECS自建数据库/云下及他云数据库:在备份数据页面中,单击创建恢复任务。
设置恢复的位置和方式,单击下一步。
参数项
说明
恢复任务名称
请输入恢复任务名称,建议配置具有业务意义的名称(无唯一性要求),便于后续识别。
恢复位置
恢复到原实例:库表数据会恢复到原实例中。
恢复到新实例:后续根据步骤5指引,自动新建一个RDS实例,库表数据会恢复到新实例中。
恢复方式
按备份集:选择恢复的目标备份集,请确保目标备份集内数据有效。
按时间点:根据备份集保留时长,选择的时间必须在可恢复的时间范围内,可恢复的时间范围是从有效备份集的恢复时间点到系统当前时间点,最长不超过30天。
说明日志备份默认开启且为可读,无法关闭。
日志备份集保留时长固定为30天暂不支持修改。
恢复到新实例,需设置如下参数。
参数项
说明
数据库所在位置
新建实例所在位置,此项默认RDS,固定配置。
实例地区
新建实例所在地区,与数据源在同一地域中,固定配置。
VPC
选择新建实例所在的专有网络VPC。如需创建专有网络,请参见创建和管理专有网络。
实例规格
选择新建实例的实例规格,可选规格以控制台为准。
说明新建实例规格建议大于或等于源实例规格。如果新实例规格小于源实例规格,那么新实例可能无法支持源实例中存储的所有数据,导致数据丢失或无法正常使用等。
存储空间
新建实例的存储空间,可选存储空间以控制台为准。
说明为确保有足够的空间恢复数据,建议您选择存储空间大小为源实例存储空间的1.3倍以上,或者DBS全量备份集大小的5~6倍以上(DBS备份时会有压缩)。
您可在数据源的备份数据页面(数据源为云数据库时还需进入逻辑备份页签)下查看备份集大小。
选择恢复对象,单击提交。
参数项
说明
恢复对象
在源库对象框中选中需要恢复的库或表单击
 移动到已选择对象框中。您可以单击编辑按钮设置恢复后的库表。
移动到已选择对象框中。您可以单击编辑按钮设置恢复后的库表。冲突处理
默认为遇到同名对象则重命名,例如表
job_info恢复时遇到同名表,系统会默认将新表重命名为job_info_dbs_<恢复任务ID>_<时间戳>。等待预检查完成后,在预检查对话框中,单击启动。
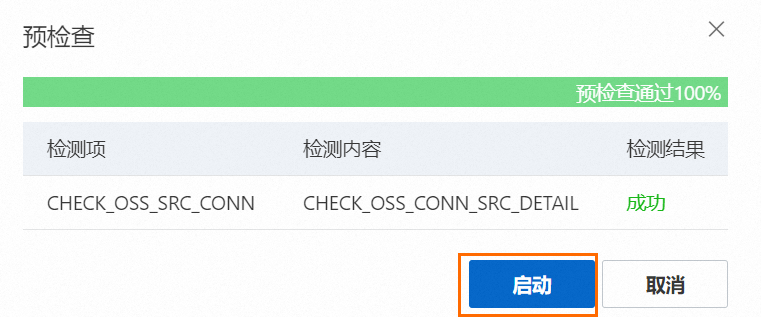 说明
说明您也可以单击取消按钮选择当前暂不启动恢复任务,后续在任务管理 > 恢复任务页面中,单击目标恢复任务操作列下的启动,随时启动恢复任务即可。
如何备份RDS只读实例?
