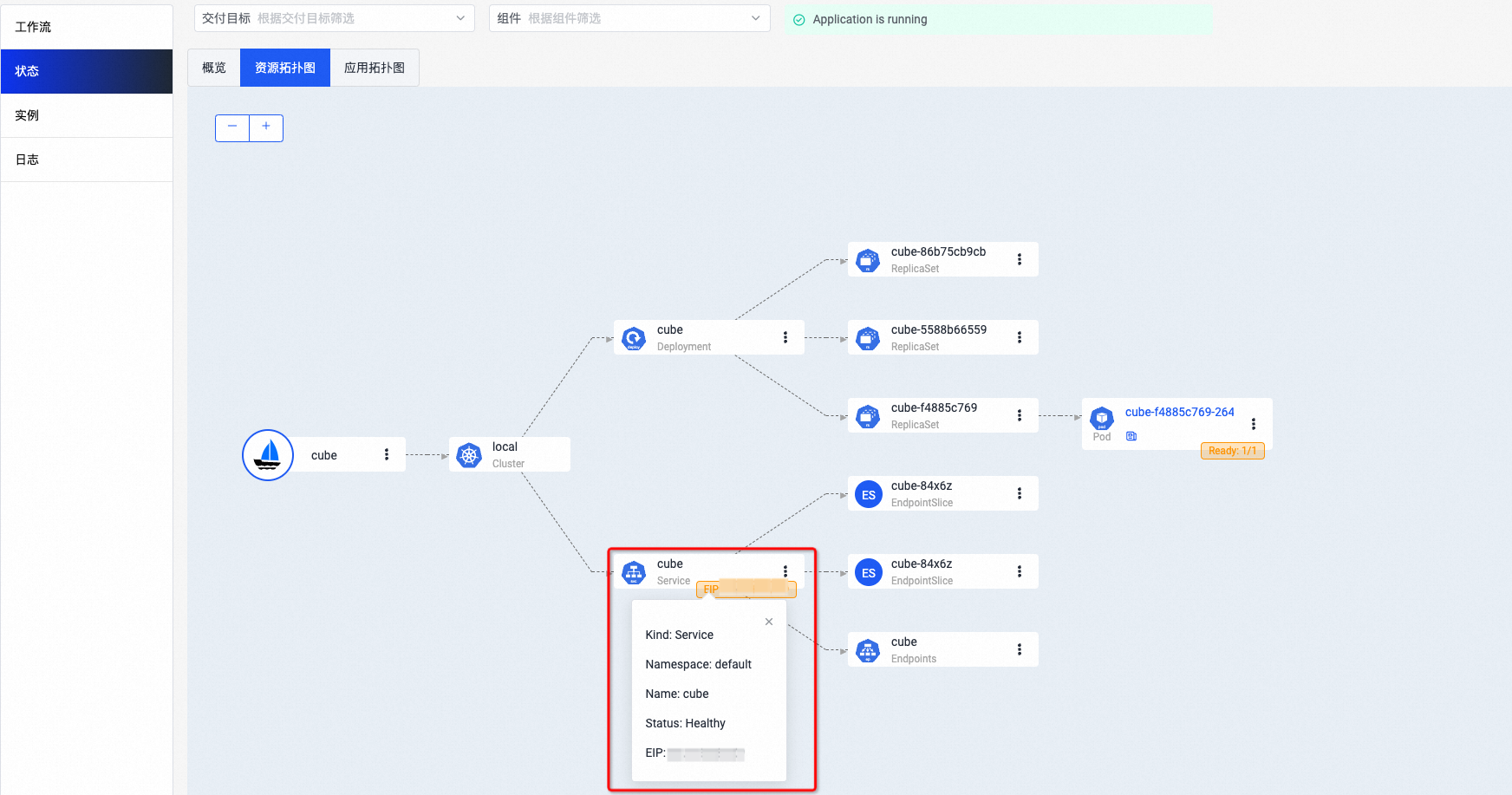
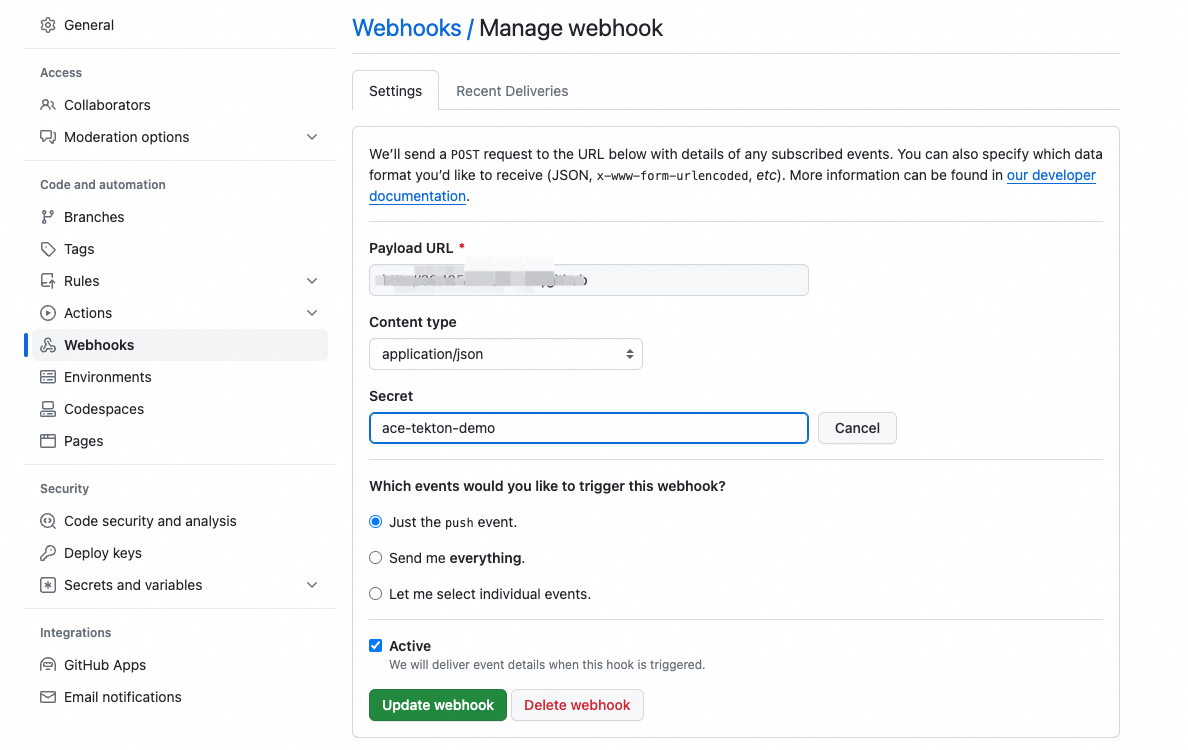
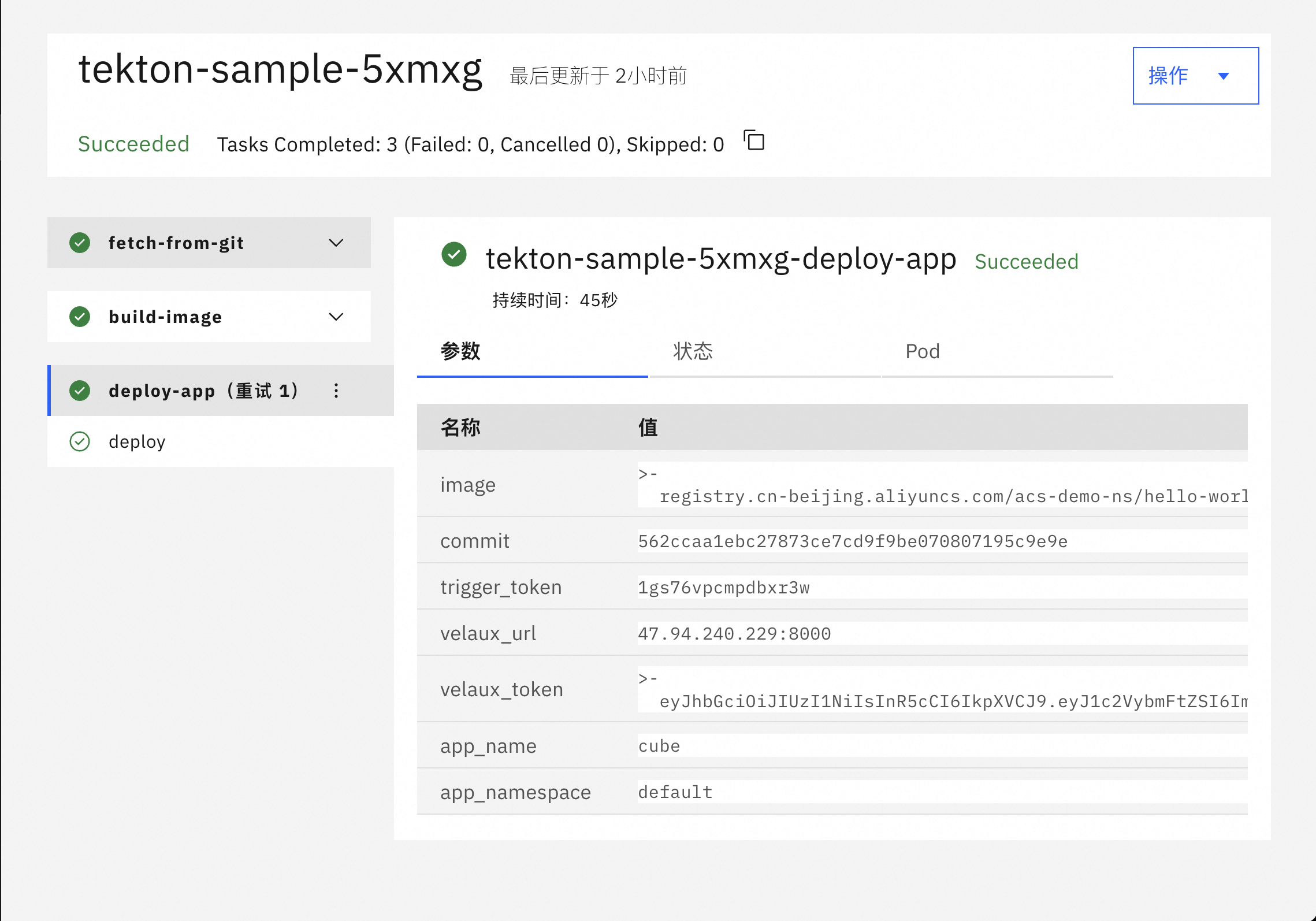
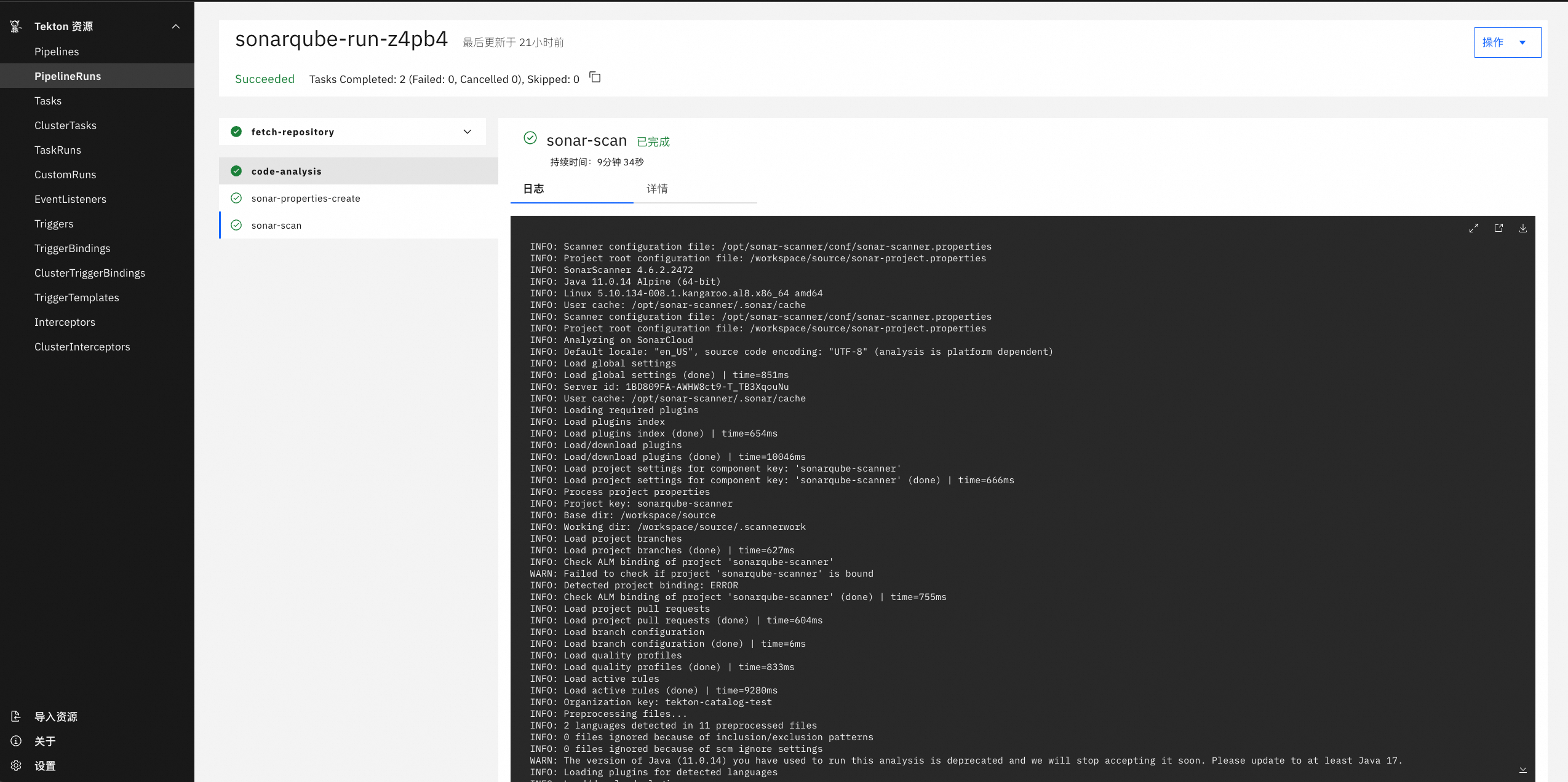
Tekton是一套开源的云原生解决方案,它提供了灵活的、易扩展的方式协助使用者构建CI/CD流水线。本文主要基于tekton-pipelines、tekton-trigger和kubevela构建一条GitOps的持续集成和持续交付流水线实践。
前提条件
已在ACS集群安装CoreDNS。具体操作,请参见非托管CoreDNS配置说明。
已通过Kubectl工具连接ACS集群。具体操作,请参见通过kubectl快速使用ACS。
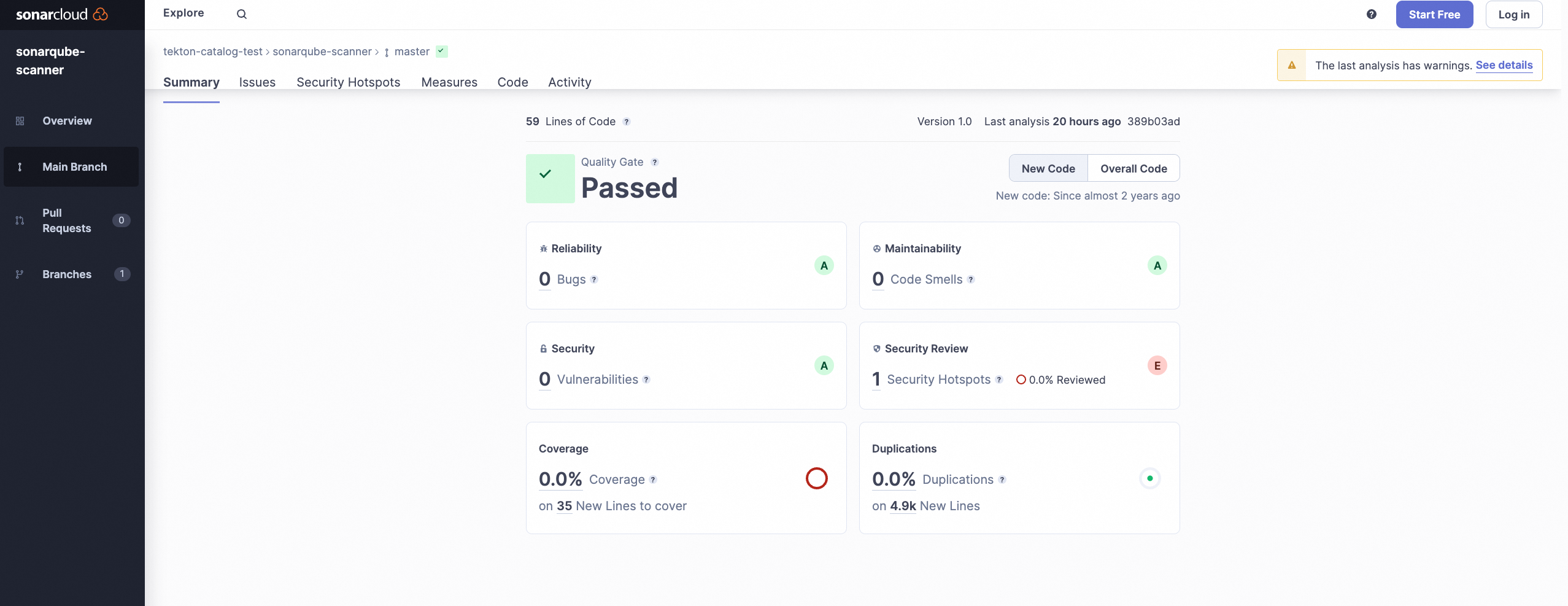
Tekton介绍
Tekton是一个基于云原生场景的解决方案,诞生自Knative项目。它是一个流水线编排工具,旨在支持云原生应用的交付和部署。本实践主要使用Tekton的组件tekton-pipeline和tekton-triggers实现GitOps交付。通过Tekton的流水线编排和周边生态的支持,实现更高效、可靠的云原生应用交付流程。
Tekton中的核心概念说明如下:
Task:实例化后是Tekton编排流水线的最小单位,其内部可以定义Steps子步骤进行串行处理,每个Task会由控制器拉起的一个Pod内进行执行,Steps之间可以定义inputs和outputs进行参数传递。
Pipeline:实例化为一个Pipeline对象,以一个DAG(有向无环图)对Task进行编排,Task之间可以定义inputs和outputs进行参数传递。
PipelineRun:可以理解为一个Pipeline对象的最终执行器,它会具体实例化出一个Pipeline对象进行执行。
本文主要按照以下三个步骤逐步丰富GitOps流水线:
先定义持续集成流水线,进行代码克隆和镜像构建。
添加持续交付任务,通过KubeVela进行服务发布。
添加Trigger,以提交代码为一次触发源完成整个GitOps流程。
Tekton是一个非常强大且功能丰富的云原生流程编排框架,每一个Task都将以Pod的形式运行,其特点非常类似Kubernetes的Job资源,根据Tekton的这种运行模式,在以下实践中我们可以结合ACS的一些产品特点来使用Serverless化的容器算力资源:
使用BestEffort实例来运行Task:结合Tekton框架的任务容灾能力和BestEffort实例的低成本特点来降低资源成本。更多关于BestEffort实例请参考BestEffort算力质量概述。
ACS提供灵活的资源规格:默认最小0.25Core CPU、0.5GiB内存的规格,以及CPU/内存0.25的步长可以给Task设置灵活的资源规格。
安装步骤
步骤一:安装Tekton Pipelines组件
使用以下内容,创建tekton-v0.46.0.yaml。
展开查看tekton-v0.46.0.yaml
apiVersion: v1 kind: Namespace metadata: name: tekton-pipelines labels: app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines pod-security.kubernetes.io/enforce: restricted --- # Copyright 2020-2022 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # https://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. kind: ClusterRole apiVersion: rbac.authorization.k8s.io/v1 metadata: name: tekton-pipelines-controller-cluster-access labels: app.kubernetes.io/component: controller app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines rules: - apiGroups: [""] # Controller needs to watch Pods created by TaskRuns to see them progress. resources: ["pods"] verbs: ["list", "watch"] # Controller needs cluster access to all of the CRDs that it is responsible for # managing. - apiGroups: ["tekton.dev"] resources: ["tasks", "clustertasks", "taskruns", "pipelines", "pipelineruns", "runs", "customruns"] verbs: ["get", "list", "create", "update", "delete", "patch", "watch"] - apiGroups: ["tekton.dev"] resources: ["verificationpolicies"] verbs: ["get", "list", "watch"] - apiGroups: ["tekton.dev"] resources: ["taskruns/finalizers", "pipelineruns/finalizers", "runs/finalizers", "customruns/finalizers"] verbs: ["get", "list", "create", "update", "delete", "patch", "watch"] - apiGroups: ["tekton.dev"] resources: ["tasks/status", "clustertasks/status", "taskruns/status", "pipelines/status", "pipelineruns/status", "runs/status", "customruns/status", "verificationpolicies/status"] verbs: ["get", "list", "create", "update", "delete", "patch", "watch"] # resolution.tekton.dev - apiGroups: ["resolution.tekton.dev"] resources: ["resolutionrequests", "resolutionrequests/status"] verbs: ["get", "list", "create", "update", "delete", "patch", "watch"] --- kind: ClusterRole apiVersion: rbac.authorization.k8s.io/v1 metadata: # This is the access that the controller needs on a per-namespace basis. name: tekton-pipelines-controller-tenant-access labels: app.kubernetes.io/component: controller app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines rules: # Read-write access to create Pods and PVCs (for Workspaces) - apiGroups: [""] resources: ["pods", "persistentvolumeclaims"] verbs: ["get", "list", "create", "update", "delete", "patch", "watch"] # Write permissions to publish events. - apiGroups: [""] resources: ["events"] verbs: ["create", "update", "patch"] # Read-only access to these. - apiGroups: [""] resources: ["configmaps", "limitranges", "secrets", "serviceaccounts"] verbs: ["get", "list", "watch"] # Read-write access to StatefulSets for Affinity Assistant. - apiGroups: ["apps"] resources: ["statefulsets"] verbs: ["get", "list", "create", "update", "delete", "patch", "watch"] --- kind: ClusterRole apiVersion: rbac.authorization.k8s.io/v1 metadata: name: tekton-pipelines-webhook-cluster-access labels: app.kubernetes.io/component: webhook app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines rules: # The webhook needs to be able to get and update customresourcedefinitions, # mainly to update the webhook certificates. - apiGroups: ["apiextensions.k8s.io"] resources: ["customresourcedefinitions", "customresourcedefinitions/status"] verbs: ["get", "update", "patch"] resourceNames: - pipelines.tekton.dev - pipelineruns.tekton.dev - runs.tekton.dev - tasks.tekton.dev - clustertasks.tekton.dev - taskruns.tekton.dev - resolutionrequests.resolution.tekton.dev - customruns.tekton.dev - verificationpolicies.tekton.dev # knative.dev/pkg needs list/watch permissions to set up informers for the webhook. - apiGroups: ["apiextensions.k8s.io"] resources: ["customresourcedefinitions"] verbs: ["list", "watch"] - apiGroups: ["admissionregistration.k8s.io"] # The webhook performs a reconciliation on these two resources and continuously # updates configuration. resources: ["mutatingwebhookconfigurations", "validatingwebhookconfigurations"] # knative starts informers on these things, which is why we need get, list and watch. verbs: ["list", "watch"] - apiGroups: ["admissionregistration.k8s.io"] resources: ["mutatingwebhookconfigurations"] # This mutating webhook is responsible for applying defaults to tekton objects # as they are received. resourceNames: ["webhook.pipeline.tekton.dev"] # When there are changes to the configs or secrets, knative updates the mutatingwebhook config # with the updated certificates or the refreshed set of rules. verbs: ["get", "update", "delete"] - apiGroups: ["admissionregistration.k8s.io"] resources: ["validatingwebhookconfigurations"] # validation.webhook.pipeline.tekton.dev performs schema validation when you, for example, create TaskRuns. # config.webhook.pipeline.tekton.dev validates the logging configuration against knative's logging structure resourceNames: ["validation.webhook.pipeline.tekton.dev", "config.webhook.pipeline.tekton.dev"] # When there are changes to the configs or secrets, knative updates the validatingwebhook config # with the updated certificates or the refreshed set of rules. verbs: ["get", "update", "delete"] - apiGroups: [""] resources: ["namespaces"] verbs: ["get"] # The webhook configured the namespace as the OwnerRef on various cluster-scoped resources, # which requires we can Get the system namespace. resourceNames: ["tekton-pipelines"] - apiGroups: [""] resources: ["namespaces/finalizers"] verbs: ["update"] # The webhook configured the namespace as the OwnerRef on various cluster-scoped resources, # which requires we can update the system namespace finalizers. resourceNames: ["tekton-pipelines"] --- # Copyright 2020 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # https://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. kind: Role apiVersion: rbac.authorization.k8s.io/v1 metadata: name: tekton-pipelines-controller namespace: tekton-pipelines labels: app.kubernetes.io/component: controller app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines rules: - apiGroups: [""] resources: ["configmaps"] verbs: ["list", "watch"] # The controller needs access to these configmaps for logging information and runtime configuration. - apiGroups: [""] resources: ["configmaps"] verbs: ["get"] resourceNames: ["config-logging", "config-observability", "config-artifact-bucket", "config-artifact-pvc", "feature-flags", "config-leader-election", "config-registry-cert"] --- kind: Role apiVersion: rbac.authorization.k8s.io/v1 metadata: name: tekton-pipelines-webhook namespace: tekton-pipelines labels: app.kubernetes.io/component: webhook app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines rules: - apiGroups: [""] resources: ["configmaps"] verbs: ["list", "watch"] # The webhook needs access to these configmaps for logging information. - apiGroups: [""] resources: ["configmaps"] verbs: ["get"] resourceNames: ["config-logging", "config-observability", "config-leader-election", "feature-flags"] - apiGroups: [""] resources: ["secrets"] verbs: ["list", "watch"] # The webhook daemon makes a reconciliation loop on webhook-certs. Whenever # the secret changes it updates the webhook configurations with the certificates # stored in the secret. - apiGroups: [""] resources: ["secrets"] verbs: ["get", "update"] resourceNames: ["webhook-certs"] --- kind: Role apiVersion: rbac.authorization.k8s.io/v1 metadata: name: tekton-pipelines-leader-election namespace: tekton-pipelines labels: app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines rules: # We uses leases for leaderelection - apiGroups: ["coordination.k8s.io"] resources: ["leases"] verbs: ["get", "list", "create", "update", "delete", "patch", "watch"] --- apiVersion: rbac.authorization.k8s.io/v1 kind: Role metadata: name: tekton-pipelines-info namespace: tekton-pipelines labels: app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines rules: # All system:authenticated users needs to have access # of the pipelines-info ConfigMap even if they don't # have access to the other resources present in the # installed namespace. - apiGroups: [""] resources: ["configmaps"] resourceNames: ["pipelines-info"] verbs: ["get"] --- # Copyright 2019 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # http://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: v1 kind: ServiceAccount metadata: name: tekton-pipelines-controller namespace: tekton-pipelines labels: app.kubernetes.io/component: controller app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines --- apiVersion: v1 kind: ServiceAccount metadata: name: tekton-pipelines-webhook namespace: tekton-pipelines labels: app.kubernetes.io/component: webhook app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines --- # Copyright 2019 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # http://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRoleBinding metadata: name: tekton-pipelines-controller-cluster-access labels: app.kubernetes.io/component: controller app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines subjects: - kind: ServiceAccount name: tekton-pipelines-controller namespace: tekton-pipelines roleRef: kind: ClusterRole name: tekton-pipelines-controller-cluster-access apiGroup: rbac.authorization.k8s.io --- # If this ClusterRoleBinding is replaced with a RoleBinding # then the ClusterRole would be namespaced. The access described by # the tekton-pipelines-controller-tenant-access ClusterRole would # be scoped to individual tenant namespaces. apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRoleBinding metadata: name: tekton-pipelines-controller-tenant-access labels: app.kubernetes.io/component: controller app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines subjects: - kind: ServiceAccount name: tekton-pipelines-controller namespace: tekton-pipelines roleRef: kind: ClusterRole name: tekton-pipelines-controller-tenant-access apiGroup: rbac.authorization.k8s.io --- apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRoleBinding metadata: name: tekton-pipelines-webhook-cluster-access labels: app.kubernetes.io/component: webhook app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines subjects: - kind: ServiceAccount name: tekton-pipelines-webhook namespace: tekton-pipelines roleRef: kind: ClusterRole name: tekton-pipelines-webhook-cluster-access apiGroup: rbac.authorization.k8s.io --- # Copyright 2020 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # http://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: rbac.authorization.k8s.io/v1 kind: RoleBinding metadata: name: tekton-pipelines-controller namespace: tekton-pipelines labels: app.kubernetes.io/component: controller app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines subjects: - kind: ServiceAccount name: tekton-pipelines-controller namespace: tekton-pipelines roleRef: kind: Role name: tekton-pipelines-controller apiGroup: rbac.authorization.k8s.io --- apiVersion: rbac.authorization.k8s.io/v1 kind: RoleBinding metadata: name: tekton-pipelines-webhook namespace: tekton-pipelines labels: app.kubernetes.io/component: webhook app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines subjects: - kind: ServiceAccount name: tekton-pipelines-webhook namespace: tekton-pipelines roleRef: kind: Role name: tekton-pipelines-webhook apiGroup: rbac.authorization.k8s.io --- apiVersion: rbac.authorization.k8s.io/v1 kind: RoleBinding metadata: name: tekton-pipelines-controller-leaderelection namespace: tekton-pipelines labels: app.kubernetes.io/component: controller app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines subjects: - kind: ServiceAccount name: tekton-pipelines-controller namespace: tekton-pipelines roleRef: kind: Role name: tekton-pipelines-leader-election apiGroup: rbac.authorization.k8s.io --- apiVersion: rbac.authorization.k8s.io/v1 kind: RoleBinding metadata: name: tekton-pipelines-webhook-leaderelection namespace: tekton-pipelines labels: app.kubernetes.io/component: webhook app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines subjects: - kind: ServiceAccount name: tekton-pipelines-webhook namespace: tekton-pipelines roleRef: kind: Role name: tekton-pipelines-leader-election apiGroup: rbac.authorization.k8s.io --- apiVersion: rbac.authorization.k8s.io/v1 kind: RoleBinding metadata: name: tekton-pipelines-info namespace: tekton-pipelines labels: app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines subjects: # Giving all system:authenticated users the access of the # ConfigMap which contains version information. - kind: Group name: system:authenticated apiGroup: rbac.authorization.k8s.io roleRef: apiGroup: rbac.authorization.k8s.io kind: Role name: tekton-pipelines-info --- # Copyright 2019 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # https://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: apiextensions.k8s.io/v1 kind: CustomResourceDefinition metadata: name: clustertasks.tekton.dev labels: app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines pipeline.tekton.dev/release: "v0.46.0" version: "v0.46.0" spec: group: tekton.dev preserveUnknownFields: false versions: - name: v1beta1 served: true storage: true schema: openAPIV3Schema: type: object # One can use x-kubernetes-preserve-unknown-fields: true # at the root of the schema (and inside any properties, additionalProperties) # to get the traditional CRD behaviour that nothing is pruned, despite # setting spec.preserveUnknownProperties: false. # # See https://kubernetes.io/blog/2019/06/20/crd-structural-schema/ # See issue: https://github.com/knative/serving/issues/912 x-kubernetes-preserve-unknown-fields: true # Opt into the status subresource so metadata.generation # starts to increment subresources: status: {} names: kind: ClusterTask plural: clustertasks singular: clustertask categories: - tekton - tekton-pipelines scope: Cluster conversion: strategy: Webhook webhook: conversionReviewVersions: ["v1beta1"] clientConfig: service: name: tekton-pipelines-webhook namespace: tekton-pipelines --- # Copyright 2020 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # https://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: apiextensions.k8s.io/v1 kind: CustomResourceDefinition metadata: name: customruns.tekton.dev labels: app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines pipeline.tekton.dev/release: "v0.46.0" version: "v0.46.0" spec: group: tekton.dev preserveUnknownFields: false versions: - name: v1beta1 served: true storage: true schema: openAPIV3Schema: type: object # One can use x-kubernetes-preserve-unknown-fields: true # at the root of the schema (and inside any properties, additionalProperties) # to get the traditional CRD behaviour that nothing is pruned, despite # setting spec.preserveUnknownProperties: false. # # See https://kubernetes.io/blog/2019/06/20/crd-structural-schema/ # See issue: https://github.com/knative/serving/issues/912 x-kubernetes-preserve-unknown-fields: true additionalPrinterColumns: - name: Succeeded type: string jsonPath: ".status.conditions[?(@.type==\"Succeeded\")].status" - name: Reason type: string jsonPath: ".status.conditions[?(@.type==\"Succeeded\")].reason" - name: StartTime type: date jsonPath: .status.startTime - name: CompletionTime type: date jsonPath: .status.completionTime # Opt into the status subresource so metadata.generation # starts to increment subresources: status: {} names: kind: CustomRun plural: customruns singular: customrun categories: - tekton - tekton-pipelines scope: Namespaced --- # Copyright 2019 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # https://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: apiextensions.k8s.io/v1 kind: CustomResourceDefinition metadata: name: pipelines.tekton.dev labels: app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines pipeline.tekton.dev/release: "v0.46.0" version: "v0.46.0" spec: group: tekton.dev preserveUnknownFields: false versions: - name: v1beta1 served: true storage: true subresources: status: {} schema: openAPIV3Schema: type: object # One can use x-kubernetes-preserve-unknown-fields: true # at the root of the schema (and inside any properties, additionalProperties) # to get the traditional CRD behaviour that nothing is pruned, despite # setting spec.preserveUnknownProperties: false. # # See https://kubernetes.io/blog/2019/06/20/crd-structural-schema/ # See issue: https://github.com/knative/serving/issues/912 x-kubernetes-preserve-unknown-fields: true - name: v1 served: true storage: false schema: openAPIV3Schema: type: object # OpenAPIV3 schema allows Kubernetes to perform validation on the schema fields # and use the schema in tooling such as `kubectl explain`. # Using "x-kubernetes-preserve-unknown-fields: true" # at the root of the schema (or within it) allows arbitrary fields. # We currently perform our own validation separately. # See https://kubernetes.io/docs/tasks/extend-kubernetes/custom-resources/custom-resource-definitions/#specifying-a-structural-schema # for more info. x-kubernetes-preserve-unknown-fields: true # Opt into the status subresource so metadata.generation # starts to increment subresources: status: {} names: kind: Pipeline plural: pipelines singular: pipeline categories: - tekton - tekton-pipelines scope: Namespaced conversion: strategy: Webhook webhook: conversionReviewVersions: ["v1beta1", "v1"] clientConfig: service: name: tekton-pipelines-webhook namespace: tekton-pipelines --- # Copyright 2019 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # https://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: apiextensions.k8s.io/v1 kind: CustomResourceDefinition metadata: name: pipelineruns.tekton.dev labels: app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines pipeline.tekton.dev/release: "v0.46.0" version: "v0.46.0" spec: group: tekton.dev preserveUnknownFields: false versions: - name: v1beta1 served: true storage: true schema: openAPIV3Schema: type: object # One can use x-kubernetes-preserve-unknown-fields: true # at the root of the schema (and inside any properties, additionalProperties) # to get the traditional CRD behaviour that nothing is pruned, despite # setting spec.preserveUnknownProperties: false. # # See https://kubernetes.io/blog/2019/06/20/crd-structural-schema/ # See issue: https://github.com/knative/serving/issues/912 x-kubernetes-preserve-unknown-fields: true additionalPrinterColumns: - name: Succeeded type: string jsonPath: ".status.conditions[?(@.type==\"Succeeded\")].status" - name: Reason type: string jsonPath: ".status.conditions[?