前提条件
已购买DBS备份计划。购买方法,请参见创建备份计划。
说明购买时,选择数据库类型为MySQL,并选择备份方式为逻辑备份。
已创建RDS MySQL只读实例。创建方法,请参见创建MySQL只读实例。
若通过本文方法一:通过公网配置备份计划,您需要:
获取只读实例的外网地址。具体操作,请参见查看和管理实例连接地址和端口。
将DBS服务网段IP添加进只读实例的白名单中。添加白名单的具体操作,请参见设置IP白名单。
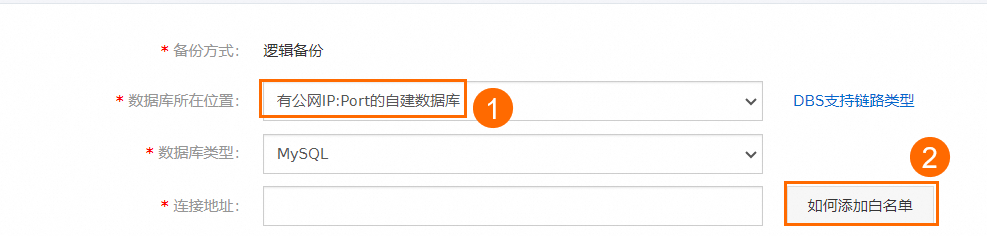
说明配置备份计划时,选择数据库所在位置为有公网IP:Port的自建数据库后,单击如何添加白名单按钮,获取DBS服务网段IP。
若通过本文方法二:通过内网配置备份计划,您需要:
已获取只读实例的内网地址,并在本地通过ping命令获取一个即时的内网IP。
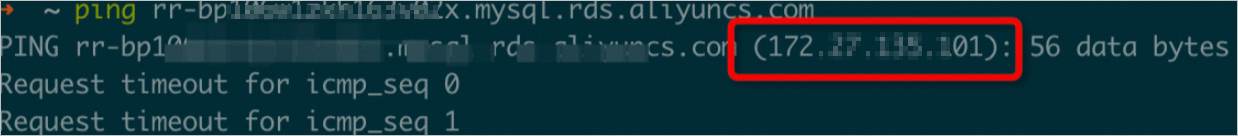 重要
重要获取的内网IP在部分场景下可能会发生变化,导致备份失败。更多详情,请参见备份对数据库的有什么影响?。
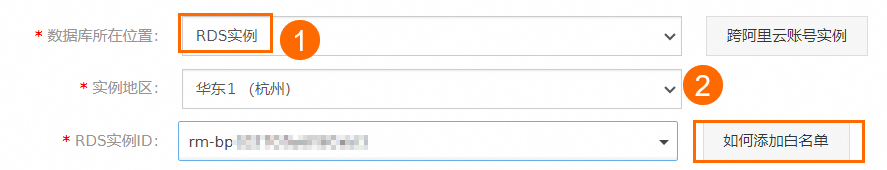
已将DBS服务网段IP添加进只读实例的白名单中。添加白名单的具体操作,请参见设置IP白名单。
说明配置备份计划时,选择数据库所在位置为RDS实例后,单击如何添加白名单按钮,获取DBS服务网段IP。
注意事项
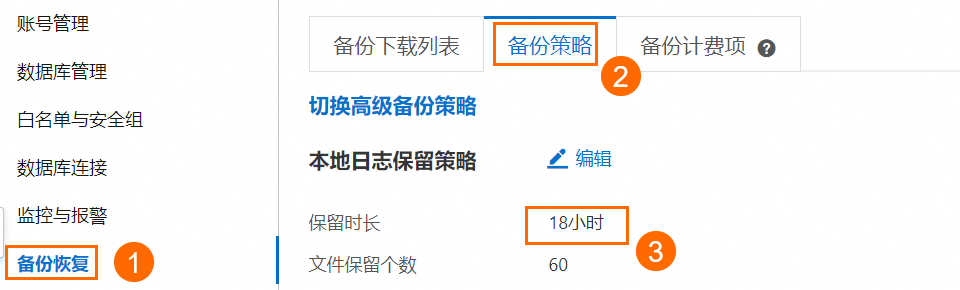
使用公网备份时binlog日志可能会存在延迟,建议您在RDS MySQL只读实例备份恢复页面的备份策略页签下,将本地日志的保留时长设置为较大值。默认保留时长为18小时。
通过内网配置备份计划时,当只读实例发生克隆、迁移可用区、切换VPC、切换交换机时,所获取的即时内网IP可能会发生变化,从而源实例连接失败,导致备份失败。