(@.type==\"Succeeded\")].reason" - name: StartTime type: date jsonPath: .status.startTime - name: CompletionTime type: date jsonPath: .status.completionTime # Opt into the status subresource so metadata.generation # starts to increment subresources: status: {} - name: v1 served: true storage: false schema: openAPIV3Schema: type: object # One can use x-kubernetes-preserve-unknown-fields: true # at the root of the schema (and inside any properties, additionalProperties) # to get the traditional CRD behaviour that nothing is pruned, despite # setting spec.preserveUnknownProperties: false. # # See https://kubernetes.io/blog/2019/06/20/crd-structural-schema/ # See issue: https://github.com/knative/serving/issues/912 x-kubernetes-preserve-unknown-fields: true additionalPrinterColumns: - name: Succeeded type: string jsonPath: ".status.conditions[?(@.type==\"Succeeded\")].status" - name: Reason type: string jsonPath: ".status.conditions[?(@.type==\"Succeeded\")].reason" - name: StartTime type: date jsonPath: .status.startTime - name: CompletionTime type: date jsonPath: .status.completionTime # Opt into the status subresource so metadata.generation # starts to increment subresources: status: {} names: kind: PipelineRun plural: pipelineruns singular: pipelinerun categories: - tekton - tekton-pipelines shortNames: - pr - prs scope: Namespaced conversion: strategy: Webhook webhook: conversionReviewVersions: ["v1beta1", "v1"] clientConfig: service: name: tekton-pipelines-webhook namespace: tekton-pipelines --- # Copyright 2022 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # https://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: apiextensions.k8s.io/v1 kind: CustomResourceDefinition metadata: name: resolutionrequests.resolution.tekton.dev labels: resolution.tekton.dev/release: devel spec: group: resolution.tekton.dev scope: Namespaced names: kind: ResolutionRequest plural: resolutionrequests singular: resolutionrequest categories: - tekton - tekton-pipelines shortNames: - resolutionrequest - resolutionrequests versions: - name: v1alpha1 served: true deprecated: true storage: false subresources: status: {} schema: openAPIV3Schema: type: object # One can use x-kubernetes-preserve-unknown-fields: true # at the root of the schema (and inside any properties, additionalProperties) # to get the traditional CRD behaviour that nothing is pruned, despite # setting spec.preserveUnknownProperties: false. # # See https://kubernetes.io/blog/2019/06/20/crd-structural-schema/ # See issue: https://github.com/knative/serving/issues/912 x-kubernetes-preserve-unknown-fields: true additionalPrinterColumns: - name: Succeeded type: string jsonPath: ".status.conditions[?(@.type=='Succeeded')].status" - name: Reason type: string jsonPath: ".status.conditions[?(@.type=='Succeeded')].reason" - name: v1beta1 served: true storage: true subresources: status: {} schema: openAPIV3Schema: type: object # One can use x-kubernetes-preserve-unknown-fields: true # at the root of the schema (and inside any properties, additionalProperties) # to get the traditional CRD behaviour that nothing is pruned, despite # setting spec.preserveUnknownProperties: false. # # See https://kubernetes.io/blog/2019/06/20/crd-structural-schema/ # See issue: https://github.com/knative/serving/issues/912 x-kubernetes-preserve-unknown-fields: true additionalPrinterColumns: - name: OwnerKind type: string jsonPath: ".metadata.ownerReferences[0].kind" - name: Owner type: string jsonPath: ".metadata.ownerReferences[0].name" - name: Succeeded type: string jsonPath: ".status.conditions[?(@.type=='Succeeded')].status" - name: Reason type: string jsonPath: ".status.conditions[?(@.type=='Succeeded')].reason" - name: StartTime type: string jsonPath: .metadata.creationTimestamp - name: EndTime type: string jsonPath: .status.conditions[?(@.type=='Succeeded')].lastTransitionTime conversion: strategy: Webhook webhook: conversionReviewVersions: ["v1alpha1", "v1beta1"] clientConfig: service: name: tekton-pipelines-webhook namespace: tekton-pipelines --- # Copyright 2020 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # https://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: apiextensions.k8s.io/v1 kind: CustomResourceDefinition metadata: name: runs.tekton.dev labels: app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines pipeline.tekton.dev/release: "v0.46.0" version: "v0.46.0" spec: group: tekton.dev preserveUnknownFields: false versions: - name: v1alpha1 served: true storage: true schema: openAPIV3Schema: type: object # One can use x-kubernetes-preserve-unknown-fields: true # at the root of the schema (and inside any properties, additionalProperties) # to get the traditional CRD behaviour that nothing is pruned, despite # setting spec.preserveUnknownProperties: false. # # See https://kubernetes.io/blog/2019/06/20/crd-structural-schema/ # See issue: https://github.com/knative/serving/issues/912 x-kubernetes-preserve-unknown-fields: true additionalPrinterColumns: - name: Succeeded type: string jsonPath: ".status.conditions[?(@.type==\"Succeeded\")].status" - name: Reason type: string jsonPath: ".status.conditions[?(@.type==\"Succeeded\")].reason" - name: StartTime type: date jsonPath: .status.startTime - name: CompletionTime type: date jsonPath: .status.completionTime # Opt into the status subresource so metadata.generation # starts to increment subresources: status: {} names: kind: Run plural: runs singular: run categories: - tekton - tekton-pipelines scope: Namespaced --- # Copyright 2019 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # https://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: apiextensions.k8s.io/v1 kind: CustomResourceDefinition metadata: name: tasks.tekton.dev labels: app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines pipeline.tekton.dev/release: "v0.46.0" version: "v0.46.0" spec: group: tekton.dev preserveUnknownFields: false versions: - name: v1beta1 served: true storage: true schema: openAPIV3Schema: type: object # One can use x-kubernetes-preserve-unknown-fields: true # at the root of the schema (and inside any properties, additionalProperties) # to get the traditional CRD behaviour that nothing is pruned, despite # setting spec.preserveUnknownProperties: false. # # See https://kubernetes.io/blog/2019/06/20/crd-structural-schema/ # See issue: https://github.com/knative/serving/issues/912 x-kubernetes-preserve-unknown-fields: true # Opt into the status subresource so metadata.generation # starts to increment subresources: status: {} - name: v1 served: true storage: false schema: openAPIV3Schema: type: object # TODO(#1461): Add OpenAPIV3 schema # OpenAPIV3 schema allows Kubernetes to perform validation on the schema fields # and use the schema in tooling such as `kubectl explain`. # Using "x-kubernetes-preserve-unknown-fields: true" # at the root of the schema (or within it) allows arbitrary fields. # We currently perform our own validation separately. # See https://kubernetes.io/docs/tasks/extend-kubernetes/custom-resources/custom-resource-definitions/#specifying-a-structural-schema # for more info. x-kubernetes-preserve-unknown-fields: true # Opt into the status subresource so metadata.generation # starts to increment subresources: status: {} names: kind: Task plural: tasks singular: task categories: - tekton - tekton-pipelines scope: Namespaced conversion: strategy: Webhook webhook: conversionReviewVersions: ["v1beta1", "v1"] clientConfig: service: name: tekton-pipelines-webhook namespace: tekton-pipelines --- # Copyright 2019 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # https://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: apiextensions.k8s.io/v1 kind: CustomResourceDefinition metadata: name: taskruns.tekton.dev labels: app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines pipeline.tekton.dev/release: "v0.46.0" version: "v0.46.0" spec: group: tekton.dev preserveUnknownFields: false versions: - name: v1beta1 served: true storage: true schema: openAPIV3Schema: type: object # One can use x-kubernetes-preserve-unknown-fields: true # at the root of the schema (and inside any properties, additionalProperties) # to get the traditional CRD behaviour that nothing is pruned, despite # setting spec.preserveUnknownProperties: false. # # See https://kubernetes.io/blog/2019/06/20/crd-structural-schema/ # See issue: https://github.com/knative/serving/issues/912 x-kubernetes-preserve-unknown-fields: true additionalPrinterColumns: - name: Succeeded type: string jsonPath: ".status.conditions[?(@.type==\"Succeeded\")].status" - name: Reason type: string jsonPath: ".status.conditions[?(@.type==\"Succeeded\")].reason" - name: StartTime type: date jsonPath: .status.startTime - name: CompletionTime type: date jsonPath: .status.completionTime # Opt into the status subresource so metadata.generation # starts to increment subresources: status: {} - name: v1 served: true storage: false schema: openAPIV3Schema: type: object # One can use x-kubernetes-preserve-unknown-fields: true # at the root of the schema (and inside any properties, additionalProperties) # to get the traditional CRD behaviour that nothing is pruned, despite # setting spec.preserveUnknownProperties: false. # # See https://kubernetes.io/blog/2019/06/20/crd-structural-schema/ # See issue: https://github.com/knative/serving/issues/912 x-kubernetes-preserve-unknown-fields: true additionalPrinterColumns: - name: Succeeded type: string jsonPath: ".status.conditions[?(@.type==\"Succeeded\")].status" - name: Reason type: string jsonPath: ".status.conditions[?(@.type==\"Succeeded\")].reason" - name: StartTime type: date jsonPath: .status.startTime - name: CompletionTime type: date jsonPath: .status.completionTime # Opt into the status subresource so metadata.generation # starts to increment subresources: status: {} names: kind: TaskRun plural: taskruns singular: taskrun categories: - tekton - tekton-pipelines shortNames: - tr - trs scope: Namespaced conversion: strategy: Webhook webhook: conversionReviewVersions: ["v1beta1", "v1"] clientConfig: service: name: tekton-pipelines-webhook namespace: tekton-pipelines --- # Copyright 2022 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # https://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: apiextensions.k8s.io/v1 kind: CustomResourceDefinition metadata: name: verificationpolicies.tekton.dev labels: app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines pipeline.tekton.dev/release: "v0.46.0" version: "v0.46.0" spec: group: tekton.dev versions: - name: v1alpha1 served: true storage: true schema: openAPIV3Schema: type: object # One can use x-kubernetes-preserve-unknown-fields: true # at the root of the schema (and inside any properties, additionalProperties) # to get the traditional CRD behaviour that nothing is pruned, despite # setting spec.preserveUnknownProperties: false. # # See https://kubernetes.io/blog/2019/06/20/crd-structural-schema/ # See issue: https://github.com/knative/serving/issues/912 x-kubernetes-preserve-unknown-fields: true names: kind: VerificationPolicy plural: verificationpolicies singular: verificationpolicy categories: - tekton - tekton-pipelines scope: Namespaced --- # Copyright 2020 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # https://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: v1 kind: Secret metadata: name: webhook-certs namespace: tekton-pipelines labels: app.kubernetes.io/component: webhook app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines pipeline.tekton.dev/release: "v0.46.0" # The data is populated at install time. --- apiVersion: admissionregistration.k8s.io/v1 kind: ValidatingWebhookConfiguration metadata: name: validation.webhook.pipeline.tekton.dev labels: app.kubernetes.io/component: webhook app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines pipeline.tekton.dev/release: "v0.46.0" webhooks: - admissionReviewVersions: ["v1"] clientConfig: service: name: tekton-pipelines-webhook namespace: tekton-pipelines failurePolicy: Fail sideEffects: None name: validation.webhook.pipeline.tekton.dev --- apiVersion: admissionregistration.k8s.io/v1 kind: MutatingWebhookConfiguration metadata: name: webhook.pipeline.tekton.dev labels: app.kubernetes.io/component: webhook app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines pipeline.tekton.dev/release: "v0.46.0" webhooks: - admissionReviewVersions: ["v1"] clientConfig: service: name: tekton-pipelines-webhook namespace: tekton-pipelines failurePolicy: Fail sideEffects: None name: webhook.pipeline.tekton.dev --- apiVersion: admissionregistration.k8s.io/v1 kind: ValidatingWebhookConfiguration metadata: name: config.webhook.pipeline.tekton.dev labels: app.kubernetes.io/component: webhook app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines pipeline.tekton.dev/release: "v0.46.0" webhooks: - admissionReviewVersions: ["v1"] clientConfig: service: name: tekton-pipelines-webhook namespace: tekton-pipelines failurePolicy: Fail sideEffects: None name: config.webhook.pipeline.tekton.dev objectSelector: matchLabels: app.kubernetes.io/part-of: tekton-pipelines --- # Copyright 2019-2022 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # https://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRole metadata: name: tekton-aggregate-edit labels: app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines rbac.authorization.k8s.io/aggregate-to-edit: "true" rbac.authorization.k8s.io/aggregate-to-admin: "true" rules: - apiGroups: - tekton.dev resources: - tasks - taskruns - pipelines - pipelineruns - runs - customruns verbs: - create - delete - deletecollection - get - list - patch - update - watch --- # Copyright 2019-2022 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # https://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRole metadata: name: tekton-aggregate-view labels: app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines rbac.authorization.k8s.io/aggregate-to-view: "true" rules: - apiGroups: - tekton.dev resources: - tasks - taskruns - pipelines - pipelineruns - runs - customruns verbs: - get - list - watch --- # Copyright 2019 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # https://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: v1 kind: ConfigMap metadata: name: config-defaults namespace: tekton-pipelines labels: app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines data: _example: | ################################ # # # EXAMPLE CONFIGURATION # # # ################################ # This block is not actually functional configuration, # but serves to illustrate the available configuration # options and document them in a way that is accessible # to users that `kubectl edit` this config map. # # These sample configuration options may be copied out of # this example block and unindented to be in the data block # to actually change the configuration. # default-timeout-minutes contains the default number of # minutes to use for TaskRun and PipelineRun, if none is specified. default-timeout-minutes: "60" # 60 minutes # default-service-account contains the default service account name # to use for TaskRun and PipelineRun, if none is specified. default-service-account: "default" # default-managed-by-label-value contains the default value given to the # "app.kubernetes.io/managed-by" label applied to all Pods created for # TaskRuns. If a user's requested TaskRun specifies another value for this # label, the user's request supercedes. default-managed-by-label-value: "tekton-pipelines" # default-pod-template contains the default pod template to use for # TaskRun and PipelineRun. If a pod template is specified on the # PipelineRun, the default-pod-template is merged with that one. # default-pod-template: # default-affinity-assistant-pod-template contains the default pod template # to use for affinity assistant pods. If a pod template is specified on the # PipelineRun, the default-affinity-assistant-pod-template is merged with # that one. # default-affinity-assistant-pod-template: # default-cloud-events-sink contains the default CloudEvents sink to be # used for TaskRun and PipelineRun, when no sink is specified. # Note that right now it is still not possible to set a PipelineRun or # TaskRun specific sink, so the default is the only option available. # If no sink is specified, no CloudEvent is generated # default-cloud-events-sink: # default-task-run-workspace-binding contains the default workspace # configuration provided for any Workspaces that a Task declares # but that a TaskRun does not explicitly provide. # default-task-run-workspace-binding: | # emptyDir: {} # default-max-matrix-combinations-count contains the default maximum number # of combinations from a Matrix, if none is specified. default-max-matrix-combinations-count: "256" # default-forbidden-env contains comma seperated environment variables that cannot be # overridden by podTemplate. default-forbidden-env: # default-resolver-type contains the default resolver type to be used in the cluster, # no default-resolver-type is specified by default default-resolver-type: --- # Copyright 2019 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # https://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: v1 kind: ConfigMap metadata: name: feature-flags namespace: tekton-pipelines labels: app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines data: # Setting this flag to "true" will prevent Tekton to create an # Affinity Assistant for every TaskRun sharing a PVC workspace # # The default behaviour is for Tekton to create Affinity Assistants # # See more in the workspace documentation about Affinity Assistant # https://github.com/tektoncd/pipeline/blob/main/docs/workspaces.md#affinity-assistant-and-specifying-workspace-order-in-a-pipeline # or https://github.com/tektoncd/pipeline/pull/2630 for more info. disable-affinity-assistant: "true" # Setting this flag to "true" will prevent Tekton scanning attached # service accounts and injecting any credentials it finds into your # Steps. # # The default behaviour currently is for Tekton to search service # accounts for secrets matching a specified format and automatically # mount those into your Steps. # # Note: setting this to "true" will prevent PipelineResources from # working. # # See https://github.com/tektoncd/pipeline/issues/2791 for more # info. disable-creds-init: "false" # Setting this flag to "false" will stop Tekton from waiting for a # TaskRun's sidecar containers to be running before starting the first # step. This will allow Tasks to be run in environments that don't # support the DownwardAPI volume type, but may lead to unintended # behaviour if sidecars are used. # # See https://github.com/tektoncd/pipeline/issues/4937 for more info. await-sidecar-readiness: "true" # This option should be set to false when Pipelines is running in a # cluster that does not use injected sidecars such as Istio. Setting # it to false should decrease the time it takes for a TaskRun to start # running. For clusters that use injected sidecars, setting this # option to false can lead to unexpected behavior. # # See https://github.com/tektoncd/pipeline/issues/2080 for more info. running-in-environment-with-injected-sidecars: "true" # Setting this flag to "true" will require that any Git SSH Secret # offered to Tekton must have known_hosts included. # # See https://github.com/tektoncd/pipeline/issues/2981 for more # info. require-git-ssh-secret-known-hosts: "false" # Setting this flag to "true" enables the use of Tekton OCI bundle. # This is an experimental feature and thus should still be considered # an alpha feature. enable-tekton-oci-bundles: "false" # Setting this flag will determine which gated features are enabled. # Acceptable values are "stable", "beta", or "alpha". enable-api-fields: "stable" # Setting this flag to "true" enables