出现该情况时,请参见前提条件获取一个新的即时内网IP,并重新如何修改备份源数据库,保存生效即可。
操作步骤
您可以选择数据库所在位置为有公网IP:Port的自建数据库或通过专线/VPN网关/智能网关接入的自建数据库两种方法来配置RDS MySQL只读实例的备份计划。
方法一:通过公网配置备份计划
找到目标备份计划ID,单击右侧操作列下的配置备份计划。
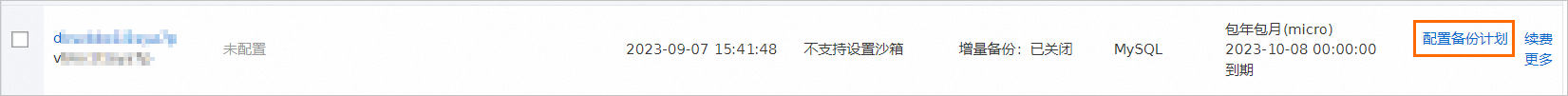
在配置备份源和目标页面,配置备份源信息与备份目标信息,并单击页面右下角的下一步。
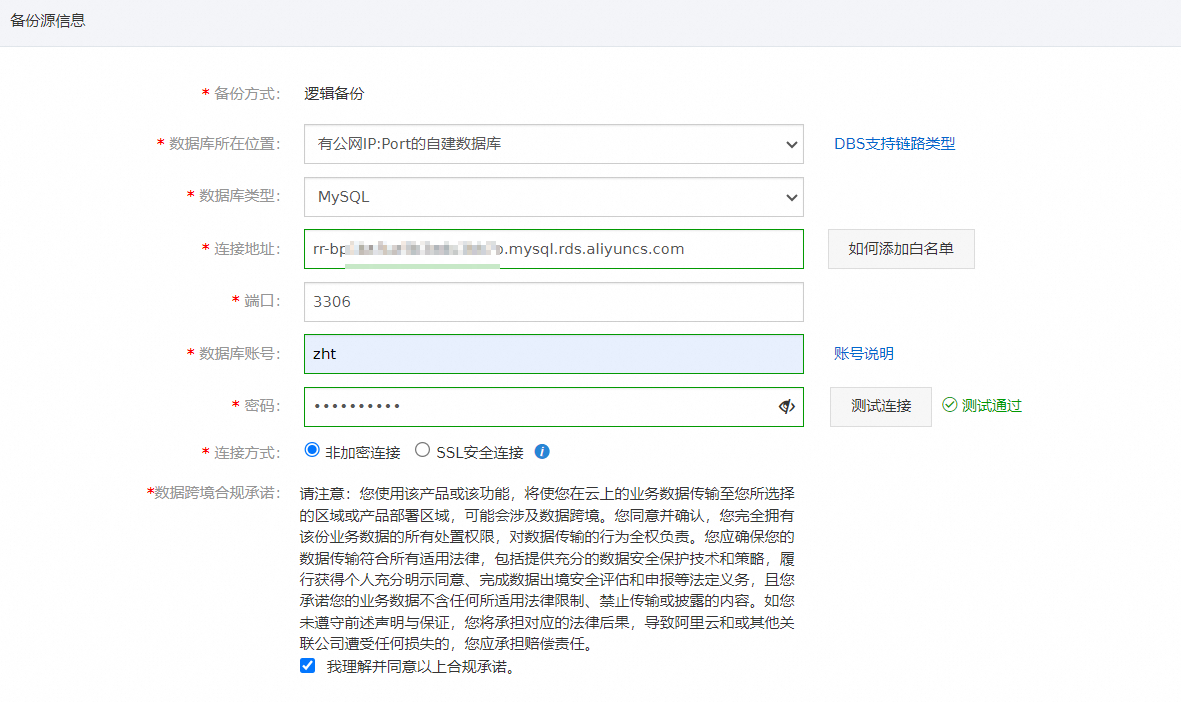 说明
说明数据库所在位置选择有公网IP:Port的自建数据库。
连接地址填写RDS MySQL只读实例的外网连接地址。具体操作,请参见查看和管理实例连接地址和端口。
其他参数项配置说明,请参见管理备份计划。
在配置备份对象页面,将目标数据库内的库表移动到已选择数据库对象框中,单击下一步。
说明逻辑备份:您可按需选择后续系统全量备份时备份哪些库表,部分数据库支持选择多库、单库或单表。部分数据库支持增量备份,且增量备份不区分库表,默认备份全部增量数据。
您可单击页面左下角的全选中来选中整个数据库进行备份。各个数据库支持的备份对象及备份粒度不同,详情请参见支持的数据库类型与功能。
备份任务默认不支持备份后续新创建的数据库,如需备份该库,您可在备份计划配置中添加该库便于后续备份。具体操作,请参见修改备份对象。
物理备份:仅支持备份整个数据库实例。
在配置备份时间页面,配置备份时间等信息,并单击页面右下角的下一步。
配置
说明
全量备份频率
按需选择周期备份或单次备份。
说明需要恢复增量数据的场景,建议选择周期备份,一周至少做一次全量备份。否则恢复时需要回放大量binlog,会有很大几率出现恢复异常,恢复RTO(Recovery Time Objective)长,恢复失败的情况。