CloudEvents for CustomRuns and Runs, as long as a # CloudEvents sink is configured in the config-defaults config map send-cloudevents-for-runs: "false" # Setting this flag to "enforce" will enforce verification of tasks/pipeline. Failing to verify # will fail the taskrun/pipelinerun. "warn" will only log the err message and "skip" # will skip the whole verification resource-verification-mode: "skip" # Setting this flag to "true" enables populating the "provenance" field in TaskRun # and PipelineRun status. This field contains metadata about resources used # in the TaskRun/PipelineRun such as the source from where a remote Task/Pipeline # definition was fetched. enable-provenance-in-status: "false" # Setting this flag will determine the version for custom tasks created by PipelineRuns. # Acceptable values are "v1beta1" and "v1alpha1". # The default is "v1beta1". custom-task-version: "v1beta1" # Setting this flag will determine how Tekton pipelines will handle non-falsifiable provenance. # If set to "spire", then SPIRE will be used to ensure non-falsifiable provenance. # If set to "none", then Tekton will not have non-falsifiable provenance. # This is an experimental feature and thus should still be considered an alpha feature. enforce-nonfalsifiablity: "none" --- # Copyright 2021 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # https://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: v1 kind: ConfigMap metadata: name: pipelines-info namespace: tekton-pipelines labels: app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines data: # Contains pipelines version which can be queried by external # tools such as CLI. Elevated permissions are already given to # this ConfigMap such that even if we don't have access to # other resources in the namespace we still can have access to # this ConfigMap. version: "v0.46.0" --- # Copyright 2020 Tekton Authors LLC # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # https://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: v1 kind: ConfigMap metadata: name: config-leader-election namespace: tekton-pipelines labels: app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines data: _example: | ################################ # # # EXAMPLE CONFIGURATION # # # ################################ # This block is not actually functional configuration, # but serves to illustrate the available configuration # options and document them in a way that is accessible # to users that `kubectl edit` this config map. # # These sample configuration options may be copied out of # this example block and unindented to be in the data block # to actually change the configuration. # lease-duration is how long non-leaders will wait to try to acquire the # lock; 15 seconds is the value used by core kubernetes controllers. lease-duration: "60s" # renew-deadline is how long a leader will try to renew the lease before # giving up; 10 seconds is the value used by core kubernetes controllers. renew-deadline: "40s" # retry-period is how long the leader election client waits between tries of # actions; 2 seconds is the value used by core kubernetes controllers. retry-period: "10s" # buckets is the number of buckets used to partition key space of each # Reconciler. If this number is M and the replica number of the controller # is N, the N replicas will compete for the M buckets. The owner of a # bucket will take care of the reconciling for the keys partitioned into # that bucket. buckets: "1" --- # Copyright 2019 Tekton Authors LLC # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # https://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: v1 kind: ConfigMap metadata: name: config-logging namespace: tekton-pipelines labels: app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines data: zap-logger-config: | { "level": "info", "development": false, "sampling": { "initial": 100, "thereafter": 100 }, "outputPaths": ["stdout"], "errorOutputPaths": ["stderr"], "encoding": "json", "encoderConfig": { "timeKey": "timestamp", "levelKey": "severity", "nameKey": "logger", "callerKey": "caller", "messageKey": "message", "stacktraceKey": "stacktrace", "lineEnding": "", "levelEncoder": "", "timeEncoder": "iso8601", "durationEncoder": "", "callerEncoder": "" } } # Log level overrides loglevel.controller: "info" loglevel.webhook: "info" --- # Copyright 2019 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # https://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: v1 kind: ConfigMap metadata: name: config-observability namespace: tekton-pipelines labels: app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines data: _example: | ################################ # # # EXAMPLE CONFIGURATION # # # ################################ # This block is not actually functional configuration, # but serves to illustrate the available configuration # options and document them in a way that is accessible # to users that `kubectl edit` this config map. # # These sample configuration options may be copied out of # this example block and unindented to be in the data block # to actually change the configuration. # metrics.backend-destination field specifies the system metrics destination. # It supports either prometheus (the default) or stackdriver. # Note: Using Stackdriver will incur additional charges. metrics.backend-destination: prometheus # metrics.stackdriver-project-id field specifies the Stackdriver project ID. This # field is optional. When running on GCE, application default credentials will be # used and metrics will be sent to the cluster's project if this field is # not provided. metrics.stackdriver-project-id: "<your stackdriver project id>" # metrics.allow-stackdriver-custom-metrics indicates whether it is allowed # to send metrics to Stackdriver using "global" resource type and custom # metric type. Setting this flag to "true" could cause extra Stackdriver # charge. If metrics.backend-destination is not Stackdriver, this is # ignored. metrics.allow-stackdriver-custom-metrics: "false" metrics.taskrun.level: "task" metrics.taskrun.duration-type: "histogram" metrics.pipelinerun.level: "pipeline" metrics.pipelinerun.duration-type: "histogram" --- # Copyright 2020 Tekton Authors LLC # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # https://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: v1 kind: ConfigMap metadata: name: config-registry-cert namespace: tekton-pipelines labels: app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines # data: # # Registry's self-signed certificate # cert: | --- # Copyright 2022 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # https://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: v1 kind: ConfigMap metadata: name: config-spire namespace: tekton-pipelines labels: app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines data: _example: | ################################ # # # EXAMPLE CONFIGURATION # # # ################################ # This block is not actually functional configuration, # but serves to illustrate the available configuration # options and document them in a way that is accessible # to users that `kubectl edit` this config map. # # These sample configuration options may be copied out of # this example block and unindented to be in the data block # to actually change the configuration. # # spire-trust-domain specifies the SPIRE trust domain to use. # spire-trust-domain: "example.org" # # spire-socket-path specifies the SPIRE agent socket for SPIFFE workload API. # spire-socket-path: "unix:///spiffe-workload-api/spire-agent.sock" # # spire-server-addr specifies the SPIRE server address for workload/node registration. # spire-server-addr: "spire-server.spire.svc.cluster.local:8081" # # spire-node-alias-prefix specifies the SPIRE node alias prefix to use. # spire-node-alias-prefix: "/tekton-node/" --- # Copyright 2019 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # http://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: apps/v1 kind: Deployment metadata: name: tekton-pipelines-controller namespace: tekton-pipelines labels: app.kubernetes.io/name: controller app.kubernetes.io/component: controller app.kubernetes.io/instance: default app.kubernetes.io/version: "v0.46.0" app.kubernetes.io/part-of: tekton-pipelines # tekton.dev/release value replaced with inputs.params.versionTag in pipeline/tekton/publish.yaml pipeline.tekton.dev/release: "v0.46.0" # labels below are related to istio and should not be used for resource lookup version: "v0.46.0" spec: replicas: 1 selector: matchLabels: app.kubernetes.io/name: controller app.kubernetes.io/component: controller app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines template: metadata: labels: app.kubernetes.io/name: controller app.kubernetes.io/component: controller app.kubernetes.io/instance: default app.kubernetes.io/version: "v0.46.0" app.kubernetes.io/part-of: tekton-pipelines # tekton.dev/release value replaced with inputs.params.versionTag in pipeline/tekton/publish.yaml pipeline.tekton.dev/release: "v0.46.0" # labels below are related to istio and should not be used for resource lookup app: tekton-pipelines-controller version: "v0.46.0" spec: serviceAccountName: tekton-pipelines-controller containers: - name: tekton-pipelines-controller image: registry.cn-hangzhou.aliyuncs.com/acs-demo-ns/tckton-pipeline-controller:v0.46.0 args: [ # These images are built on-demand by `ko resolve` and are replaced # by image references by digest. "-entrypoint-image", "registry.cn-hangzhou.aliyuncs.com/acs-demo-ns/tckton-pipeline-entrypoint:v0.46.0", "-nop-image", "registry.cn-hangzhou.aliyuncs.com/acs-demo-ns/tckton-pipeline-nop:v0.46.0", "-sidecarlogresults-image", "registry.cn-hangzhou.aliyuncs.com/acs-demo-ns/tckton-pipeline-sidecarlogresults:v0.46.0", "-workingdirinit-image", "registry.cn-hangzhou.aliyuncs.com/acs-demo-ns/tckton-pipeline-workingdirinit:v0.46.0", # The shell image must allow root in order to create directories and copy files to PVCs. # cgr.dev/chainguard/busybox as of April 14 2022 # image shall not contains tag, so it will be supported on a runtime like cri-o "-shell-image", "busybox:1.36", # for script mode to work with windows we need a powershell image # pinning to nanoserver tag as of July 15 2021 "-shell-image-win", "mcr.microsoft.com/powershell:nanoserver@sha256:b6d5ff841b78bdf2dfed7550000fd4f3437385b8fa686ec0f010be24777654d6"] volumeMounts: - name: config-logging mountPath: /etc/config-logging - name: config-registry-cert mountPath: /etc/config-registry-cert env: - name: SYSTEM_NAMESPACE value: tekton-pipelines # If you are changing these names, you will also need to update # the controller's Role in 200-role.yaml to include the new # values in the "configmaps" "get" rule. - name: CONFIG_DEFAULTS_NAME value: config-defaults - name: CONFIG_LOGGING_NAME value: config-logging - name: CONFIG_OBSERVABILITY_NAME value: config-observability - name: CONFIG_ARTIFACT_BUCKET_NAME value: config-artifact-bucket - name: CONFIG_ARTIFACT_PVC_NAME value: config-artifact-pvc - name: CONFIG_FEATURE_FLAGS_NAME value: feature-flags - name: CONFIG_LEADERELECTION_NAME value: config-leader-election - name: CONFIG_SPIRE value: config-spire - name: SSL_CERT_FILE value: /etc/config-registry-cert/cert - name: SSL_CERT_DIR value: /etc/ssl/certs - name: METRICS_DOMAIN value: tekton.dev/pipeline # The following variables can be uncommented with correct values to enable Jaeger tracing #- name: OTEL_EXPORTER_JAEGER_ENDPOINT # value: http://jaeger-collector.jaeger:14268/api/traces #- name: OTEL_EXPORTER_JAEGER_USER # value: username #- name: OTEL_EXPORTER_JAEGER_PASSWORD # value: password securityContext: allowPrivilegeEscalation: false capabilities: drop: - "ALL" # User 65532 is the nonroot user ID runAsUser: 65532 runAsGroup: 65532 runAsNonRoot: true seccompProfile: type: RuntimeDefault ports: - name: metrics containerPort: 9090 - name: profiling containerPort: 8008 - name: probes containerPort: 8080 livenessProbe: httpGet: path: /health port: probes scheme: HTTP initialDelaySeconds: 5 periodSeconds: 10 timeoutSeconds: 5 readinessProbe: httpGet: path: /readiness port: probes scheme: HTTP initialDelaySeconds: 5 periodSeconds: 10 timeoutSeconds: 5 volumes: - name: config-logging configMap: name: config-logging - name: config-registry-cert configMap: name: config-registry-cert --- apiVersion: v1 kind: Service metadata: labels: app.kubernetes.io/name: controller app.kubernetes.io/component: controller app.kubernetes.io/instance: default app.kubernetes.io/version: "v0.46.0" app.kubernetes.io/part-of: tekton-pipelines # tekton.dev/release value replaced with inputs.params.versionTag in pipeline/tekton/publish.yaml pipeline.tekton.dev/release: "v0.46.0" # labels below are related to istio and should not be used for resource lookup app: tekton-pipelines-controller version: "v0.46.0" name: tekton-pipelines-controller namespace: tekton-pipelines spec: ports: - name: http-metrics port: 9090 protocol: TCP targetPort: 9090 - name: http-profiling port: 8008 targetPort: 8008 - name: probes port: 8080 selector: app.kubernetes.io/name: controller app.kubernetes.io/component: controller app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines --- # Copyright 2022 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # http://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: v1 kind: Namespace metadata: name: tekton-pipelines-resolvers labels: app.kubernetes.io/component: resolvers app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines pod-security.kubernetes.io/enforce: restricted --- # Copyright 2022 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # https://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. kind: ClusterRole apiVersion: rbac.authorization.k8s.io/v1 metadata: # ClusterRole for resolvers to monitor and update resolutionrequests. name: tekton-pipelines-resolvers-resolution-request-updates labels: app.kubernetes.io/component: resolvers app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines rules: - apiGroups: ["resolution.tekton.dev"] resources: ["resolutionrequests", "resolutionrequests/status"] verbs: ["get", "list", "watch", "update", "patch"] - apiGroups: ["tekton.dev"] resources: ["tasks", "pipelines"] verbs: ["get", "list"] # Read-only access to these. - apiGroups: [""] resources: ["secrets"] verbs: ["get", "list", "watch"] --- # Copyright 2022 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # https://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. kind: Role apiVersion: rbac.authorization.k8s.io/v1 metadata: name: tekton-pipelines-resolvers-namespace-rbac namespace: tekton-pipelines-resolvers labels: app.kubernetes.io/component: resolvers app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines rules: # Needed to watch and load configuration and secret data. - apiGroups: [""] resources: ["configmaps", "secrets"] verbs: ["get", "list", "update", "watch"] # This is needed by leader election to run the controller in HA. - apiGroups: ["coordination.k8s.io"] resources: ["leases"] verbs: ["get", "list", "create", "update", "delete", "patch", "watch"] --- # Copyright 2022 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # https://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: v1 kind: ServiceAccount metadata: name: tekton-pipelines-resolvers namespace: tekton-pipelines-resolvers labels: app.kubernetes.io/component: resolvers app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines --- # Copyright 2021 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # https://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRoleBinding metadata: name: tekton-pipelines-resolvers namespace: tekton-pipelines-resolvers labels: app.kubernetes.io/component: resolvers app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines subjects: - kind: ServiceAccount name: tekton-pipelines-resolvers namespace: tekton-pipelines-resolvers roleRef: kind: ClusterRole name: tekton-pipelines-resolvers-resolution-request-updates apiGroup: rbac.authorization.k8s.io --- # Copyright 2021 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # https://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: rbac.authorization.k8s.io/v1 kind: RoleBinding metadata: name: tekton-pipelines-resolvers-namespace-rbac namespace: tekton-pipelines-resolvers labels: app.kubernetes.io/component: resolvers app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines subjects: - kind: ServiceAccount name: tekton-pipelines-resolvers namespace: tekton-pipelines-resolvers roleRef: kind: Role name: tekton-pipelines-resolvers-namespace-rbac apiGroup: rbac.authorization.k8s.io --- # Copyright 2022 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # https://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: v1 kind: ConfigMap metadata: name: bundleresolver-config namespace: tekton-pipelines-resolvers labels: app.kubernetes.io/component: resolvers app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines data: # the default service account name to use for bundle requests. default-service-account: "default" # The default layer kind in the bundle image. default-kind: "task" --- # Copyright 2022 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # https://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: v1 kind: ConfigMap metadata: name: cluster-resolver-config namespace: tekton-pipelines-resolvers labels: app.kubernetes.io/component: resolvers app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines data: # The default kind to fetch. default-kind: "task" # The default namespace to look for resources in. default-namespace: "" # An optional comma-separated list of namespaces which the resolver is allowed to access. Defaults to empty, meaning all namespaces are allowed. allowed-namespaces: "" # An optional comma-separated list of namespaces which the resolver is blocked from accessing. Defaults to empty, meaning all namespaces are allowed. blocked-namespaces: "" --- # Copyright 2019 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # https://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: v1 kind: ConfigMap metadata: name: resolvers-feature-flags namespace: tekton-pipelines-resolvers labels: app.kubernetes.io/component: resolvers app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines data: # Setting this flag to "true" enables remote resolution of Tekton OCI bundles. enable-bundles-resolver: "true" # Setting this flag to "true" enables remote resolution of tasks and pipelines via the Tekton Hub. enable-hub-resolver: "true" # Setting this flag to "true" enables remote resolution of tasks and pipelines from Git repositories. enable-git-resolver: "true" # Setting this flag to "true" enables remote resolution of tasks and pipelines from other namespaces within the cluster. enable-cluster-resolver: "true" --- # Copyright 2020 Tekton Authors LLC # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # https://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: v1 kind: ConfigMap metadata: name: config-leader-election namespace: tekton-pipelines-resolvers labels: app.kubernetes.io/component: resolvers app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines data: _example: | ################################ # # # EXAMPLE CONFIGURATION # # # ################################ # This block is not actually functional configuration, # but serves to illustrate the available configuration # options and document them in a way that is accessible # to users that `kubectl edit` this config map. # # These sample configuration options may be copied out of # this example block and unindented to be in the data block # to actually change the configuration. # lease-duration is how long non-leaders will wait to try to acquire the # lock; 15 seconds is the value used by core kubernetes controllers. lease-duration: "60s" # renew-deadline is how long a leader will try to renew the lease before # giving up; 10 seconds is the value used by core kubernetes controllers. renew-deadline: "40s" # retry-period is how long the leader election client waits between tries of # actions; 2 seconds is the value used by core kubernetes controllers. retry-period: "10s" # buckets is the number of buckets used to partition key space of each # Reconciler. If this number is M and the replica number of the controller # is N, the N replicas will compete for the M buckets. The owner of a # bucket will take care of the reconciling for the keys partitioned into # that bucket. buckets: "1" --- # Copyright 2019 Tekton Authors LLC # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # https://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: v1 kind: ConfigMap metadata: name: config-logging namespace: tekton-pipelines-resolvers labels: app.kubernetes.io/component: resolvers app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines data: zap-logger-config: | { "level": "info", "development": false, "sampling": { "initial": 100, "thereafter": 100 }, "outputPaths": ["stdout"], "errorOutputPaths": ["stderr"], "encoding": "json", "encoderConfig": { "timeKey": "timestamp", "levelKey": "severity", "nameKey": "logger", "callerKey": "caller", "messageKey": "message", "stacktraceKey": "stacktrace", "lineEnding": "", "levelEncoder": "", "timeEncoder": "iso8601", "durationEncoder": "", "callerEncoder": "" } } # Log level overrides loglevel.controller: "info" loglevel.webhook: "info" --- # Copyright 2022 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # https://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: v1 kind: ConfigMap metadata: name: config-observability namespace: tekton-pipelines-resolvers labels: app.kubernetes.io/component: resolvers app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines data: _example: | ################################ # # # EXAMPLE CONFIGURATION # # # ################################ # This block is not actually functional configuration, # but serves to illustrate the available configuration # options and document them in a way that is accessible # to users that `kubectl edit` this config map. # # These sample configuration options may be copied out of # this example block and unindented to be in the data block # to actually change the configuration. # metrics.backend-destination field specifies the system metrics destination. # It supports either prometheus (the default) or stackdriver. # Note: Using stackdriver will incur additional charges metrics.backend-destination: prometheus # metrics.request-metrics-backend-destination specifies the request metrics # destination. If non-empty, it enables queue proxy to send request metrics. # Currently supported values: prometheus, stackdriver. metrics.request-metrics-backend-destination: prometheus # metrics.stackdriver-project-id field specifies the stackdriver project ID. This # field is optional. When running on GCE, application default credentials will be # used if this field is not provided. metrics.stackdriver-project-id: "<your stackdriver project id>" # metrics.allow-stackdriver-custom-metrics indicates whether it is allowed to send metrics to # Stackdriver using "global" resource type and custom metric type if the # metrics are not supported by "knative_revision" resource type. Setting this # flag to "true" could cause extra Stackdriver charge. # If metrics.backend-destination is not Stackdriver, this is ignored. metrics.allow-stackdriver-custom-metrics: "false" --- # Copyright 2022 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # https://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: v1 kind: ConfigMap metadata: name: git-resolver-config namespace: tekton-pipelines-resolvers labels: app.kubernetes.io/component: resolvers app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines data: # The maximum amount of time a single anonymous cloning resolution may take. fetch-timeout: "1m" # The git url to fetch the remote resource from when using anonymous cloning. default-url: "https://github.com/tektoncd/catalog.git" # The git revision to fetch the remote resource from with either anonymous cloning or the authenticated API. default-revision: "main" # The SCM type to use with the authenticated API. Can be github, gitlab, gitea, bitbucketserver, bitbucketcloud scm-type: "github" # The SCM server URL to use with the authenticated API. Not needed when using github.com, gitlab.com, or BitBucket Cloud server-url: "" # The Kubernetes secret containing the API token for the SCM provider. Required when using the authenticated API. api-token-secret-name: "" # The key in the API token secret containing the actual token. Required when using the authenticated API. api-token-secret-key: "" # The namespace containing the API token secret. Defaults to "default". api-token-secret-namespace: "default" # The default organization to look for repositories under when using the authenticated API, # if not specified in the resolver parameters. Optional. default-org: "" --- # Copyright 2022 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # https://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: v1 kind: ConfigMap metadata: name: hubresolver-config namespace: tekton-pipelines-resolvers labels: app.kubernetes.io/component: resolvers app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines data: # the default Tekton Hub catalog from where to pull the resource. default-tekton-hub-catalog: "Tekton" # the default Artifact Hub Task catalog from where to pull the resource. default-artifact-hub-task-catalog: "tekton-catalog-tasks" # the default Artifact Hub Pipeline catalog from where to pull the resource. default-artifact-hub-pipeline-catalog: "tekton-catalog-pipelines" # the default layer kind in the hub image. default-kind: "task" # the default hub source to pull the resource from. default-type: "artifact" --- # Copyright 2022 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # http://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: apps/v1 kind: Deployment metadata: name: tekton-pipelines-remote-resolvers namespace: tekton-pipelines-resolvers labels: app.kubernetes.io/name: resolvers app.kubernetes.io/component: resolvers app.kubernetes.io/instance: default app.kubernetes.io/version: "v0.46.0" app.kubernetes.io/part-of: tekton-pipelines # tekton.dev/release value replaced with inputs.params.versionTag in pipeline/tekton/publish.yaml pipeline.tekton.dev/release: "v0.46.0" # labels below are related to istio and should not be used for resource lookup version: "v0.46.0" spec: replicas: 1 selector: matchLabels: app.kubernetes.io/name: resolvers app.kubernetes.io/component: resolvers app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines template: metadata: labels: app.kubernetes.io/name: resolvers app.kubernetes.io/component: resolvers app.kubernetes.io/instance: default app.kubernetes.io/version: "v0.46.0" app.kubernetes.io/part-of: tekton-pipelines # tekton.dev/release value replaced with inputs.params.versionTag in pipeline/tekton/publish.yaml pipeline.tekton.dev/release: "v0.46.0" # labels below are related to istio and should not be used for resource lookup app: tekton-pipelines-resolvers version: "v0.46.0" spec: affinity: podAntiAffinity: preferredDuringSchedulingIgnoredDuringExecution: - podAffinityTerm: labelSelector: matchLabels: app.kubernetes.io/name: resolvers app.kubernetes.io/component: resolvers app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines topologyKey: kubernetes.io/hostname weight: 100 serviceAccountName: tekton-pipelines-resolvers containers: - name: controller image: registry.cn-hangzhou.aliyuncs.com/acs-demo-ns/tckton-pipeline-resolvers:v0.46.0 resources: requests: cpu: 100m memory: 100Mi limits: cpu: 1000m memory: 4Gi ports: - name: metrics containerPort: 9090 env: - name: SYSTEM_NAMESPACE value: tekton-pipelines-resolvers # If you are changing these names, you will also need to update # the controller's Role in 200-role.yaml to include the new # values in the "configmaps" "get" rule. - name: CONFIG_LOGGING_NAME value: config-logging - name: CONFIG_OBSERVABILITY_NAME value: config-observability - name: CONFIG_FEATURE_FLAGS_NAME value: feature-flags - name: CONFIG_LEADERELECTION_NAME value: config-leader-election - name: METRICS_DOMAIN value: tekton.dev/resolution # Override this env var to set a private hub api endpoint - name: ARTIFACT_HUB_API value: "https://artifacthub.io/" securityContext: allowPrivilegeEscalation: false readOnlyRootFilesystem: true runAsNonRoot: true capabilities: drop: - "ALL" seccompProfile: type: RuntimeDefault --- # Copyright 2020 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # https://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: autoscaling/v2 kind: HorizontalPodAutoscaler metadata: name: tekton-pipelines-webhook namespace: tekton-pipelines labels: app.kubernetes.io/name: webhook app.kubernetes.io/component: webhook app.kubernetes.io/instance: default app.kubernetes.io/version: "v0.46.0" app.kubernetes.io/part-of: tekton-pipelines # tekton.dev/release value replaced with inputs.params.versionTag in pipeline/tekton/publish.yaml pipeline.tekton.dev/release: "v0.46.0" # labels below are related to istio and should not be used for resource lookup version: "v0.46.0" spec: minReplicas: 1 maxReplicas: 5 scaleTargetRef: apiVersion: apps/v1 kind: Deployment name: tekton-pipelines-webhook metrics: - type: Resource resource: name: cpu target: type: Utilization averageUtilization: 100 --- # Copyright 2020 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # https://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: apps/v1 kind: Deployment metadata: # Note: the Deployment name must be the same as the Service name specified in # config/400-webhook-service.yaml. If you change this name, you must also # change the value of WEBHOOK_SERVICE_NAME below. name: tekton-pipelines-webhook namespace: tekton-pipelines labels: app.kubernetes.io/name: webhook app.kubernetes.io/component: webhook app.kubernetes.io/instance: default app.kubernetes.io/version: "v0.46.0" app.kubernetes.io/part-of: tekton-pipelines # tekton.dev/release value replaced with inputs.params.versionTag in pipeline/tekton/publish.yaml pipeline.tekton.dev/release: "v0.46.0" # labels below are related to istio and should not be used for resource lookup version: "v0.46.0" spec: selector: matchLabels: app.kubernetes.io/name: webhook app.kubernetes.io/component: webhook app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines template: metadata: labels: app.kubernetes.io/name: webhook app.kubernetes.io/component: webhook app.kubernetes.io/instance: default app.kubernetes.io/version: "v0.46.0" app.kubernetes.io/part-of: tekton-pipelines # tekton.dev/release value replaced with inputs.params.versionTag in pipeline/tekton/publish.yaml pipeline.tekton.dev/release: "v0.46.0" # labels below are related to istio and should not be used for resource lookup app: tekton-pipelines-webhook version: "v0.46.0" spec: affinity: podAntiAffinity: preferredDuringSchedulingIgnoredDuringExecution: - podAffinityTerm: labelSelector: matchLabels: app.kubernetes.io/name: webhook app.kubernetes.io/component: webhook app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines topologyKey: kubernetes.io/hostname weight: 100 serviceAccountName: tekton-pipelines-webhook containers: - name: webhook # This is the Go import path for the binary that is containerized # and substituted here. image: registry.cn-hangzhou.aliyuncs.com/acs-demo-ns/tckton-pipeline-webhook:v0.46.0 # Resource request required for autoscaler to take any action for a metric resources: requests: cpu: 100m memory: 100Mi limits: cpu: 500m memory: 500Mi env: - name: SYSTEM_NAMESPACE value: tekton-pipelines # If you are changing these names, you will also need to update # the webhook's Role in 200-role.yaml to include the new # values in the "configmaps" "get" rule. - name: CONFIG_LOGGING_NAME value: config-logging - name: CONFIG_OBSERVABILITY_NAME value: config-observability - name: CONFIG_LEADERELECTION_NAME value: config-leader-election - name: CONFIG_FEATURE_FLAGS_NAME value: feature-flags # If you change WEBHOOK_PORT, you will also need to change the # containerPort "https-webhook" to the same value. - name: WEBHOOK_PORT value: "8443" # if you change WEBHOOK_ADMISSION_CONTROLLER_NAME, you will also need to update # the webhooks.name in 500-webhooks.yaml to include the new names of admission webhooks. # Additionally, you will also need to change the resource names (metadata.name) of # "MutatingWebhookConfiguration" and "ValidatingWebhookConfiguration" in 500-webhooks.yaml # to reflect the change in the name of the admission webhook. # Followed by changing the webhook's Role in 200-clusterrole.yaml to update the "resourceNames" of # "mutatingwebhookconfigurations" and "validatingwebhookconfigurations" resources. - name: WEBHOOK_ADMISSION_CONTROLLER_NAME value: webhook.pipeline.tekton.dev - name: WEBHOOK_SERVICE_NAME value: tekton-pipelines-webhook - name: WEBHOOK_SECRET_NAME value: webhook-certs - name: METRICS_DOMAIN value: tekton.dev/pipeline securityContext: allowPrivilegeEscalation: false capabilities: drop: - "ALL" # User 65532 is the distroless nonroot user ID runAsUser: 65532 runAsGroup: 65532 runAsNonRoot: true seccompProfile: type: RuntimeDefault ports: - name: metrics containerPort: 9090 - name: profiling containerPort: 8008 # This must match the value of the environment variable WEBHOOK_PORT. - name: https-webhook containerPort: 8443 - name: probes containerPort: 8080 livenessProbe: httpGet: path: /health port: probes scheme: HTTP initialDelaySeconds: 5 periodSeconds: 10 timeoutSeconds: 5 readinessProbe: httpGet: path: /readiness port: probes scheme: HTTP initialDelaySeconds: 5 periodSeconds: 10 timeoutSeconds: 5 --- apiVersion: v1 kind: Service metadata: labels: app.kubernetes.io/name: webhook app.kubernetes.io/component: webhook app.kubernetes.io/instance: default app.kubernetes.io/version: "v0.46.0" app.kubernetes.io/part-of: tekton-pipelines # tekton.dev/release value replaced with inputs.params.versionTag in pipeline/tekton/publish.yaml pipeline.tekton.dev/release: "v0.46.0" # labels below are related to istio and should not be used for resource lookup app: tekton-pipelines-webhook version: "v0.46.0" name: tekton-pipelines-webhook namespace: tekton-pipelines spec: ports: # Define metrics and profiling for them to be accessible within service meshes. - name: http-metrics port: 9090 targetPort: 9090 - name: http-profiling port: 8008 targetPort: 8008 - name: https-webhook port: 443 targetPort: https-webhook - name: probes port: 8080 selector: app.kubernetes.io/name: webhook app.kubernetes.io/component: webhook app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines ---通过kubectl执行以下命令,安装Pipelines v0.46.0版本。
kubectl apply -f tekton-v0.46.0.yaml预期输出:
namespace/tekton-pipelines created clusterrole.rbac.authorization.k8s.io/tekton-pipelines-controller-cluster-access created clusterrole.rbac.authorization.k8s.io/tekton-pipelines-controller-tenant-access created clusterrole.rbac.authorization.k8s.io/tekton-pipelines-webhook-cluster-access created role.rbac.authorization.k8s.io/tekton-pipelines-controller created role.rbac.authorization.k8s.io/tekton-pipelines-webhook created role.rbac.authorization.k8s.io/tekton-pipelines-leader-election created role.rbac.authorization.k8s.io/tekton-pipelines-info created serviceaccount/tekton-pipelines-controller created serviceaccount/tekton-pipelines-webhook created ......安装完成后新增三个Operator组件。
tekton-pipelines-controller
tekton-pipelines-webhook
tekton-pipelines-remote-resolver
执行以下命令,查看组件的安装状态。
查看tekton-pipelines安装状态。
kubectl get deploy -n tekton-pipelines预期输出:
NAME READY UP-TO-DATE AVAILABLE AGE tekton-pipelines-controller 1/1 1 1 155m tekton-pipelines-webhook 1/1 1 1 155m查看tekton-pipelines-resolvers安装状态。
kubectl get deploy -n tekton-pipelines-resolvers预期输出:
NAME READY UP-TO-DATE AVAILABLE AGE tekton-pipelines-remote-resolvers 1/1 1 1 155m可以看到以上组件均已安装成功。
说明下文为了加速组件的安装,将组件的镜像转储到阿里云ACR中,镜像内容未发生变化。
(可选)步骤二:安装Tekton Dashboard
Tekton提供了一个基础的Dashboard(v0.42.0),您可以按需进行安装。
以下安装会通过一个公网SLB来提供前端服务。
使用以下内容,创建dashboard.yaml。
展开查看dashboard.yaml
apiVersion: v1 kind: Namespace metadata: labels: app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-dashboard name: tekton-dashboard --- apiVersion: apiextensions.k8s.io/v1 kind: CustomResourceDefinition metadata: labels: app.kubernetes.io/component: dashboard app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-dashboard name: extensions.dashboard.tekton.dev spec: group: dashboard.tekton.dev names: categories: - tekton - tekton-dashboard kind: Extension plural: extensions shortNames: - ext - exts preserveUnknownFields: false scope: Namespaced versions: - additionalPrinterColumns: - jsonPath: .spec.apiVersion name: API version type: string - jsonPath: .spec.name name: Kind type: string - jsonPath: .spec.displayname name: Display name type: string - jsonPath: .metadata.creationTimestamp name: Age type: date name: v1alpha1 schema: openAPIV3Schema: type: object x-kubernetes-preserve-unknown-fields: true served: true storage: true subresources: status: {} --- apiVersion: v1 kind: ServiceAccount metadata: labels: app.kubernetes.io/component: dashboard app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-dashboard name: tekton-dashboard namespace: tekton-pipelines --- apiVersion: rbac.authorization.k8s.io/v1 kind: Role metadata: labels: app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-dashboard name: tekton-dashboard-info namespace: tekton-pipelines rules: - apiGroups: - "" resourceNames: - dashboard-info resources: - configmaps verbs: - get --- apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRole metadata: labels: app.kubernetes.io/component: dashboard app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-dashboard name: tekton-dashboard-backend rules: - apiGroups: - apiextensions.k8s.io resources: - customresourcedefinitions verbs: - get - list - apiGroups: - security.openshift.io resources: - securitycontextconstraints verbs: - use - apiGroups: - tekton.dev resources: - clustertasks verbs: - get - list - watch - apiGroups: - triggers.tekton.dev resources: - clusterinterceptors - clustertriggerbindings verbs: - get - list - watch - apiGroups: - "" resources: - serviceaccounts verbs: - get - list - watch - apiGroups: - dashboard.tekton.dev resources: - extensions verbs: - create - update - delete - patch - apiGroups: - tekton.dev resources: - clustertasks verbs: - create - update - delete - patch - apiGroups: - triggers.tekton.dev resources: - clusterinterceptors - clustertriggerbindings verbs: - create - update - delete - patch --- apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRole metadata: labels: app.kubernetes.io/component: dashboard app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-dashboard name: tekton-dashboard-tenant rules: - apiGroups: - dashboard.tekton.dev resources: - extensions verbs: - get - list - watch - apiGroups: - "" resources: - events - namespaces - pods - pods/log verbs: - get - list - watch - apiGroups: - tekton.dev resources: - tasks - taskruns - pipelines - pipelineruns - customruns verbs: - get - list - watch - apiGroups: - triggers.tekton.dev resources: - eventlisteners - interceptors - triggerbindings - triggers - triggertemplates verbs: - get - list - watch - apiGroups: - tekton.dev resources: - tasks - taskruns - pipelines - pipelineruns - customruns verbs: - create - update - delete - patch - apiGroups: - triggers.tekton.dev resources: - eventlisteners - interceptors - triggerbindings - triggers - triggertemplates verbs: - create - update - delete - patch --- apiVersion: rbac.authorization.k8s.io/v1 kind: RoleBinding metadata: labels: app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-dashboard name: tekton-dashboard-info namespace: tekton-pipelines roleRef: apiGroup: rbac.authorization.k8s.io kind: Role name: tekton-dashboard-info subjects: - apiGroup: rbac.authorization.k8s.io kind: Group name: system:authenticated --- apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRoleBinding metadata: labels: app.kubernetes.io/component: dashboard app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-dashboard rbac.dashboard.tekton.dev/subject: tekton-dashboard name: tekton-dashboard-backend roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: tekton-dashboard-backend subjects: - kind: ServiceAccount name: tekton-dashboard namespace: tekton-pipelines --- apiVersion: v1 data: version: v0.42.0 kind: ConfigMap metadata: labels: app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-dashboard name: dashboard-info namespace: tekton-pipelines --- apiVersion: v1 kind: Service metadata: labels: app: tekton-dashboard app.kubernetes.io/component: dashboard app.kubernetes.io/instance: default app.kubernetes.io/name: dashboard app.kubernetes.io/part-of: tekton-dashboard app.kubernetes.io/version: v0.42.0 dashboard.tekton.dev/release: v0.42.0 version: v0.42.0 name: tekton-dashboard namespace: tekton-pipelines spec: ports: - name: http port: 9097 protocol: TCP targetPort: 9097 selector: app.kubernetes.io/component: dashboard app.kubernetes.io/instance: default app.kubernetes.io/name: dashboard app.kubernetes.io/part-of: tekton-dashboard type: LoadBalancer --- apiVersion: apps/v1 kind: Deployment metadata: labels: app: tekton-dashboard app.kubernetes.io/component: dashboard app.kubernetes.io/instance: default app.kubernetes.io/name: dashboard app.kubernetes.io/part-of: tekton-dashboard app.kubernetes.io/version: v0.42.0 dashboard.tekton.dev/release: v0.42.0 version: v0.42.0 name: tekton-dashboard namespace: tekton-pipelines spec: replicas: 1 selector: matchLabels: app.kubernetes.io/component: dashboard app.kubernetes.io/instance: default app.kubernetes.io/name: dashboard app.kubernetes.io/part-of: tekton-dashboard template: metadata: labels: app: tekton-dashboard app.kubernetes.io/component: dashboard app.kubernetes.io/instance: default app.kubernetes.io/name: dashboard app.kubernetes.io/part-of: tekton-dashboard app.kubernetes.io/version: v0.42.0 name: tekton-dashboard spec: containers: - args: - --port=9097 - --logout-url= - --pipelines-namespace=tekton-pipelines - --triggers-namespace=tekton-pipelines - --read-only=false - --log-level=info - --log-format=json - --namespace= - --namespaces= - --stream-logs=true - --external-logs= env: - name: INSTALLED_NAMESPACE valueFrom: fieldRef: fieldPath: metadata.namespace image: registry.cn-hangzhou.aliyuncs.com/acs-demo-ns/tekton-dashboard:v0.42.0 livenessProbe: httpGet: path: /health port: 9097 name: tekton-dashboard ports: - containerPort: 9097 readinessProbe: httpGet: path: /readiness port: 9097 securityContext: allowPrivilegeEscalation: false capabilities: drop: - ALL runAsGroup: 65532 runAsNonRoot: true runAsUser: 65532 seccompProfile: type: RuntimeDefault serviceAccountName: tekton-dashboard volumes: [] --- --- apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRoleBinding metadata: labels: app.kubernetes.io/component: dashboard app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-dashboard rbac.dashboard.tekton.dev/subject: tekton-dashboard name: tekton-dashboard-tenant roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: tekton-dashboard-tenant subjects: - kind: ServiceAccount name: tekton-dashboard namespace: tekton-pipelines执行以下命令,安装dashboard v0.42.0版本。
kubectl apply -f dashboard.yaml执行以下命令,查看Dashboard的安装状态。
查看
tekton-pipelines命名空间中所有包含dashboard名称的Deployment资源。kubectl get deploy -n tekton-pipelines | grep dashboard预期输出:
tekton-dashboard 1/1 1 1 21m查看
tekton-pipelines命名空间中所有包含dashboard名称的Service资源。kubectl get svc -n tekton-pipelines | grep dashboard预期输出:
tekton-dashboard LoadBalancer 192.168.206.174 your-endpoint 9097/TCP 21m预期输出表明Dashboard安装成功。
通过Endpoint访问Dashboard。
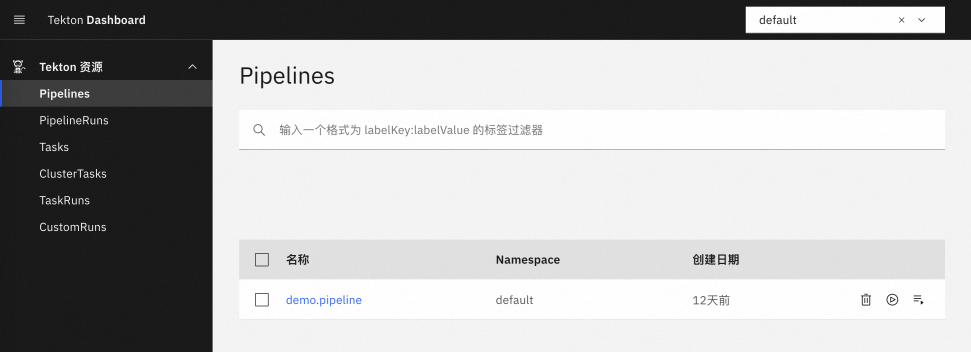
(可选)步骤三:安装Tekton CLI
Tekton提供了一个基于kubectl的客户端扩展,您可以按需安装。具体操作,请参见参考Tekton。
操作平台为macOS
brew install tektoncd-cli操作平台为Windows
tkn is available on Windows via Chocolatey: choco install tektoncd-cli --confirm
Tekton基于GitOps的持续集成(CI)和持续交付(CD)
场景一:结合阿里云ACR和GitHub进行镜像构建
以下示例定义一个Tekton Pipeline进行镜像构建。
定义一个Task将代码克隆至共享存储(NAS)中。
定义一个 Task,利用Kaniko对NAS(网络附加存储)中的代码进行容器镜像构建,并将构建好的镜像推送到阿里云容器镜像服务ACR仓库中。
前提条件
已创建一个代码仓库。本示例使用GitHub仓库
https://gitee.com/AliyunContainerService/tekton-demo.git。示例仓库中包含一个基础的Hello World HTTP服务和Dockerfile。
操作步骤
执行以下命令,创建镜像仓库密钥。
示例中使用的是阿里云ACR个人版,通过Secret的方式来保存密钥,后续的镜像构建阶段和应用部署阶段都使用此Secret。
说明ACS集成了ACR镜像仓库免密插件,您也可以通过免密插件的方式来代替这一步骤。关于如何使用免密插件,请参见免密拉取ACR镜像。
kubectl create secret docker-registry docker-regcred \ --docker-server=registry.cn-beijing.aliyuncs.com \ --docker-username=yourUserName \ --docker-password=yourPassword新建Role和ServiceAccount。
使用以下内容,创建account.yaml。
展开查看account.yaml
--- apiVersion: v1 kind: ServiceAccount metadata: name: pipeline-account --- apiVersion: v1 kind: Secret metadata: name: kube-api-secret annotations: kubernetes.io/service-account.name: pipeline-account type: kubernetes.io/service-account-token --- kind: Role apiVersion: rbac.authorization.k8s.io/v1 metadata: name: pipeline-role --- apiVersion: rbac.authorization.k8s.io/v1 kind: RoleBinding metadata: name: pipeline-role-binding roleRef: apiGroup: rbac.authorization.k8s.io kind: Role name: pipeline-role subjects: - kind: ServiceAccount name: pipeline-account执行以下命令,创建Role和ServiceAccount。
kubectl apply -f account.yaml预期输出:
serviceaccount/pipeline-account created secret/kube-api-secret created role.rbac.authorization.k8s.io/pipeline-role created rolebinding.rbac.authorization.k8s.io/pipeline-role-binding created
定义克隆代码的任务git-clone.yaml。
说明进行Git Clone的作业采用ACS BestEffort资源来降低运行成本,通过labels内指定
alibabacloud.com/compute-qos: "best-effort"进行设置。git-clone任务会将代码下载到指定目录,后续将通过挂载NAS共享存储的方式让不同Task进行代码数据的交互。
克隆代码的任务只包含一个Step,将代码下载至声明的
workspaces共享空间下。展开查看克隆代码YAML
apiVersion: tekton.dev/v1 kind: Task metadata: name: git-clone labels: alibabacloud.com/compute-qos: "best-effort" # 使用BestEffort型资源。 spec: workspaces: - name: output description: The git repo will be cloned onto the volume backing this workspace params: - name: repo_url description: git repo url to clone type: string - name: revision description: git revision to checkout (branch, tag, sha, ref…) type: string default: master - name: submodules description: defines if the resource should initialize and fetch the submodules type: string default: "true" - name: depth description: performs a shallow clone where only the most recent commit(s) will be fetched type: string default: "1" - name: sslVerify description: defines if http.sslVerify should be set to true or false in the global git config type: string default: "true" - name: subdirectory description: subdirectory inside the "output" workspace to clone the git repo into type: string default: "" - name: deleteExisting description: clean out the contents of the repo's destination directory (if it already exists) before trying to clone the repo there type: string default: "false" results: - name: commit description: The precise commit SHA that was fetched by this Task steps: - name: clone image: registry.cn-hangzhou.aliyuncs.com/acs-demo-ns/tckton-pipeline-git-init:latest securityContext: runAsUser: 0 # This needs root, and git-init is nonroot by default script: | CHECKOUT_DIR="$(workspaces.output.path)/$(params.subdirectory)" cleandir() { # Delete any existing contents of the repo directory if it exists. # # We don't just "rm -rf $CHECKOUT_DIR" because $CHECKOUT_DIR might be "/" # or the root of a mounted volume. if [[ -d "$CHECKOUT_DIR" ]] ; then # Delete non-hidden files and directories rm -rf "$CHECKOUT_DIR"/* # Delete files and directories starting with . but excluding .. rm -rf "$CHECKOUT_DIR"/.[!.]* # Delete files and directories starting with .. plus any other character rm -rf "$CHECKOUT_DIR"/..?* fi } if [[ "$(params.deleteExisting)" == "true" ]] ; then cleandir fi /ko-app/git-init \ -url "$(params.repo_url)" \ -revision "$(params.revision)" \ -path "$CHECKOUT_DIR" \ -sslVerify="$(params.sslVerify)" \ -submodules="$(params.submodules)" \ -depth="$(params.depth)" cd "$CHECKOUT_DIR" RESULT_SHA="$(git rev-parse HEAD | tr -d '\n')" EXIT_CODE="$?" if [ "$EXIT_CODE" != 0 ] then exit $EXIT_CODE fi # Make sure we don't add a trailing newline to the result! echo -n "$RESULT_SHA" > $(results.commit.path)定义镜像构建任务tasks.yaml。
说明进行镜像构建的作业采用ACS任务型资源来降低运行成本,通过labels内指定
alibabacloud.com/copmute-qos: "best-effort"进行设置。任务通过Kaniko进行镜像构建:
将共享空间内的代码进行镜像构建并推送到ACR仓库。
镜像信息输出到结果中。
展开查看tasks.yaml
apiVersion: tekton.dev/v1beta1 kind: Task metadata: name: kaniko labels: alibabacloud.com/compute-qos: "best-effort" # 使用BestEffort型资源。 annotations: tekton.dev/tags: image-build tekton.dev/displayName: "Build and upload container image using Kaniko" tekton.dev/platforms: "linux/amd64,linux/arm64,linux/ppc64le" spec: description: >- This Task builds a simple Dockerfile with kaniko and pushes to a registry. This Task stores the image name and digest as results, allowing Tekton Chains to pick up that an image was built & sign it. params: - name: IMAGE description: Name (reference) of the image to build. - name: DOCKERFILE description: Path to the Dockerfile to build. default: ./Dockerfile - name: CONTEXT description: The build context used by Kaniko. default: ./ - name: EXTRA_ARGS type: array default: [--ignore-path=/product_uuid] - name: BUILDER_IMAGE description: The image on which builds will run default: registry.cn-hangzhou.aliyuncs.com/acs-demo-ns/kaniko-executor:v1.8.1 workspaces: - name: source description: Holds the context and Dockerfile - name: dockerconfig description: Includes a docker `config.json` optional: true mountPath: /kaniko/.docker results: - name: IMAGE_DIGEST description: Digest of the image just built. - name: IMAGE_URL description: URL of the image just built. steps: - name: build-and-push workingDir: $(workspaces.source.path) image: $(params.BUILDER_IMAGE) args: - $(params.EXTRA_ARGS) - --dockerfile=$(params.DOCKERFILE) - --context=$(workspaces.source.path)/$(params.CONTEXT) # The user does not need to care the workspace and the source. - --destination=$(params.IMAGE) - --digest-file=$(results.IMAGE_DIGEST.path) # kaniko assumes it is running as root, which means this example fails on platforms # that default to run containers as random uid (like OpenShift). Adding this securityContext # makes it explicit that it needs to run as root. securityContext: runAsUser: 0 - name: write-url image: docker.io/library/bash:5.1.4@sha256:c523c636b722339f41b6a431b44588ab2f762c5de5ec3bd7964420ff982fb1d9 script: | set -e image="$(params.IMAGE)" echo -n "${image}" | tee "$(results.IMAGE_URL.path)"
定义Pipeline流水线。
通过定义Pipeline将原子Task代码克隆和镜像构建组装成一条工作流,并对任务的执行顺序、参数传递进行描述。
展开查看pipeline.yaml
apiVersion: tekton.dev/v1 kind: Pipeline metadata: name: "demo.pipeline" spec: params: - name: image-registry default: registry.cn-beijing.aliyuncs.com/acs-demo-ns - name: image-repo-name type: string - name: repo_url type: string - name: repo_revision type: string workspaces: - name: git-source - name: docker-regcred tasks: - name: fetch-from-git taskRef: name: git-clone params: - name: repo_url value: $(params.repo_url) - name: revision value: $(params.repo_revision) - name: deleteExisting value: "true" workspaces: - name: output workspace: git-source - name: build-image runAfter: [fetch-from-git] taskRef: name: kaniko params: - name: IMAGE value: $(params.image-registry)/$(params.image-repo-name):$(tasks.fetch-from-git.results.commit) - name: CONTEXT value: src - name: DOCKERFILE value: $(workspaces.source.path)/src/Dockerfile workspaces: - name: source workspace: git-source - name: dockerconfig workspace: docker-regcred定义pipelineRun.yaml。
说明示例中通过volumeClaimTemplate进行静态NAS的方式作为共享存储,您也可以使用动态创建NAS的方式进行自动创建,具体操作,请参见NAS存储卷。
name字段使用generateName,避免重名流水线被忽略问题。通过
volumeClaimTemplate声明存储(静态NAS方式)。csi.alibabacloud.com/mountpoint表示NAS的访问地址。storageClassName为ACS中NAS的定义alibaba-cloud-nas。
通过
taskRunTemplate设置Task Pod的资源规格,这里我们对镜像构建任务的Pod设置CPU和内存分别为0.5Core和2GiB。挂载镜像密钥
docker-regcred。展开查看pipelineRun.yaml
apiVersion: tekton.dev/v1 kind: PipelineRun metadata: generateName: tekton-kn-sample- spec: pipelineRef: name: "demo.pipeline" taskRunTemplate: serviceAccountName: "pipeline-account" taskRunSpecs: - pipelineTaskName: build-image computeResources: requests: cpu: 500m memory: 2Gi workspaces: - name: git-source volumeClaimTemplate: metadata: annotations: csi.alibabacloud.com/mountpoint: "your-nas-endpoint" spec: accessModes: - ReadWriteMany storageClassName: alibaba-cloud-nas resources: requests: storage: 30Gi - name: docker-regcred secret: defaultMode: 420 items: - key: .dockerconfigjson path: config.json secretName: docker-regcred params: - name: repo_url value: https://gitee.com/AliyunContainerService/tekton-demo.git - name: repo_revision value: main - name: image-registry value: registry.cn-beijing.aliyuncs.com/acs-demo-ns - name: image-repo-name value: hello-world
分别执行以下命令,创建镜像构建任务、Pipeline流水线和PipelineRun。
kubectl apply -f tasks.yaml kubectl apply -f pipeline.yaml kubectl create -f pipelineRun.yaml通过Tekton CLI查看工作流的执行状态。
当所有任务执行完成后,PipelineRun会进入Succeeded状态。
# 输入 tkn pr list #期望输出 NAME STARTED DURATION STATUS tekton-kn-sample-xdcr7 # 输入 tkn pr describe tekton-kn-sample-xdcr7 # 期望输出 Name: tekton-kn-sample-xdcr7 Namespace: default Pipeline Ref: demo.pipeline Service Account: pipeline-account Labels: tekton.dev/pipeline=demo.pipeline Status STARTED DURATION STATUS 4 hours ago 2m30s Succeeded Timeouts Pipeline: 1h0m0s Params NAME VALUE ∙ repo_url https://gitee.com/AliyunContainerService/tekton-demo.git ∙ repo_revision main ∙ image-registry registry.cn-beijing.aliyuncs.com/acs-demo-ns ∙ image-repo-name hello-world ∙ image-tag v0.1 Workspaces NAME SUB PATH WORKSPACE BINDING ∙ git-source --- VolumeClaimTemplate ∙ docker-regcred --- Secret (secret=docker-regcred,item=.dockerconfigjson=config.json) Taskruns NAME TASK NAME STARTED DURATION STATUS ∙ tekton-kn-sample-xdcr7-build-image build-image 4 hours ago 2m5s Succeeded ∙ tekton-kn-sample-xdcr7-fetch-from-git fetch-from-git 4 hours ago 25s Succeeded
关于容错机制
上述示例CI是一个典型的短时作业场景,因此全部采用BestEffort实例运行。
BestEffort实例的特点是在批量运行时可以保持高吞吐量和低成本,在少数情况下,BestEffort实例会被驱逐重建。建议如下:
对Tekton的Task、Pipeline进行容错机制的设置。
Tekton提供了在Pipeline Spec中设置任务的超时(timeout)和失败重试(retries)的能力。
timeout:默认值是60分钟,可以根据每个任务类型的特点设置合适的超时时间。
retries:默认值为0,即不进行重试,可以根据任务特点设置合适的重试次数。
修改Pipeline设置任务超时和重试次数,并重新部署。
展开查看pipeline.yaml
apiVersion: tekton.dev/v1 kind: Pipeline metadata: name: "demo.pipeline" spec: params: - name: image-registry default: registry.cn-beijing.aliyuncs.com/acs-demo-ns - name: image-repo-name type: string - name: repo_url type: string - name: repo_revision type: string workspaces: - name: git-source - name: docker-regcred tasks: - name: fetch-from-git taskRef: name: git-clone timeout: "0h0m10s" # 代码克隆任务超时时间5秒,主要用于模拟失败情况。 retries: 2 # 当失败时最多重试两次。 params: - name: repo_url value: $(params.repo_url) - name: revision value: $(params.repo_revision) - name: deleteExisting value: "true" workspaces: - name: output workspace: git-source - name: build-image runAfter: [fetch-from-git] taskRef: name: kaniko timeout: "0h5m0s" retries: 2 params: - name: IMAGE value: $(params.image-registry)/$(params.image-repo-name):$(tasks.fetch-from-git.results.commit) - name: CONTEXT value: src - name: DOCKERFILE value: $(workspaces.source.path)/src/Dockerfile workspaces: - name: source workspace: git-source - name: dockerconfig workspace: docker-regcred执行以下命令,查看任务超时的自动重试。
kubectl get po预期输出:
tekton-kn-sample-nfn4h-fetch-from-git-pod 0/1 Init:StartError 0 1m13s tekton-kn-sample-nfn4h-fetch-from-git-pod-retry1 0/1 Completed 0 1m22s可以看到Tekton会在失败时自动拉起一个
retry-{index}后缀的Pod进行重试。
场景二:结合KubeVela进行服务交付
通过Tekton结合Kubevela来进行服务交付。关于KubeVela的安装和最佳实践,请参见KubeVela最佳实践。
服务交付主要进行以下步骤:
KubeVela中创建应用Trigger Webhook用于接收Tekton的部署请求。
编排Tekton Pipelines,在构建镜像步骤后添加部署任务。
部署任务内通过一个Python脚本来完成部署触发和部署状态轮询。
操作步骤
在KubeVela中创建Trigger Webhook。
在VelaUX中对应用创建Trigger Webhook。
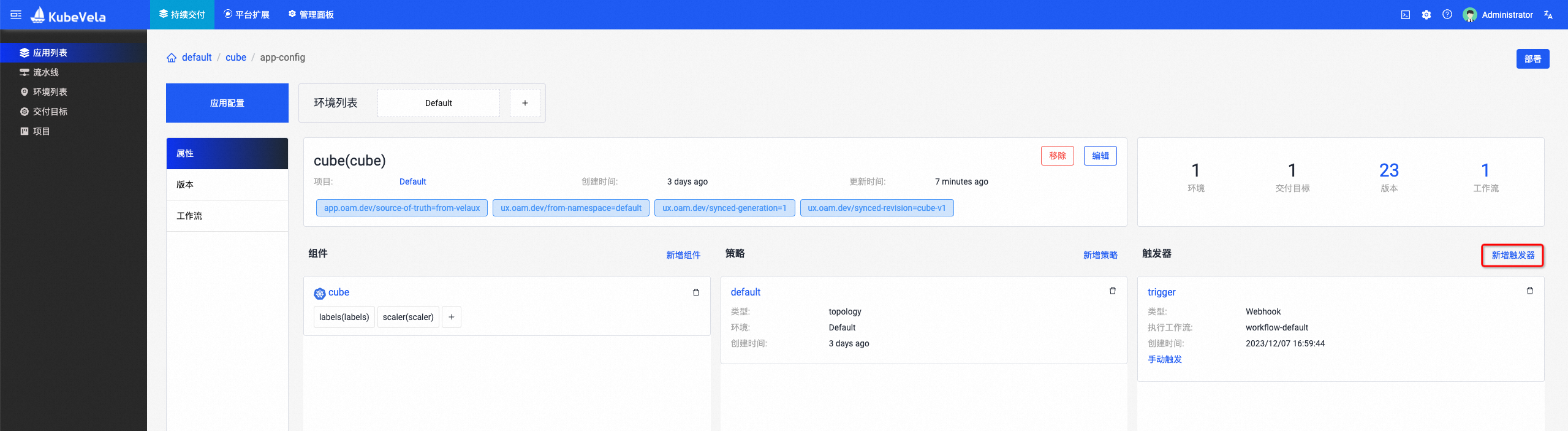
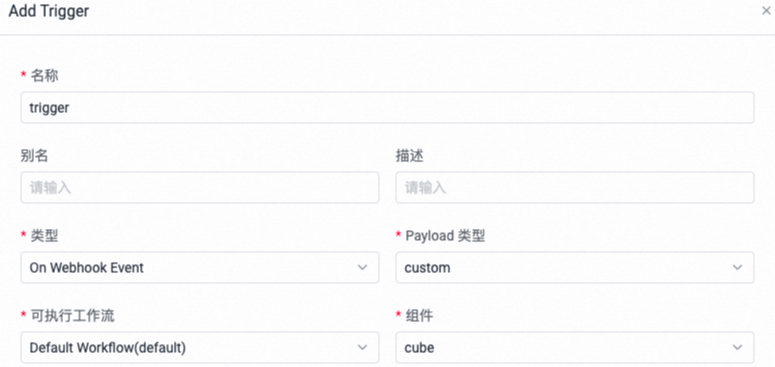
配置字段:
类型:On Webhook Event
Payload 类型:custom
查看Trigger Webhook请求地址。
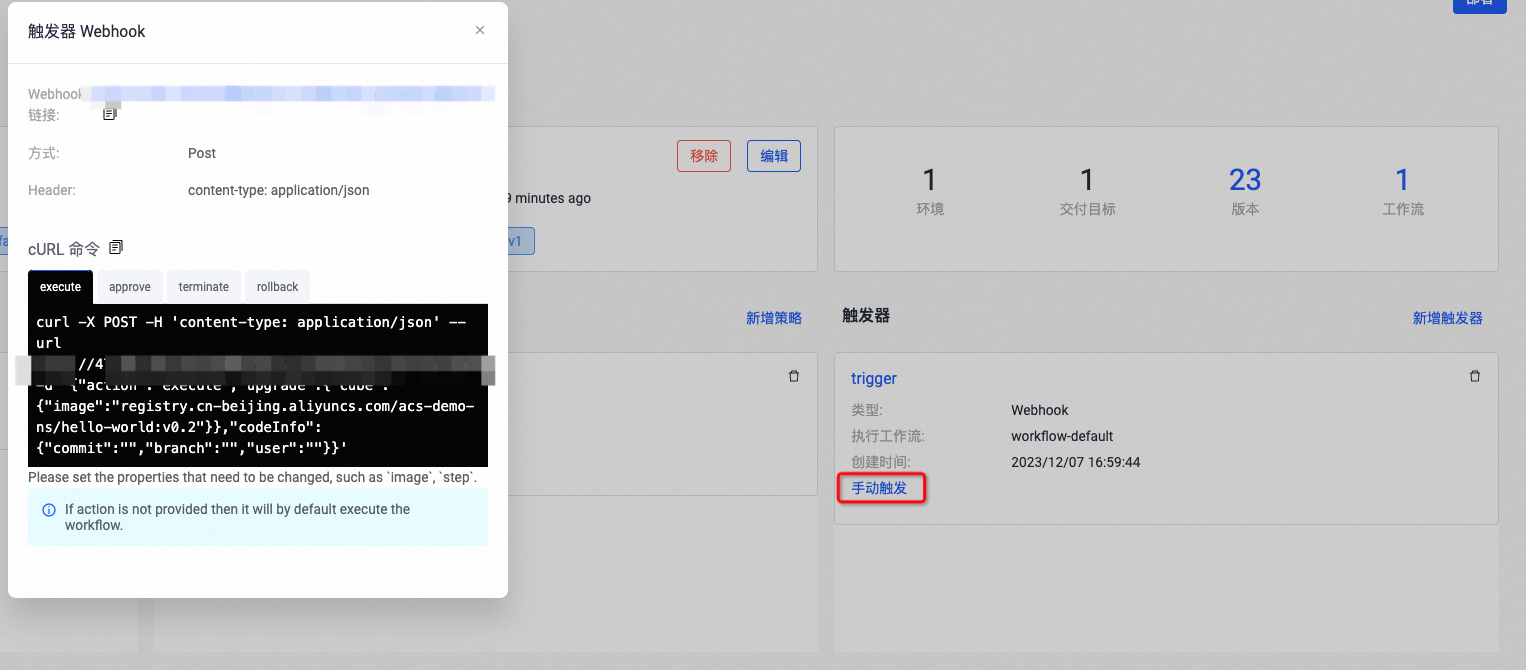
获取KubeVela的API Token。
返回结果中的
accessToken为后续查询发布状态的API Token。# 请求 curl -H Content-Type:application/json -X POST -d '{"username": "admin", "password":"your password"}' http://your-velaux-url:8000/api/v1/auth/login #预期返回 { "user": { "createTime": "0001-01-01T00:00:00Z", "lastLoginTime": "0001-01-01T00:00:00Z", "name": "admin", "email": "xxx", "disabled": false }, "accessToken": "xxx", "refreshToken": "xxx" }
定义服务部署任务。
部署任务通过Script方式以Python脚本完成了一次触发KubeVela和等待部署状态的任务,详细流程如下:
发起HTTP请求触发前置准备中创建好的Webhook,入参为克隆代码产出的代码Commit和构建任务产出的镜像地址。
通过API Token请求VelaUX OpenAPI轮询发布状态,直到运行成功或者超时退出。
展开查看YAML
apiVersion: tekton.dev/v1beta1 kind: Task metadata: name: kubevela-trigger labels: alibabacloud.com/compute-qos: "best-effort" spec: description: >- This Task is used to trigger to deploy application, with the revision of code commitId and image build from kaniko params: - name: image description: full url of the image - name: trigger_token description: token of the webhook - name: commit description: commit id of the code - name: velaux_url description: web server url of kubevela - name: velaux_token description: token of the velaux webserver - name: app_name description: vela app name - name: app_namespace description: namespace of vela app workspaces: - name: source description: Holds the context and Dockerfile steps: - name: deploy image: python:3.10.1-alpine3.15 script: | #!/usr/bin/env python """This script will trigger kubevela""" import json import sys import http.client import socket import time webhook_url = "/api/v1/webhook/$(params.trigger_token)" data = {"action":"execute","upgrade":{"cube":{"image":"$(params.image)"}},"codeInfo":{"commit":"$(params.commit)","branch":"","user":""}} print("Sending request to trigger webhook to deploy new image ") print(data) conn = http.client.HTTPConnection("$(params.velaux_url)") conn.request( "POST", webhook_url, body=json.dumps(data), headers={ "Accept": "application/json", "Content-Type": "application/json", }) resp = conn.getresponse() revison = "" if not str(resp.status).startswith("2"): print("Error: %d" % (resp.status)) print(resp.read()) sys.exit(1) else: resp_data = json.loads(resp.read()) print(resp_data) revision = resp_data["version"] authHeader = "Bearer $(params.velaux_token)" query_revision_url = "/v1/namespaces/$(params.app_namespace)/applications/$(params.app_name)" while 1: time.sleep(3) conn = http.client.HTTPConnection("$(params.velaux_url)") conn.request( "GET", query_revision_url, headers={ "Accept": "application/json, application/xml", "Authorization": authHeader, }) query_resp = conn.getresponse() if not str(query_resp.status).startswith("2"): print("Error: %d" % (query_resp.status)) print(query_resp.read()) continue else: query_resp_data = json.loads(query_resp.read()) print(query_resp_data) status = query_resp_data["status"]["workflow"]["status"] if status == "succeeded": print("succeeded to deploy application") break参数
说明
commit代码的CommitID,为克隆任务的输出。
image构建好的镜像完整地址,为构建任务的输出。
velaux_urlVelaUX的可访问地址。
velaux_token步骤1的accessToken。
trigger_token步骤1应用的Trigger Webhook Token。
app_nameKubeVela中目标应用的名称。
app_namespaceKubeVela中目标应用的Namespace。
调整Pipeline,添加部署任务。
在Pipeline中新增
deploy-app任务,并且通过Tekton Results API的方式从前置的任务中获取commit和镜像信息。关于Results的更多信息,请参见using-results。commit:$(tasks.fetch-from-git.results.commit)image:$(tasks.build-image.results.IMAGE_URL)