全量备份周期
全量备份频率为周期备份时必选。勾选备份数据的周期,每周最少选择一天进行数据备份。
全量备份开始时间
全量备份频率为周期备份时必选。选择备份开始时间,例如01:00,建议设置为业务低峰期。
说明若到了指定备份时间点,仍有上次的全量备份任务在进行中,则会自动跳过一次备份。
增量备份
选择是否开启增量备份,开启该参数时,请确保目标数据库已开启Binlog。
说明该参数仅在全量备份频率参数为周期备份时显示。
RDS MySQL已默认开启Binlog,自建数据库需要手动开启Binlog。
全量备份并行线程数上限
填写全量备份并行线程数上限,您可以通过设置该参数调节备份速度,例如降低备份线程数,以减少对数据库的影响。
备份网络限速
网络带宽限制(默认为0,表示不限速),单位为MB/s,取值不限。
说明该参数仅在备份MySQL数据库时显示。
在配置生命周期页面,输入全量备份数据的保存时间。
说明若您在上一步开启了增量备份功能,您还需要配置增量备份数据的备份时间。
完成上述配置后,单击页面右下角的预检查并启动。
在预检查对话框中显示预检查通过后,单击立即启动。
说明待备份计划状态变为运行中,表示备份计划已配置完成。
如果备份计划出现异常或报错,建议您及时排查问题并修复。具体操作,请参见如何修复异常DBS备份计划。若按照文中修复建议仍未解决您的问题,请到DBS客户咨询群(钉钉群号:35585947)进行咨询。
方法二:通过内网配置备份计划
找到目标备份计划ID,单击右侧操作列下的配置备份计划。

在配置备份源和目标页面,配置备份源信息与备份目标信息,并单击页面右下角的下一步。
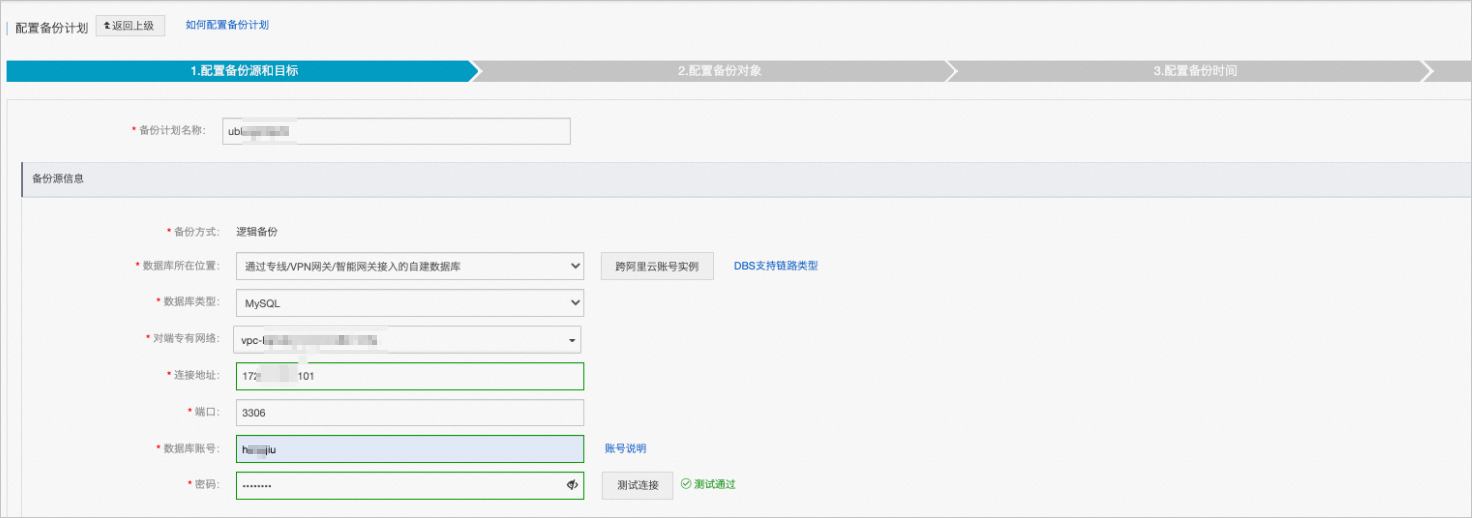 说明
说明数据库所在位置选择通过专线/VPN网关/智能网关接入的自建数据库。
对端专有网络选择目标RDS MySQL只读实例的专有网络。
连接地址填写用户已获取的内网IP地址,可参见前提条件。