展开查看Pipeline YAML
apiVersion: tekton.dev/v1 kind: Pipeline metadata: name: "demo.pipeline" spec: params: - name: image-registry default: registry.cn-beijing.aliyuncs.com/acs-demo-ns - name: image-repo-name type: string - name: repo_url type: string - name: repo_revision type: string - name: trigger_token type: string - name: velaux_url type: string - name: velaux_token type: string - name: app_name type: string - name: app_namespace type: string workspaces: - name: git-source - name: docker-regcred tasks: - name: fetch-from-git taskRef: name: git-clone timeout: "0h5m0s" retries: 2 params: - name: repo_url value: $(params.repo_url) - name: revision value: $(params.repo_revision) - name: deleteExisting value: "true" workspaces: - name: output workspace: git-source - name: build-image runAfter: [fetch-from-git] taskRef: name: kaniko timeout: "0h5m0s" retries: 2 params: - name: IMAGE value: $(params.image-registry)/$(params.image-repo-name):$(tasks.fetch-from-git.results.commit) - name: CONTEXT value: src - name: DOCKERFILE value: $(workspaces.source.path)/src/Dockerfile workspaces: - name: source workspace: git-source - name: dockerconfig workspace: docker-regcred - name: deploy-app runAfter: [build-image] taskRef: name: kubevela-trigger timeout: "0h5m0s" retries: 2 params: - name: image value: $(tasks.build-image.results.IMAGE_URL) - name: commit value: $(tasks.fetch-from-git.results.commit) - name: trigger_token value: $(params.trigger_token) - name: velaux_url value: $(params.velaux_url) - name: velaux_token value: $(params.velaux_token) - name: app_name value: $(params.app_name) - name: app_namespace value: $(params.app_namespace) workspaces: - name: source workspace: git-source调整PipelineRun,添加部署任务。
展开查看PipelineRun YAML
--- apiVersion: tekton.dev/v1 kind: PipelineRun metadata: generateName: tekton-kn-sample- spec: pipelineRef: name: "demo.pipeline" taskRunTemplate: serviceAccountName: 'pipeline-account' workspaces: - name: git-source volumeClaimTemplate: metadata: annotations: csi.alibabacloud.com/mountpoint: "your-nas-endpoint" spec: accessModes: - ReadWriteMany storageClassName: alibaba-cloud-nas resources: requests: storage: 30Gi - name: docker-regcred secret: defaultMode: 420 items: - key: .dockerconfigjson path: config.json secretName: docker-regcred params: - name: repo_url value: https://gitee.com/AliyunContainerService/tekton-demo.git - name: repo_revision value: main - name: image-registry value: registry.cn-beijing.aliyuncs.com/acs-demo-ns - name: image-repo-name value: hello-world - name: trigger_token value: your-velaux-webhook-token - name: velaux_url value: your-velaux-url - name: velaux_token value: your-velaux-accessToken - name: app_name value: cube - name: app_namespace value: default提交至集群执行工作流。
方式一:通过kubectl命令查看工作流状态。
# 提交执行 kubectl create -f pipelineRun.yaml # 预期输出 pipelinerun.tekton.dev/tekton-kn-sample-b8gkt created # 查询pipeline状态 kubectl get pipelinerun # 预期输出 NAME SUCCEEDED REASON STARTTIME COMPLETIONTIME tekton-kn-sample-b8gkt True Succeeded 5m 2m方式二:如果您安装了Tekton Dashboard,可以通过白屏查看执行状态。
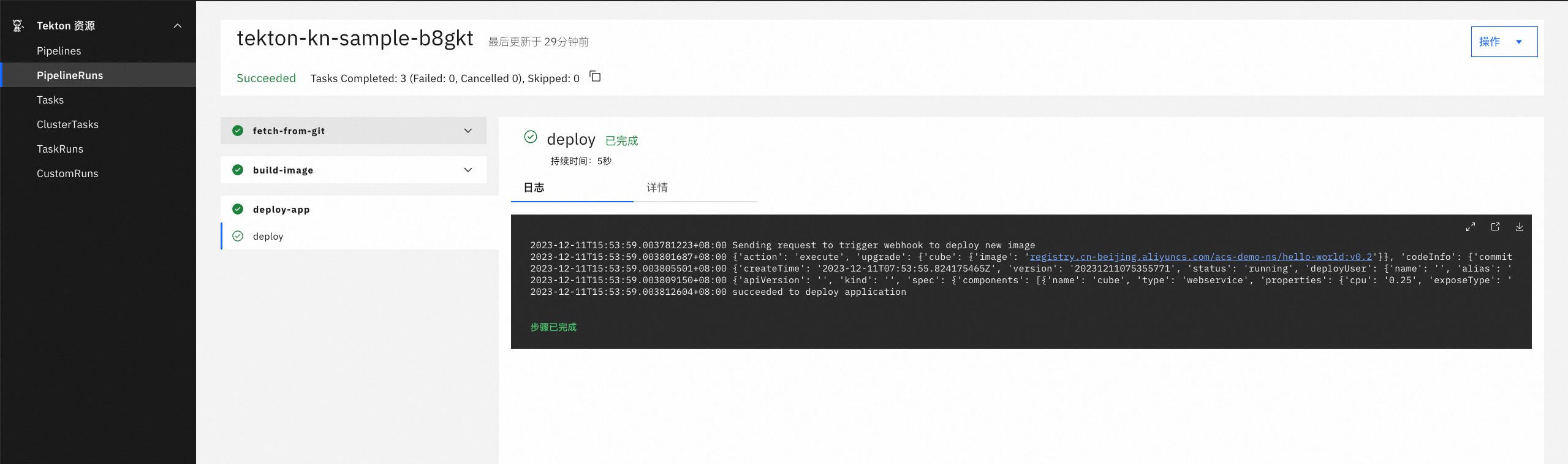
访问服务。
通过VelaUX查看应用情况。

访问服务

场景三:结合Tekton Triggers完成GitOps升级
通过上面两个步骤已经构建出一个构建和交付的基本流水线。现在通过GitOps的思路以代码变更为触发源,将其升级到自动化的持续构建和持续交付流水线。
基于Tekton Triggers子项目,可以定义一个Webhook,在代码变更时自动实例化出一个PipelineRun进行流水线执行。
Tekton Triggers中有以下几个核心对象:
TriggerTemplate:用于描述Trigger需要创建的对象模板,在本例中是一个PipelineRun。TriggerBinding:用于声明参数转换,将接收的参数转换为TriggerTemplate中声明的方式。Interceptor:对事件进行自定义处理,如需要过滤的事件类型等。EventListener:核心监听器,可以定义一个或多个Triggers对象描述并关联相应的TriggerBinding和TriggerTemplate,以及对执行器的配置进行自定义扩展。
将Pipeline变为一个基于GitOps的方式,主要进行以下几个步骤的调整:
新建EventListener等Triggers相关的CRD定义作为事件处理器。
新建一个Ingress对象,绑定至监听器的Service上,将监听器暴露出公网。
在Github仓库中配置Webhook触发,针对PUSH事件进行触发,并将CommitId等信息作为事件参数进行镜像版本和发布版本的定义。
前提条件
已安装IngressController。具体操作,请参见安装Nginx Ingress Controller。
操作步骤
安装Tekton Triggers 0.23.0版本。
使用以下内容,创建tekton-triggers.yaml。
展开查看tekton-triggers-v0.23.0.yaml
# Copyright 2019 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # http://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. kind: ClusterRole apiVersion: rbac.authorization.k8s.io/v1 metadata: name: tekton-triggers-admin labels: app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-triggers rules: - apiGroups: [""] resources: ["configmaps", "services", "events"] verbs: ["get", "list", "create", "update", "delete", "patch", "watch"] - apiGroups: ["apps"] resources: ["deployments", "deployments/finalizers"] verbs: ["get", "list", "create", "update", "delete", "patch", "watch"] - apiGroups: ["admissionregistration.k8s.io"] resources: ["mutatingwebhookconfigurations", "validatingwebhookconfigurations"] verbs: ["get", "list", "create", "update", "delete", "patch", "watch"] - apiGroups: ["triggers.tekton.dev"] resources: ["clustertriggerbindings", "clusterinterceptors", "interceptors", "eventlisteners", "triggerbindings", "triggertemplates", "triggers", "eventlisteners/finalizers"] verbs: ["get", "list", "create", "update", "delete", "patch", "watch"] - apiGroups: ["triggers.tekton.dev"] resources: ["clustertriggerbindings/status", "clusterinterceptors/status", "interceptors/status", "eventlisteners/status", "triggerbindings/status", "triggertemplates/status", "triggers/status"] verbs: ["get", "list", "create", "update", "delete", "patch", "watch"] # We uses leases for leaderelection - apiGroups: ["coordination.k8s.io"] resources: ["leases"] verbs: ["get", "list", "create", "update", "delete", "patch", "watch"] - apiGroups: ["serving.knative.dev"] resources: ["*", "*/status", "*/finalizers"] verbs: ["get", "list", "create", "update", "delete", "deletecollection", "patch", "watch"] - apiGroups: [""] resources: ["namespaces"] verbs: ["get"] # The webhook configured the namespace as the OwnerRef on various cluster-scoped resources, # which requires we can Get the system namespace. resourceNames: ["tekton-pipelines"] - apiGroups: [""] resources: ["namespaces/finalizers"] verbs: ["update"] # The webhook configured the namespace as the OwnerRef on various cluster-scoped resources, # which requires we can update the system namespace finalizers. resourceNames: ["tekton-pipelines"] --- kind: ClusterRole apiVersion: rbac.authorization.k8s.io/v1 metadata: name: tekton-triggers-core-interceptors labels: app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-triggers rules: - apiGroups: [""] resources: ["secrets"] verbs: ["get", "list", "watch"] --- kind: ClusterRole apiVersion: rbac.authorization.k8s.io/v1 metadata: name: tekton-triggers-core-interceptors-secrets labels: app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-triggers rules: - apiGroups: ["triggers.tekton.dev"] resources: ["clusterinterceptors"] verbs: ["get", "list", "watch", "update"] - apiGroups: [""] resources: ["secrets"] verbs: ["get", "list", "watch", "update"] resourceNames: ["tekton-triggers-core-interceptors-certs"] --- apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRole metadata: name: tekton-triggers-eventlistener-roles labels: app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-triggers rules: - apiGroups: ["triggers.tekton.dev"] resources: ["eventlisteners", "triggerbindings", "interceptors", "triggertemplates", "triggers"] verbs: ["get", "list", "watch"] - apiGroups: [""] resources: ["configmaps"] verbs: ["get", "list", "watch"] - apiGroups: ["tekton.dev"] resources: ["pipelineruns", "pipelineresources", "taskruns"] verbs: ["create"] - apiGroups: [""] resources: ["serviceaccounts"] verbs: ["impersonate"] - apiGroups: [""] resources: ["events"] verbs: ["create", "patch"] --- kind: ClusterRole apiVersion: rbac.authorization.k8s.io/v1 metadata: name: tekton-triggers-eventlistener-clusterroles labels: app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-triggers rules: - apiGroups: ["triggers.tekton.dev"] resources: ["clustertriggerbindings", "clusterinterceptors"] verbs: ["get", "list", "watch"] - apiGroups: [""] resources: ["secrets"] verbs: ["get", "list", "watch"] --- # Copyright 2020 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # http://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. # NOTE: when multi-tenant EventListener progresses, moving this Role # to a ClusterRole is not the advisable path. Additional Roles that # adds access to Secrets to the Namespaces managed by the multi-tenant # EventListener is what should be done. While not as simple, it avoids # giving access to K8s system level, cluster admin privileged level Secrets kind: Role apiVersion: rbac.authorization.k8s.io/v1 metadata: name: tekton-triggers-admin-webhook namespace: tekton-pipelines labels: app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-triggers rules: - apiGroups: [""] resources: ["secrets"] verbs: ["get", "list", "create", "update", "delete", "patch", "watch"] --- kind: Role apiVersion: rbac.authorization.k8s.io/v1 metadata: name: tekton-triggers-core-interceptors namespace: tekton-pipelines labels: app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-triggers rules: - apiGroups: [""] resources: ["configmaps"] verbs: ["get", "list", "watch"] --- apiVersion: rbac.authorization.k8s.io/v1 kind: Role metadata: name: tekton-triggers-info namespace: tekton-pipelines labels: app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-triggers rules: # All system:authenticated users needs to have access # of the triggers-info ConfigMap even if they don't # have access to the other resources present in the # installed namespace. - apiGroups: [""] resources: ["configmaps"] resourceNames: ["triggers-info"] verbs: ["get"] --- # Copyright 2019 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # http://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: v1 kind: ServiceAccount metadata: name: tekton-triggers-controller namespace: tekton-pipelines labels: app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-triggers --- apiVersion: v1 kind: ServiceAccount metadata: name: tekton-triggers-webhook namespace: tekton-pipelines labels: app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-triggers --- apiVersion: v1 kind: ServiceAccount metadata: name: tekton-triggers-core-interceptors namespace: tekton-pipelines labels: app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-triggers --- # Copyright 2019 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # http://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRoleBinding metadata: name: tekton-triggers-controller-admin labels: app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-triggers subjects: - kind: ServiceAccount name: tekton-triggers-controller namespace: tekton-pipelines roleRef: kind: ClusterRole name: tekton-triggers-admin apiGroup: rbac.authorization.k8s.io --- apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRoleBinding metadata: name: tekton-triggers-webhook-admin labels: app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-triggers subjects: - kind: ServiceAccount name: tekton-triggers-webhook namespace: tekton-pipelines roleRef: kind: ClusterRole name: tekton-triggers-admin apiGroup: rbac.authorization.k8s.io --- apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRoleBinding metadata: name: tekton-triggers-core-interceptors labels: app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-triggers subjects: - kind: ServiceAccount name: tekton-triggers-core-interceptors namespace: tekton-pipelines roleRef: kind: ClusterRole name: tekton-triggers-core-interceptors apiGroup: rbac.authorization.k8s.io --- apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRoleBinding metadata: name: tekton-triggers-core-interceptors-secrets labels: app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-triggers subjects: - kind: ServiceAccount name: tekton-triggers-core-interceptors namespace: tekton-pipelines roleRef: kind: ClusterRole name: tekton-triggers-core-interceptors-secrets apiGroup: rbac.authorization.k8s.io --- # Copyright 2020 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # http://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: rbac.authorization.k8s.io/v1 kind: RoleBinding metadata: name: tekton-triggers-webhook-admin namespace: tekton-pipelines labels: app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-triggers subjects: - kind: ServiceAccount name: tekton-triggers-webhook namespace: tekton-pipelines roleRef: kind: Role name: tekton-triggers-admin-webhook apiGroup: rbac.authorization.k8s.io --- apiVersion: rbac.authorization.k8s.io/v1 kind: RoleBinding metadata: name: tekton-triggers-core-interceptors namespace: tekton-pipelines labels: app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-triggers subjects: - kind: ServiceAccount name: tekton-triggers-core-interceptors namespace: tekton-pipelines roleRef: kind: Role name: tekton-triggers-core-interceptors apiGroup: rbac.authorization.k8s.io --- apiVersion: rbac.authorization.k8s.io/v1 kind: RoleBinding metadata: name: tekton-triggers-info namespace: tekton-pipelines labels: app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-triggers subjects: # Giving all system:authenticated users the access of the # ConfigMap which contains version information. - kind: Group name: system:authenticated apiGroup: rbac.authorization.k8s.io roleRef: apiGroup: rbac.authorization.k8s.io kind: Role name: tekton-triggers-info --- # Copyright 2021 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # https://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: apiextensions.k8s.io/v1 kind: CustomResourceDefinition metadata: name: clusterinterceptors.triggers.tekton.dev labels: app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-triggers triggers.tekton.dev/release: "v0.23.0" version: "v0.23.0" spec: group: triggers.tekton.dev scope: Cluster names: kind: ClusterInterceptor plural: clusterinterceptors singular: clusterinterceptor shortNames: - ci categories: - tekton - tekton-triggers versions: - name: v1alpha1 served: true storage: true schema: openAPIV3Schema: type: object # One can use x-kubernetes-preserve-unknown-fields: true # at the root of the schema (and inside any properties, additionalProperties) # to get the traditional CRD behaviour that nothing is pruned, despite # setting spec.preserveUnknownProperties: false. # # See https://kubernetes.io/blog/2019/06/20/crd-structural-schema/ # See issue: https://github.com/knative/serving/issues/912 x-kubernetes-preserve-unknown-fields: true # Opt into the status subresource so metadata.generation # starts to increment subresources: status: {} --- # Copyright 2019 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # https://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: apiextensions.k8s.io/v1 kind: CustomResourceDefinition metadata: name: clustertriggerbindings.triggers.tekton.dev labels: app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-triggers triggers.tekton.dev/release: "v0.23.0" version: "v0.23.0" spec: group: triggers.tekton.dev scope: Cluster names: kind: ClusterTriggerBinding plural: clustertriggerbindings singular: clustertriggerbinding shortNames: - ctb categories: - tekton - tekton-triggers versions: - name: v1beta1 served: true storage: true schema: openAPIV3Schema: type: object # One can use x-kubernetes-preserve-unknown-fields: true # at the root of the schema (and inside any properties, additionalProperties) # to get the traditional CRD behaviour that nothing is pruned, despite # setting spec.preserveUnknownProperties: false. # # See https://kubernetes.io/blog/2019/06/20/crd-structural-schema/ # See issue: https://github.com/knative/serving/issues/912 x-kubernetes-preserve-unknown-fields: true subresources: status: {} - name: v1alpha1 served: true storage: false schema: openAPIV3Schema: type: object # One can use x-kubernetes-preserve-unknown-fields: true # at the root of the schema (and inside any properties, additionalProperties) # to get the traditional CRD behaviour that nothing is pruned, despite # setting spec.preserveUnknownProperties: false. # # See https://kubernetes.io/blog/2019/06/20/crd-structural-schema/ # See issue: https://github.com/knative/serving/issues/912 x-kubernetes-preserve-unknown-fields: true subresources: status: {} --- # Copyright 2019 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # https://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: apiextensions.k8s.io/v1 kind: CustomResourceDefinition metadata: name: eventlisteners.triggers.tekton.dev labels: app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-triggers triggers.tekton.dev/release: "v0.23.0" version: "v0.23.0" spec: group: triggers.tekton.dev scope: Namespaced names: kind: EventListener plural: eventlisteners singular: eventlistener shortNames: - el categories: - tekton - tekton-triggers versions: - name: v1beta1 served: true storage: true # Opt into the status subresource so metadata.generation # starts to increment subresources: status: {} schema: openAPIV3Schema: type: object # One can use x-kubernetes-preserve-unknown-fields: true # at the root of the schema (and inside any properties, additionalProperties) # to get the traditional CRD behaviour that nothing is pruned, despite # setting spec.preserveUnknownProperties: false. # # See https://kubernetes.io/blog/2019/06/20/crd-structural-schema/ # See issue: https://github.com/knative/serving/issues/912 x-kubernetes-preserve-unknown-fields: true additionalPrinterColumns: - name: Address type: string jsonPath: .status.address.url - name: Available type: string jsonPath: ".status.conditions[?(@.type=='Available')].status" - name: Reason type: string jsonPath: ".status.conditions[?(@.type=='Available')].reason" - name: Ready type: string jsonPath: ".status.conditions[?(@.type=='Ready')].status" - name: Reason type: string jsonPath: ".status.conditions[?(@.type=='Ready')].reason" - name: v1alpha1 served: true storage: false schema: openAPIV3Schema: type: object # One can use x-kubernetes-preserve-unknown-fields: true # at the root of the schema (and inside any properties, additionalProperties) # to get the traditional CRD behaviour that nothing is pruned, despite # setting spec.preserveUnknownProperties: false. # # See https://kubernetes.io/blog/2019/06/20/crd-structural-schema/ # See issue: https://github.com/knative/serving/issues/912 x-kubernetes-preserve-unknown-fields: true # Opt into the status subresource so metadata.generation # starts to increment subresources: status: {} additionalPrinterColumns: - name: Address type: string jsonPath: .status.address.url - name: Available type: string jsonPath: ".status.conditions[?(@.type=='Available')].status" - name: Reason type: string jsonPath: ".status.conditions[?(@.type=='Available')].reason" - name: Ready type: string jsonPath: ".status.conditions[?(@.type=='Ready')].status" - name: Reason type: string jsonPath: ".status.conditions[?