端口填写目标RDS MySQL只读实例的端口号。
其他参数项配置说明,请参见管理备份计划。
在配置备份对象页面,将目标数据库内的库表移动到已选择数据库对象框中,单击下一步。
说明逻辑备份:您可按需选择后续系统全量备份时备份哪些库表,部分数据库支持选择多库、单库或单表。部分数据库支持增量备份,且增量备份不区分库表,默认备份全部增量数据。
您可单击页面左下角的全选中来选中整个数据库进行备份。各个数据库支持的备份对象及备份粒度不同,详情请参见支持的数据库类型与功能。
备份任务默认不支持备份后续新创建的数据库,如需备份该库,您可在备份计划配置中添加该库便于后续备份。具体操作,请参见修改备份对象。
物理备份:仅支持备份整个数据库实例。
在配置备份时间页面,配置备份时间等信息,并单击页面右下角的下一步。
配置
说明
全量备份频率
按需选择周期备份或单次备份。
说明需要恢复增量数据的场景,建议选择周期备份,一周至少做一次全量备份。否则恢复时需要回放大量binlog,会有很大几率出现恢复异常,恢复RTO(Recovery Time Objective)长,恢复失败的情况。
全量备份周期
全量备份频率为周期备份时必选。勾选备份数据的周期,每周最少选择一天进行数据备份。
全量备份开始时间
全量备份频率为周期备份时必选。选择备份开始时间,例如01:00,建议设置为业务低峰期。
说明若到了指定备份时间点,仍有上次的全量备份任务在进行中,则会自动跳过一次备份。
增量备份
选择是否开启增量备份,开启该参数时,请确保目标数据库已开启Binlog。
说明该参数仅在全量备份频率参数为周期备份时显示。
RDS MySQL已默认开启Binlog,自建数据库需要手动开启Binlog。
全量备份并行线程数上限
填写全量备份并行线程数上限,您可以通过设置该参数调节备份速度,例如降低备份线程数,以减少对数据库的影响。
备份网络限速
网络带宽限制(默认为0,表示不限速),单位为MB/s,取值不限。
说明该参数仅在备份MySQL数据库时显示。
在配置生命周期页面,输入全量备份数据的保存时间。
说明若您在上一步开启了增量备份功能,您还需要配置增量备份数据的备份时间。
完成上述配置后,单击页面右下角的预检查并启动。
在预检查对话框中显示预检查通过后,单击立即启动。
说明待备份计划状态变为运行中,表示备份计划已配置完成。
如果备份计划出现异常或报错,建议您及时排查问题并修复。具体操作,请参见如何修复异常DBS备份计划。若按照文中修复建议仍未解决您的问题,请到DBS客户咨询群(钉钉群号:35585947)进行咨询。
获取只读实例内外网地址
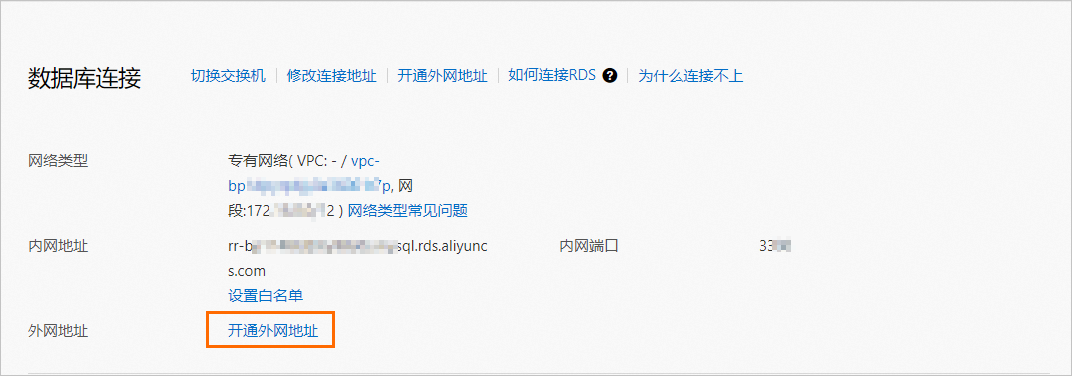
访问RDS实例列表,在上方选择地域,然后单击目标实例ID。
在基本信息页面,单击查看连接详情,获取只读实例内外网地址。
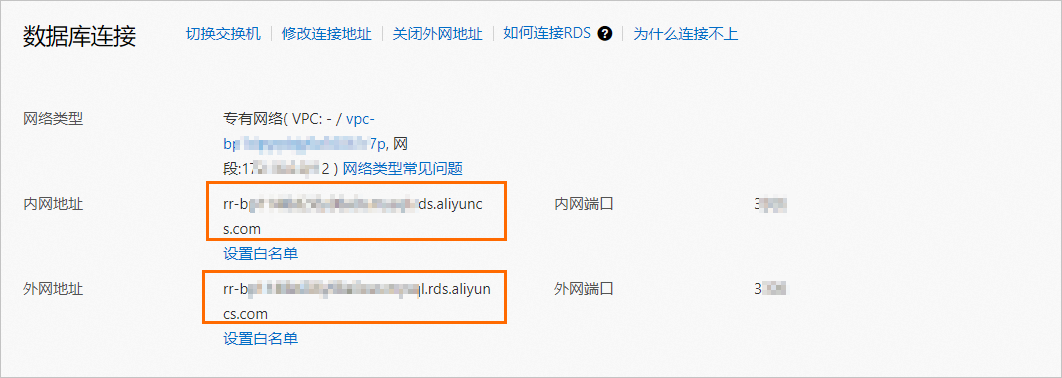 说明
说明如果只读实例还未开通外网(公网)地址。请单击开通外网地址 > 确定,开通后再获取外网地址。
常见问题
Q:通过内网IP配置的备份计划出现连接源实例失败的情况,可能原因及解决方法是什么?
A:可能原因:本文方法二中的IP是一个即时的内网IP,当只读实例发生克隆、迁移可用区、切换VPC、切换交换机时,即时内网IP可能会发生变化,从而源实例连接失败,导致备份失败。
解决方法:通过只读实例的内网地址,并在本地通过ping命令重新获取一个即时的内网IP,并重新如何修改备份源数据库,保存生效即可。

Q:数据灾备(DBS)支持备份只读实例的全量备份数据和增量备份数据吗?
A:支持。
DBS与RDS备份有什么区别?
针对RDS数据库,DBS提供转储备份和逻辑备份,满足RDS客户的异地备份和灵活备份诉求。
针对RDS数据库,RDS提供物理备份,满足RDS客户的本地备份和快速恢复诉求。

DBS转储备份给RDS用户带来了什么价值?
异地备份
安全、稳定的备份专用网络。
直接转储RDS原生物理备份数据和日志,无需额外发起备份。
备份集可一键恢复到RDS。
最长5年保留,备份集独立保留,即使RDS实例释放后,备份集仍会按照设置的保留时间进行保留。
存储自动扩容、免运维。
灵活备份
DBS提供核心表备份能力,实时保护核心数据,单表全量备份+实时增量备份,RPO达到秒级,数据可以恢复到任意时间点。
DBS提供单表恢复能力,从整个备份集中抽取一张表数据,恢复时间仅与实际恢复数据量有关,实现分钟级数据恢复。
DBS提供库表映射恢复能力,数据恢复无需额外购买数据库实例,可以将数据直接恢复到原数据库实例,通过库表映射功能,用户可以手工对库表进行重命名恢复,同时DBS提供的同名对象冲突处理策略,恢复过程中遇到同名库表会自动重命名,不会删除或修改恢复目标数据库上原始数据。
针对RDS数据库,DBS与DMS深度集成,支持在DMS上直接发起备份和恢复,功能入口:安全与规范(DBS) > 数据灾备(DBS)。

如何查看OSS备份文件?
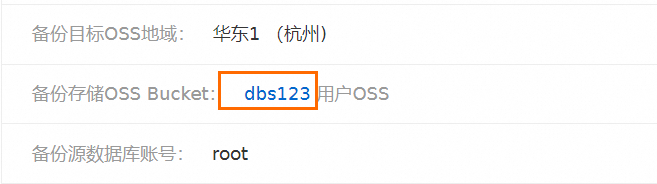
数据灾备(DBS)支持将数据库实例备份到您自建的OSS中,当您将数据备份至用户OSS时,DBS会在指定OSS Bucket中自动创建备份目录,无需您手动创建。备份文件命名规则为<备份任务ID>/<备份类型>/<运行备份任务(全量或增量任务)ID>/<具体数据>。
找到目标备份计划ID,单击右侧操作列下方的管理。
在备份任务配置页面,找到备份存储OSS Bucket,单击目标OSS Bucket。
系统将自动跳转至OSS控制台的目标Bucket目录,如下图分别表示
full(全量备份)文件夹和continuous(增量备份)文件夹。OSS的更多信息,请参见开始使用OSS。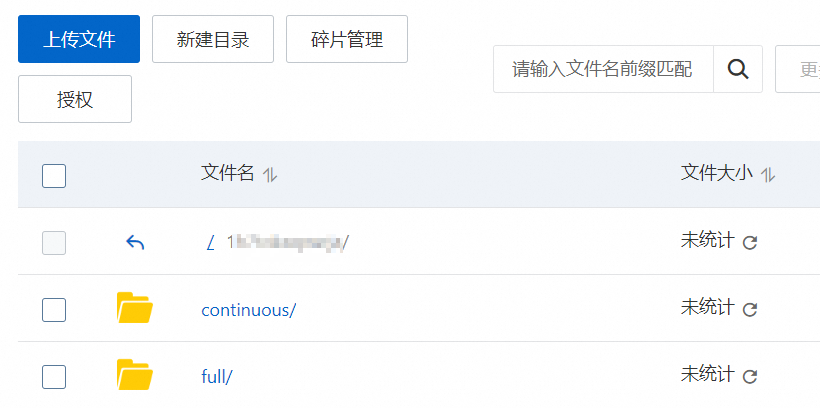
为什么DBS备份SQL运行时间与RDS控制台显示不一致?
出于备份数据可靠性考虑,针对DBS逻辑备份,运行备份SQL时会设置0时区,而RDS的SQL审计记录备份SQL会带上东8区信息,因此RDS控制台上备份SQL的显示运行时间与真实运行时间会相差8小时,真实运行时间以DBS控制台为准。
备份对数据库的有什么影响?
数据灾备(DBS)对数据库执行备份时会造成一定影响,建议选择业务低峰期执行备份任务。
类目 | 逻辑备份 | 物理备份 |
全量备份原理 | 对每张表数据进行切分,然后在数据库上执行SQL语句,多线程并行读取数据。 | 在数据库所在服务器上安装DBS备份网关,然后通过备份网关将数据库文件进行备份(拷贝)。 |
增量备份原理 | 支持实时捕获数据库内存中的日志,实现实时增量备份,避免堆积数据,从而降低对数据库IO性能的影响。 | |
对数据库的影响 | 从数据库实例中读取数据,对数据库性能有一定影响,但不会造成锁表的情况。 | 从数据库磁盘中读取数据,对数据库IO性能有一定影响,但不会造成锁表的情况。 |