(@.type=='Ready')].reason" --- # Copyright 2022 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # https://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: apiextensions.k8s.io/v1 kind: CustomResourceDefinition metadata: name: interceptors.triggers.tekton.dev labels: app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-triggers triggers.tekton.dev/release: "v0.23.0" version: "v0.23.0" spec: group: triggers.tekton.dev scope: Namespaced names: kind: Interceptor plural: interceptors singular: interceptor shortNames: - ni categories: - tekton - tekton-triggers versions: - name: v1alpha1 served: true storage: true schema: openAPIV3Schema: type: object # One can use x-kubernetes-preserve-unknown-fields: true # at the root of the schema (and inside any properties, additionalProperties) # to get the traditional CRD behaviour that nothing is pruned, despite # setting spec.preserveUnknownProperties: false. # # See https://kubernetes.io/blog/2019/06/20/crd-structural-schema/ # See issue: https://github.com/knative/serving/issues/912 x-kubernetes-preserve-unknown-fields: true # Opt into the status subresource so metadata.generation # starts to increment subresources: status: {} --- # Copyright 2019 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # https://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: apiextensions.k8s.io/v1 kind: CustomResourceDefinition metadata: name: triggers.triggers.tekton.dev labels: app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-triggers triggers.tekton.dev/release: "v0.23.0" version: "v0.23.0" spec: group: triggers.tekton.dev scope: Namespaced names: kind: Trigger plural: triggers singular: trigger shortNames: - tri categories: - tekton - tekton-triggers versions: - name: v1beta1 served: true storage: true schema: openAPIV3Schema: type: object # One can use x-kubernetes-preserve-unknown-fields: true # at the root of the schema (and inside any properties, additionalProperties) # to get the traditional CRD behaviour that nothing is pruned, despite # setting spec.preserveUnknownProperties: false. # # See https://kubernetes.io/blog/2019/06/20/crd-structural-schema/ # See issue: https://github.com/knative/serving/issues/912 x-kubernetes-preserve-unknown-fields: true subresources: status: {} - name: v1alpha1 served: true storage: false schema: openAPIV3Schema: type: object # One can use x-kubernetes-preserve-unknown-fields: true # at the root of the schema (and inside any properties, additionalProperties) # to get the traditional CRD behaviour that nothing is pruned, despite # setting spec.preserveUnknownProperties: false. # # See https://kubernetes.io/blog/2019/06/20/crd-structural-schema/ # See issue: https://github.com/knative/serving/issues/912 x-kubernetes-preserve-unknown-fields: true # Opt into the status subresource so metadata.generation # starts to increment subresources: status: {} --- # Copyright 2019 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # https://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: apiextensions.k8s.io/v1 kind: CustomResourceDefinition metadata: name: triggerbindings.triggers.tekton.dev labels: app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-triggers triggers.tekton.dev/release: "v0.23.0" version: "v0.23.0" spec: group: triggers.tekton.dev scope: Namespaced names: kind: TriggerBinding plural: triggerbindings singular: triggerbinding shortNames: - tb categories: - tekton - tekton-triggers versions: - name: v1beta1 served: true storage: true schema: openAPIV3Schema: type: object # One can use x-kubernetes-preserve-unknown-fields: true # at the root of the schema (and inside any properties, additionalProperties) # to get the traditional CRD behaviour that nothing is pruned, despite # setting spec.preserveUnknownProperties: false. # # See https://kubernetes.io/blog/2019/06/20/crd-structural-schema/ # See issue: https://github.com/knative/serving/issues/912 x-kubernetes-preserve-unknown-fields: true # Opt into the status subresource so metadata.generation # starts to increment subresources: status: {} - name: v1alpha1 served: true storage: false schema: openAPIV3Schema: type: object # One can use x-kubernetes-preserve-unknown-fields: true # at the root of the schema (and inside any properties, additionalProperties) # to get the traditional CRD behaviour that nothing is pruned, despite # setting spec.preserveUnknownProperties: false. # # See https://kubernetes.io/blog/2019/06/20/crd-structural-schema/ # See issue: https://github.com/knative/serving/issues/912 x-kubernetes-preserve-unknown-fields: true # Opt into the status subresource so metadata.generation # starts to increment subresources: status: {} --- # Copyright 2019 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # https://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: apiextensions.k8s.io/v1 kind: CustomResourceDefinition metadata: name: triggertemplates.triggers.tekton.dev labels: app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-triggers triggers.tekton.dev/release: "v0.23.0" version: "v0.23.0" spec: group: triggers.tekton.dev scope: Namespaced names: kind: TriggerTemplate plural: triggertemplates singular: triggertemplate shortNames: - tt categories: - tekton - tekton-triggers versions: - name: v1beta1 served: true storage: true schema: openAPIV3Schema: type: object # One can use x-kubernetes-preserve-unknown-fields: true # at the root of the schema (and inside any properties, additionalProperties) # to get the traditional CRD behaviour that nothing is pruned, despite # setting spec.preserveUnknownProperties: false. # # See https://kubernetes.io/blog/2019/06/20/crd-structural-schema/ # See issue: https://github.com/knative/serving/issues/912 x-kubernetes-preserve-unknown-fields: true # Opt into the status subresource so metadata.generation # starts to increment subresources: status: {} - name: v1alpha1 served: true storage: false schema: openAPIV3Schema: type: object # One can use x-kubernetes-preserve-unknown-fields: true # at the root of the schema (and inside any properties, additionalProperties) # to get the traditional CRD behaviour that nothing is pruned, despite # setting spec.preserveUnknownProperties: false. # # See https://kubernetes.io/blog/2019/06/20/crd-structural-schema/ # See issue: https://github.com/knative/serving/issues/912 x-kubernetes-preserve-unknown-fields: true # Opt into the status subresource so metadata.generation # starts to increment subresources: status: {} --- # Copyright 2020 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # https://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: v1 kind: Secret metadata: name: triggers-webhook-certs namespace: tekton-pipelines labels: app.kubernetes.io/component: webhook app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-triggers triggers.tekton.dev/release: "v0.23.0" # The data is populated at install time. --- apiVersion: admissionregistration.k8s.io/v1 kind: ValidatingWebhookConfiguration metadata: name: validation.webhook.triggers.tekton.dev labels: app.kubernetes.io/component: webhook app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-triggers triggers.tekton.dev/release: "v0.23.0" webhooks: - admissionReviewVersions: - v1 clientConfig: service: name: tekton-triggers-webhook namespace: tekton-pipelines failurePolicy: Fail sideEffects: None name: validation.webhook.triggers.tekton.dev --- apiVersion: admissionregistration.k8s.io/v1 kind: MutatingWebhookConfiguration metadata: name: webhook.triggers.tekton.dev labels: app.kubernetes.io/component: webhook app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-triggers triggers.tekton.dev/release: "v0.23.0" webhooks: - admissionReviewVersions: - v1 clientConfig: service: name: tekton-triggers-webhook namespace: tekton-pipelines failurePolicy: Fail sideEffects: None name: webhook.triggers.tekton.dev --- apiVersion: admissionregistration.k8s.io/v1 kind: ValidatingWebhookConfiguration metadata: name: config.webhook.triggers.tekton.dev labels: app.kubernetes.io/component: webhook app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-triggers triggers.tekton.dev/release: "v0.23.0" webhooks: - admissionReviewVersions: - v1 clientConfig: service: name: tekton-triggers-webhook namespace: tekton-pipelines failurePolicy: Fail sideEffects: None name: config.webhook.triggers.tekton.dev namespaceSelector: matchExpressions: - key: triggers.tekton.dev/release operator: Exists --- # Copyright 2019 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # http://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRole metadata: name: tekton-triggers-aggregate-edit labels: app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-triggers rbac.authorization.k8s.io/aggregate-to-edit: "true" rbac.authorization.k8s.io/aggregate-to-admin: "true" rules: - apiGroups: - triggers.tekton.dev resources: - clustertriggerbindings - clusterinterceptors - eventlisteners - interceptors - triggers - triggerbindings - triggertemplates verbs: - create - delete - deletecollection - get - list - patch - update - watch --- # Copyright 2019 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # http://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRole metadata: name: tekton-triggers-aggregate-view labels: app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-triggers rbac.authorization.k8s.io/aggregate-to-view: "true" rules: - apiGroups: - triggers.tekton.dev resources: - clustertriggerbindings - clusterinterceptors - eventlisteners - interceptors - triggers - triggerbindings - triggertemplates verbs: - get - list - watch --- # Copyright 2021 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # https://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: v1 kind: ConfigMap metadata: name: config-defaults-triggers namespace: tekton-pipelines labels: app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-triggers data: _example: | ################################ # # # EXAMPLE CONFIGURATION # # # ################################ # This block is not actually functional configuration, # but serves to illustrate the available configuration # options and document them in a way that is accessible # to users that `kubectl edit` this config map. # # These sample configuration options may be copied out of # this example block and unindented to be in the data block # to actually change the configuration. # default-service-account contains the default service account name # to use for TaskRun and PipelineRun, if none is specified. default-service-account: "default" --- # Copyright 2021 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # https://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: v1 kind: ConfigMap metadata: name: feature-flags-triggers namespace: tekton-pipelines labels: app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-pipelines data: # Setting this flag will determine which gated features are enabled. # Acceptable values are "stable" or "alpha". enable-api-fields: "alpha" # Setting this field with valid regex pattern matching the pattern will exclude labels from # getting added to resources created by the EventListener such as the deployment labels-exclusion-pattern: "" --- # Copyright 2021 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # https://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: v1 kind: ConfigMap metadata: name: triggers-info namespace: tekton-pipelines labels: app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-triggers data: # Contains triggers version which can be queried by external # tools such as CLI. Elevated permissions are already given to # this ConfigMap such that even if we don't have access to # other resources in the namespace we still can have access to # this ConfigMap. version: "v0.23.0" --- # Copyright 2019 Tekton Authors LLC # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # https://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: v1 kind: ConfigMap metadata: name: config-logging-triggers namespace: tekton-pipelines labels: app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-triggers data: # Common configuration for all knative codebase zap-logger-config: | { "level": "info", "development": false, "disableStacktrace": true, "sampling": { "initial": 100, "thereafter": 100 }, "outputPaths": ["stdout"], "errorOutputPaths": ["stderr"], "encoding": "json", "encoderConfig": { "timeKey": "timestamp", "levelKey": "severity", "nameKey": "logger", "callerKey": "caller", "messageKey": "message", "stacktraceKey": "stacktrace", "lineEnding": "", "levelEncoder": "", "timeEncoder": "iso8601", "durationEncoder": "", "callerEncoder": "" } } # Log level overrides loglevel.controller: "info" loglevel.webhook: "info" loglevel.eventlistener: "info" --- # Copyright 2019 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # https://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: v1 kind: ConfigMap metadata: name: config-observability-triggers namespace: tekton-pipelines labels: app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-triggers data: _example: | ################################ # # # EXAMPLE CONFIGURATION # # # ################################ # This block is not actually functional configuration, # but serves to illustrate the available configuration # options and document them in a way that is accessible # to users that `kubectl edit` this config map. # # These sample configuration options may be copied out of # this example block and unindented to be in the data block # to actually change the configuration. # metrics.backend-destination field specifies the system metrics destination. # It supports either prometheus (the default) or stackdriver. # Note: Using stackdriver will incur additional charges metrics.backend-destination: prometheus # metrics.stackdriver-project-id field specifies the stackdriver project ID. This # field is optional. When running on GCE, application default credentials will be # used if this field is not provided. metrics.stackdriver-project-id: "<your stackdriver project id>" # metrics.allow-stackdriver-custom-metrics indicates whether it is allowed to send metrics to # Stackdriver using "global" resource type and custom metric type if the # metrics are not supported by "knative_revision" resource type. Setting this # flag to "true" could cause extra Stackdriver charge. # If metrics.backend-destination is not Stackdriver, this is ignored. metrics.allow-stackdriver-custom-metrics: "false" --- # Copyright 2019 Tekton Authors LLC # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # https://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: v1 kind: Service metadata: labels: app.kubernetes.io/name: controller app.kubernetes.io/component: controller app.kubernetes.io/instance: default app.kubernetes.io/version: "v0.23.0" app.kubernetes.io/part-of: tekton-triggers triggers.tekton.dev/release: "v0.23.0" app: tekton-triggers-controller version: "v0.23.0" name: tekton-triggers-controller namespace: tekton-pipelines spec: ports: - name: http-metrics port: 9000 protocol: TCP targetPort: 9000 selector: app.kubernetes.io/name: controller app.kubernetes.io/component: controller app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-triggers --- # Copyright 2019 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # http://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: apps/v1 kind: Deployment metadata: name: tekton-triggers-controller namespace: tekton-pipelines labels: app.kubernetes.io/name: controller app.kubernetes.io/component: controller app.kubernetes.io/instance: default app.kubernetes.io/version: "v0.23.0" app.kubernetes.io/part-of: tekton-triggers # tekton.dev/release value replaced with inputs.params.versionTag in triggers/tekton/publish.yaml triggers.tekton.dev/release: "v0.23.0" spec: replicas: 1 selector: matchLabels: app.kubernetes.io/name: controller app.kubernetes.io/component: controller app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-triggers template: metadata: labels: app.kubernetes.io/name: controller app.kubernetes.io/component: controller app.kubernetes.io/instance: default app.kubernetes.io/version: "v0.23.0" app.kubernetes.io/part-of: tekton-triggers app: tekton-triggers-controller triggers.tekton.dev/release: "v0.23.0" # version value replaced with inputs.params.versionTag in triggers/tekton/publish.yaml version: "v0.23.0" spec: serviceAccountName: tekton-triggers-controller containers: - name: tekton-triggers-controller image: "registry.cn-hangzhou.aliyuncs.com/acs-demo-ns/tekton-triggers-controller:v0.23.0" args: ["-logtostderr", "-stderrthreshold", "INFO", "-el-image", "registry.cn-hangzhou.aliyuncs.com/acs-demo-ns/tekton-triggers-eventlistenersink:v0.23.0", "-el-port", "8080", "-el-security-context=true", "-el-events", "disable", "-el-readtimeout", "5", "-el-writetimeout", "40", "-el-idletimeout", "120", "-el-timeouthandler", "30", "-el-httpclient-readtimeout", "30", "-el-httpclient-keep-alive", "30", "-el-httpclient-tlshandshaketimeout", "10", "-el-httpclient-responseheadertimeout", "10", "-el-httpclient-expectcontinuetimeout", "1", "-period-seconds", "10", "-failure-threshold", "1"] env: - name: SYSTEM_NAMESPACE valueFrom: fieldRef: fieldPath: metadata.namespace - name: CONFIG_LOGGING_NAME value: config-logging-triggers - name: CONFIG_OBSERVABILITY_NAME value: config-observability-triggers - name: CONFIG_DEFAULTS_NAME value: config-defaults-triggers - name: METRICS_DOMAIN value: tekton.dev/triggers - name: METRICS_PROMETHEUS_PORT value: "9000" securityContext: allowPrivilegeEscalation: false capabilities: drop: - "ALL" # User 65532 is the distroless nonroot user ID runAsUser: 65532 runAsGroup: 65532 runAsNonRoot: true seccompProfile: type: RuntimeDefault --- # Copyright 2019 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # http://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: v1 kind: Service metadata: name: tekton-triggers-webhook namespace: tekton-pipelines labels: app.kubernetes.io/name: webhook app.kubernetes.io/component: webhook app.kubernetes.io/instance: default app.kubernetes.io/version: "v0.23.0" app.kubernetes.io/part-of: tekton-triggers app: tekton-triggers-webhook version: "v0.23.0" triggers.tekton.dev/release: "v0.23.0" spec: ports: - name: https-webhook port: 443 targetPort: 8443 selector: app.kubernetes.io/name: webhook app.kubernetes.io/component: webhook app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-triggers --- # Copyright 2019 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # https://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: apps/v1 kind: Deployment metadata: name: tekton-triggers-webhook namespace: tekton-pipelines labels: app.kubernetes.io/name: webhook app.kubernetes.io/component: webhook app.kubernetes.io/instance: default app.kubernetes.io/version: "v0.23.0" app.kubernetes.io/part-of: tekton-triggers # tekton.dev/release value replaced with inputs.params.versionTag in triggers/tekton/publish.yaml triggers.tekton.dev/release: "v0.23.0" spec: replicas: 1 selector: matchLabels: app.kubernetes.io/name: webhook app.kubernetes.io/component: webhook app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-triggers template: metadata: labels: app.kubernetes.io/name: webhook app.kubernetes.io/component: webhook app.kubernetes.io/instance: default app.kubernetes.io/version: "v0.23.0" app.kubernetes.io/part-of: tekton-triggers app: tekton-triggers-webhook triggers.tekton.dev/release: "v0.23.0" # version value replaced with inputs.params.versionTag in triggers/tekton/publish.yaml version: "v0.23.0" spec: serviceAccountName: tekton-triggers-webhook containers: - name: webhook # This is the Go import path for the binary that is containerized # and substituted here. image: "registry.cn-hangzhou.aliyuncs.com/acs-demo-ns/tekton-triggers-webhook:v0.23.0" env: - name: SYSTEM_NAMESPACE valueFrom: fieldRef: fieldPath: metadata.namespace - name: CONFIG_LOGGING_NAME value: config-logging-triggers - name: WEBHOOK_SERVICE_NAME value: tekton-triggers-webhook - name: WEBHOOK_SECRET_NAME value: triggers-webhook-certs - name: METRICS_DOMAIN value: tekton.dev/triggers ports: - name: metrics containerPort: 9000 - name: profiling containerPort: 8008 - name: https-webhook containerPort: 8443 securityContext: allowPrivilegeEscalation: false # User 65532 is the distroless nonroot user ID runAsUser: 65532 runAsGroup: 65532 runAsNonRoot: true capabilities: drop: - "ALL" seccompProfile: type: RuntimeDefault --- # Copyright 2022 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # https://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: v1 kind: Secret metadata: name: tekton-triggers-core-interceptors-certs namespace: tekton-pipelines labels: app.kubernetes.io/name: core-interceptors app.kubernetes.io/component: interceptors app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-triggers triggers.tekton.dev/release: "v0.23.0" # The data is populated at install time. --- # Copyright 2020 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # http://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: apps/v1 kind: Deployment metadata: name: tekton-triggers-core-interceptors namespace: tekton-pipelines labels: app.kubernetes.io/name: core-interceptors app.kubernetes.io/component: interceptors app.kubernetes.io/instance: default app.kubernetes.io/version: "v0.23.0" app.kubernetes.io/part-of: tekton-triggers # tekton.dev/release value replaced with inputs.params.versionTag in triggers/tekton/publish.yaml triggers.tekton.dev/release: "v0.23.0" spec: replicas: 1 selector: matchLabels: app.kubernetes.io/name: core-interceptors app.kubernetes.io/component: interceptors app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-triggers template: metadata: labels: app.kubernetes.io/name: core-interceptors app.kubernetes.io/component: interceptors app.kubernetes.io/instance: default app.kubernetes.io/version: "v0.23.0" app.kubernetes.io/part-of: tekton-triggers app: tekton-triggers-core-interceptors triggers.tekton.dev/release: "v0.23.0" # version value replaced with inputs.params.versionTag in triggers/tekton/publish.yaml version: "v0.23.0" spec: serviceAccountName: tekton-triggers-core-interceptors containers: - name: tekton-triggers-core-interceptors image: "registry.cn-hangzhou.aliyuncs.com/acs-demo-ns/tekton-triggers-interceptors:v0.23.0" ports: - containerPort: 8443 args: ["-logtostderr", "-stderrthreshold", "INFO"] env: - name: SYSTEM_NAMESPACE valueFrom: fieldRef: fieldPath: metadata.namespace - name: CONFIG_LOGGING_NAME value: config-logging-triggers - name: CONFIG_OBSERVABILITY_NAME value: config-observability-triggers - name: METRICS_DOMAIN value: tekton.dev/triggers # assuming service and deployment names are same always for consistency - name: INTERCEPTOR_TLS_SVC_NAME value: tekton-triggers-core-interceptors - name: INTERCEPTOR_TLS_SECRET_NAME value: tekton-triggers-core-interceptors-certs readinessProbe: httpGet: path: /ready port: 8443 scheme: HTTPS initialDelaySeconds: 5 periodSeconds: 10 timeoutSeconds: 5 securityContext: allowPrivilegeEscalation: false # User 65532 is the distroless nonroot user ID runAsUser: 65532 runAsGroup: 65532 runAsNonRoot: true capabilities: drop: - "ALL" seccompProfile: type: RuntimeDefault --- apiVersion: v1 kind: Service metadata: labels: app.kubernetes.io/name: tekton-triggers-core-interceptors app.kubernetes.io/component: interceptors app.kubernetes.io/instance: default app.kubernetes.io/version: "v0.23.0" app.kubernetes.io/part-of: tekton-triggers triggers.tekton.dev/release: "v0.23.0" app: tekton-triggers-core-interceptors version: "v0.23.0" name: tekton-triggers-core-interceptors namespace: tekton-pipelines spec: ports: - name: "https" port: 8443 selector: app.kubernetes.io/name: core-interceptors app.kubernetes.io/component: interceptors app.kubernetes.io/instance: default app.kubernetes.io/part-of: tekton-triggers --- # Copyright 2021 The Tekton Authors # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # http://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: triggers.tekton.dev/v1alpha1 kind: ClusterInterceptor metadata: name: cel labels: server/type: https spec: clientConfig: service: name: tekton-triggers-core-interceptors namespace: tekton-pipelines path: "cel" port: 8443 --- apiVersion: triggers.tekton.dev/v1alpha1 kind: ClusterInterceptor metadata: name: bitbucket labels: server/type: https spec: clientConfig: service: name: tekton-triggers-core-interceptors namespace: tekton-pipelines path: "bitbucket" port: 8443 --- apiVersion: triggers.tekton.dev/v1alpha1 kind: ClusterInterceptor metadata: name: github labels: server/type: https spec: clientConfig: service: name: tekton-triggers-core-interceptors namespace: tekton-pipelines path: "github" port: 8443 --- apiVersion: triggers.tekton.dev/v1alpha1 kind: ClusterInterceptor metadata: name: gitlab labels: server/type: https spec: clientConfig: service: name: tekton-triggers-core-interceptors namespace: tekton-pipelines path: "gitlab" port: 8443 ---通过kubctl执行以下命令,安装Tekton Triggers。
kubectl apply -f tekton-triggers-v0.23.0.yaml执行以下命令,查看Tekton Triggers的安装状态。
kubectl get deploy -n tekton-pipelines预期输出:
NAME READY UP-TO-DATE AVAILABLE AGE tekton-dashboard 1/1 1 1 13d tekton-pipelines-controller 1/1 1 1 25d tekton-pipelines-webhook 1/1 1 1 25d tekton-triggers-controller 1/1 1 1 2m2s tekton-triggers-core-interceptors 1/1 1 1 2m2s tekton-triggers-webhook 1/1 1 1 2m2s当所有控制器启动完成后,说明已经安装完成。
声明必要的RBAC资源。
说明本示例声明一个名为github-triggers-secret的Secret,作为后续和GitHub Webhook交互的公钥使用。
展开查看YAML
--- apiVersion: v1 kind: Secret metadata: name: github-triggers-secret type: Opaque stringData: secretToken: "ace-tekton-demo" --- apiVersion: v1 kind: ServiceAccount metadata: name: tekton-triggers-github-sa secrets: - name: github-triggers-secret --- apiVersion: rbac.authorization.k8s.io/v1 kind: Role metadata: name: tekton-triggers-github-minimal rules: # EventListeners need to be able to fetch all namespaced resources - apiGroups: ["triggers.tekton.dev"] resources: ["eventlisteners", "triggerbindings", "triggertemplates", "triggers"] verbs: ["get", "list", "watch"] - apiGroups: [""] # configmaps is needed for updating logging config resources: ["configmaps"] verbs: ["get", "list", "watch"] # Permissions to create resources in associated TriggerTemplates - apiGroups: ["tekton.dev"] resources: ["pipelineruns", "pipelineresources", "taskruns"] verbs: ["create"] - apiGroups: [""] resources: ["serviceaccounts"] verbs: ["impersonate"] - apiGroups: ["policy"] resources: ["podsecuritypolicies"] resourceNames: ["tekton-triggers"] verbs: ["use"] --- apiVersion: rbac.authorization.k8s.io/v1 kind: RoleBinding metadata: name: tekton-triggers-github-binding subjects: - kind: ServiceAccount name: tekton-triggers-github-sa roleRef: apiGroup: rbac.authorization.k8s.io kind: Role name: tekton-triggers-github-minimal --- kind: ClusterRole apiVersion: rbac.authorization.k8s.io/v1 metadata: name: tekton-triggers-github-clusterrole rules: # EventListeners need to be able to fetch any clustertriggerbindings - apiGroups: ["triggers.tekton.dev"] resources: ["clustertriggerbindings", "clusterinterceptors","interceptors"] verbs: ["get", "list", "watch"] --- apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRoleBinding metadata: name: tekton-triggers-github-clusterbinding subjects: - kind: ServiceAccount name: tekton-triggers-github-sa namespace: default roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: tekton-triggers-github-clusterrole ---定义Triggers相关资源。
因为需要处理GitHub的PUSH事件,并且由GitHub发起一次请求调用,您可以通过GitHub先查看请求的详细描述。本示例需要关注
head_commit.id和repository.clone_url两个属性,作为构建镜像的入参使用。声明TriggerBinding对象。
apiVersion: triggers.tekton.dev/v1beta1 kind: TriggerBinding metadata: name: github-push-binding spec: params: - name: gitrevision value: $(body.head_commit.id) - name: gitrepositoryurl value: $(body.repository.clone_url)声明TriggerTemplate接收参数和PipelineRun定义。
在Template中使用步骤二的PipelineRun作为资源模板,对其中的两个参数进行替换,改为由TriggerBinding传入。
展开查看TriggerTemplate YAML
apiVersion: triggers.tekton.dev/v1beta1 kind: TriggerTemplate metadata: name: github-template spec: params: #接收参数 - name: gitrevision - name: gitrepositoryurl resourceTemplates: - apiVersion: tekton.dev/v1 kind: PipelineRun metadata: generateName: tekton-sample- spec: pipelineRef: name: "demo.pipeline" taskRunTemplate: serviceAccountName: 'pipeline-account' workspaces: - name: git-source volumeClaimTemplate: metadata: annotations: csi.alibabacloud.com/mountpoint: "your-nas-endpoint" spec: accessModes: - ReadWriteMany storageClassName: alibaba-cloud-nas resources: requests: storage: 30Gi - name: docker-regcred secret: defaultMode: 420 items: - key: .dockerconfigjson path: config.json secretName: docker-regcred params: - name: repo_url value: $(tt.params.gitrepositoryurl) # 引用参数,作为PipelineRun的参数定义 - name: repo_revision value: $(tt.params.gitrevision) # 引用参数,作为PipelineRun的参数定义 - name: image-registry value: registry.cn-beijing.aliyuncs.com/acs-demo-ns - name: image-repo-name value: hello-world - name: trigger_token value: your-velaux-token - name: velaux_url value: your-velaux-url - name: velaux_token value: your-velaux-token - name: app_name value: cube - name: app_namespace value: default声明EventListener完成整体Trigger定义。
内置在EventListener中定义过滤器使用全局Interceptor并过滤PUSH事件。
通过resources属性进行资源协议扩展,使用任务型实例作为执行器。
展开查看EventListener YAML
apiVersion: triggers.tekton.dev/v1beta1 kind: EventListener metadata: name: github-listener spec: triggers: - name: github-listener interceptors: - ref: name: "github" params: - name: "secretRef" value: secretName: github-triggers-secret secretKey: secretToken - name: "eventTypes" value: ["push"] bindings: - ref: github-push-binding template: ref: github-template resources: kubernetesResource: spec: template: metadata: labels: alibabacloud.com/compute-qos: "best-effort" spec: serviceAccountName: tekton-triggers-github-sa
创建Ingress对象将监听器透出公网,可被GitHub Webhook访问。
在前提条件里已经安装了Ingress Controller,因此创建Ingress对象后会通过集群的公网SLB对外透出访问端口。
apiVersion: networking.k8s.io/v1 kind: Ingress metadata: labels: ingress-controller: nginx name: tekton-triggers namespace: default spec: ingressClassName: nginx rules: - http: paths: - backend: service: name: el-github-listener port: number: 8080 path: /github pathType: Exact执行以下命令,查看创建情况。
kubectl get ingress NAME CLASS HOSTS ADDRESS PORTS AGE tekton-triggers nginx * 39.105.xxx.xxx 80 1m执行以下命令,发起测试请求。
triggers curl -i 39.105.xxx.xxx:80/github HTTP/1.1 400 Bad Request Date: Tue, 19 Dec 2023 10:50:24 GMT Content-Type: application/json Content-Length: 154 Connection: keep-alive {"eventListener":"github-listener","namespace":"default","eventListenerUID":"","errorMessage":"Invalid event body format : unexpected end of JSON input"}
配置GitHub Webhook。
Secret中填写定义的一个公钥名称acs-tekton-demo。您可以根据情况进行调整。

进行一次代码提交,并推送至main分支。
您可以通过命令行或者Codespaces进行一次代码提交,此时会自动创建出一个PipelineRun进行流水线执行。
tkn pr list NAME STARTED DURATION STATUS tekton-sample-5xmxg 2 hours ago 4m7s Succeeded tkn pr describe tekton-sample-5xmxg Name: tekton-sample-5xmxg Namespace: default Pipeline Ref: demo.pipeline Service Account: pipeline-account Labels: tekton.dev/pipeline=demo.pipeline triggers.tekton.dev/eventlistener=github-listener triggers.tekton.dev/trigger=github-listener triggers.tekton.dev/triggers-eventid=6a65d322-c244-4477-ba4b-47b6e7490d26 Status STARTED DURATION STATUS 2 hours ago 4m7s Succeeded Timeouts Pipeline: 1h0m0s Params NAME VALUE ∙ repo_url https://gitee.com/AliyunContainerService/tekton-demo.git ∙ repo_revision 562ccaa1ebc27873ce7cd9f9be070807195c9e9e ∙ image-registry registry.cn-beijing.aliyuncs.com/acs-demo-ns ∙ image-repo-name hello-world ∙ trigger_token ... ∙ velaux_url ... ∙ velaux_token ... ∙ app_name cube ∙ app_namespace default Workspaces NAME SUB PATH WORKSPACE BINDING ∙ git-source --- VolumeClaimTemplate ∙ docker-regcred --- Secret (secret=docker-regcred,item=.dockerconfigjson=config.json) Taskruns NAME TASK NAME STARTED DURATION STATUS ∙ tekton-sample-5xmxg-deploy-app deploy-app 2 hours ago 45s Succeeded ∙ tekton-sample-5xmxg-build-image build-image 2 hours ago 2m2s Succeeded ∙ tekton-sample-5xmxg-fetch-from-git fetch-from-git 2 hours ago 37s Succeeded您也可以通过控制台进行查看。

场景四:Tekton Triggers结合SonarQube在闲时进行代码质量扫描
SonarQube是一款开源的代码质量管理系统,提供丰富的多语言支持。结合Tekton Triggers提供的EventListener机制,您可以在业务闲时复用算力资源对公司或者个人的代码仓库进行质量扫描,也可以通过Tekton集成Trivy进行全量镜像安全扫描等。
操作步骤
定义SonarQube任务和流水线。
我们的Pipeline由两个任务组成,分别是git-clone进行代码下载和sonarqube-scanner进行代码质量扫描
定义SonarQube Task。
此处引用官方仓库中的SonarQube定义。更多信息,请参见SonarQube Task。
展开查看SonarQube Task YAML
apiVersion: tekton.dev/v1beta1 kind: Task metadata: name: sonarqube-scanner labels: app.kubernetes.io/version: "0.4" annotations: tekton.dev/pipelines.minVersion: "0.17.0" tekton.dev/categories: Security tekton.dev/tags: security tekton.dev/displayName: "sonarqube scanner" tekton.dev/platforms: "linux/amd64" spec: description: >- The following task can be used to perform static analysis on the source code provided the SonarQube server is hosted SonarQube is the leading tool for continuously inspecting the Code Quality and Security of your codebases, all while empowering development teams. Analyze over 25 popular programming languages including C#, VB.Net, JavaScript, TypeScript and C++. It detects bugs, vulnerabilities and code smells across project branches and pull requests. workspaces: - name: source description: "Workspace containing the code which needs to be scanned by SonarQube" - name: sonar-settings description: "Optional workspace where SonarQube properties can be mounted" optional: true - name: sonar-credentials description: | A workspace containing a login or password for use within sonarqube. optional: true params: - name: SONAR_HOST_URL description: SonarQube server URL default: "" - name: SONAR_PROJECT_KEY description: Project's unique key default: "" - name: PROJECT_VERSION description: "Version of the project. Default: 1.0" default: "1.0" - name: SOURCE_TO_SCAN description: "Comma-separated paths to directories containing main source files" default: "." - name: SONAR_ORGANIZATION description: "The organization in sonarqube where the project exists" default: "" - name: SONAR_SCANNER_IMAGE description: "The sonarqube scanner CLI image which will run the scan" default: "docker.io/sonarsource/sonar-scanner-cli:4.6@sha256:7a976330a8bad1beca6584c1c118e946e7a25fdc5b664d5c0a869a6577d81b4f" - name: SONAR_LOGIN_KEY description: Name of the file of the login within the sonarqube credentials workspace default: "login" - name: SONAR_PASSWORD_KEY description: Name of the file of the password within the sonarqube credentials workspace default: "password" steps: - name: sonar-properties-create image: registry.access.redhat.com/ubi8/ubi-minimal:8.2 workingDir: $(workspaces.source.path) env: - name: SONAR_HOST_URL value: $(params.SONAR_HOST_URL) - name: SONAR_PROJECT_KEY value: $(params.SONAR_PROJECT_KEY) - name: PROJECT_VERSION value: $(params.PROJECT_VERSION) - name: SOURCE_TO_SCAN value: $(params.SOURCE_TO_SCAN) - name: SONAR_ORGANIZATION value: $(params.SONAR_ORGANIZATION) script: | #!/usr/bin/env bash replaceValues() { filename=$1 thekey=$2 newvalue=$3 if ! grep -R "^[#]*\s*${thekey}=.*" $filename >/dev/null; then echo "APPENDING because '${thekey}' not found" echo "" >>$filename echo "$thekey=$newvalue" >>$filename else echo "SETTING because '${thekey}' found already" sed -ir "s|^[#]*\s*${thekey}=.*|$thekey=$newvalue|" $filename fi } if [[ "$(workspaces.sonar-settings.bound)" == "true" ]]; then if [[ -f $(workspaces.sonar-settings.path)/sonar-project.properties ]]; then echo "using user provided sonar-project.properties file" cp -RL $(workspaces.sonar-settings.path)/sonar-project.properties $(workspaces.source.path)/sonar-project.properties fi fi if [[ -f $(workspaces.source.path)/sonar-project.properties ]]; then if [[ -n "${SONAR_HOST_URL}" ]]; then echo "replacing sonar host URL" replaceValues $(workspaces.source.path)/sonar-project.properties sonar.host.url "${SONAR_HOST_URL}" fi if [[ -n "${SONAR_PROJECT_KEY}" ]]; then echo "replacing sonar project key" replaceValues $(workspaces.source.path)/sonar-project.properties sonar.projectKey "${SONAR_PROJECT_KEY}" fi echo "Values in sonar-project.properties file replaced successfully..." else echo "Creating sonar-project.properties file..." touch sonar-project.properties [[ -n "${SONAR_PROJECT_KEY}" ]] && { echo "sonar.projectKey=${SONAR_PROJECT_KEY}" >> sonar-project.properties } || { echo "missing property SONAR_PROJECT_KEY" exit 1 } [[ -n "${SONAR_HOST_URL}" ]] && { echo "sonar.host.url=${SONAR_HOST_URL}" >> sonar-project.properties } || { echo "missing property SONAR_HOST_URL" exit 1 } [[ -n "${PROJECT_VERSION}" ]] && { echo "sonar.projectVersion=${PROJECT_VERSION}" >> sonar-project.properties } || { echo "missing property PROJECT_VERSION" exit 1 } [[ -n "${SONAR_ORGANIZATION}" ]] && { echo "sonar.organization=${SONAR_ORGANIZATION}" >> sonar-project.properties } || { echo "missing property SONAR_ORGANIZATION" exit 1 } echo "sonar.sources=${SOURCE_TO_SCAN}" >> sonar-project.properties echo "---------------------------" cat $(workspaces.source.path)/sonar-project.properties fi if [[ "$(workspaces.sonar-credentials.bound)" == "true" ]]; then if [[ -f $(workspaces.sonar-credentials.path)/$(params.SONAR_PASSWORD_KEY) ]]; then SONAR_PASSWORD=`cat $(workspaces.sonar-credentials.path)/$(params.SONAR_PASSWORD_KEY)` replaceValues $(workspaces.source.path)/sonar-project.properties sonar.password "${SONAR_PASSWORD}" fi if [[ -f $(workspaces.sonar-credentials.path)/$(params.SONAR_LOGIN_KEY) ]]; then SONAR_LOGIN=`cat $(workspaces.sonar-credentials.path)/$(params.SONAR_LOGIN_KEY)` replaceValues $(workspaces.source.path)/sonar-project.properties sonar.login "${SONAR_LOGIN}" fi fi - name: sonar-scan image: $(params.SONAR_SCANNER_IMAGE) workingDir: $(workspaces.source.path) command: - sonar-scanner定义Pipeline。
展开查看Pipeline YAML
apiVersion: tekton.dev/v1beta1 kind: Pipeline metadata: name: sonarqube-pipeline spec: params: - name: repo_url type: string - name: deleteExisting type: string - name: SONAR_PROJECT_KEY type: string - name: SONAR_HOST_URL type: string - name: PROJECT_VERSION type: string - name: SONAR_ORGANIZATION type: string workspaces: - name: shared-workspace tasks: - name: fetch-repository taskRef: name: git-clone workspaces: - name: output workspace: shared-workspace params: - name: repo_url value: $(params.repo_url) - name: deleteExisting value: $(params.deleteExisting) - name: code-analysis taskRef: name: sonarqube-scanner params: - name: SONAR_PROJECT_KEY value: $(params.SONAR_PROJECT_KEY) - name: SONAR_HOST_URL value: $(params.SONAR_HOST_URL) - name: PROJECT_VERSION value: $(params.PROJECT_VERSION) - name: SONAR_ORGANIZATION value: $(params.SONAR_ORGANIZATION) runAfter: - fetch-repository workspaces: - name: source workspace: shared-workspace定义EventListener监听器。
和上述场景一样,通过volumeClaimTemplate声明静态NAS作为代码数据的共享存储。SonarQube采用Sonarcloud的公共项目。
展开查看EventListener YAML
--- apiVersion: triggers.tekton.dev/v1beta1 kind: EventListener metadata: name: cron-listener spec: serviceAccountName: tekton-triggers-github-sa triggers: - name: github-listener bindings: - ref: cron-sonar-binding template: ref: cron-sonar-template resources: kubernetesResource: spec: template: metadata: labels: alibabacloud.com/compute-qos: "best-effort" spec: serviceAccountName: tekton-triggers-github-sa --- apiVersion: triggers.tekton.dev/v1beta1 kind: TriggerBinding metadata: name: cron-sonar-binding spec: params: - name: gitrevision value: main --- apiVersion: triggers.tekton.dev/v1beta1 kind: TriggerTemplate metadata: name: cron-sonar-template spec: resourceTemplates: - apiVersion: tekton.dev/v1beta1 kind: PipelineRun metadata: generateName: sonarqube-run- spec: pipelineRef: name: sonarqube-pipeline taskRunSpecs: - pipelineTaskName: code-analysis computeResources: requests: cpu: 500m memory: 2Gi workspaces: - name: shared-workspace volumeClaimTemplate: metadata: annotations: csi.alibabacloud.com/mountpoint: "your-nas-endpoint" spec: accessModes: - ReadWriteMany storageClassName: alicloud-nas resources: requests: storage: 30Gi params: - name: repo_url value: "https://github.com/vinamra28/sonartest.git" - name: deleteExisting value: "true" - name: SONAR_PROJECT_KEY value: sonarqube-scanner - name: SONAR_HOST_URL value: https://sonarcloud.io/ - name: PROJECT_VERSION value: "1.0" - name: SONAR_ORGANIZATION value: tekton-catalog-test
定义CronJob作为EventListener的触发器入口。
定义一个每天凌晨的CronJob来模拟闲时进行任务触发,通过CURL命令请求EventListener暴露的Service域名。
执行以下命令,将EventListener、Pipeline和Task等资源提交至集群中。
kubectl apply -f resource.yaml,eventlistener.yaml预期输出:
task.tekton.dev/sonarqube-scanner configured pipeline.tekton.dev/sonarqube-pipeline configured eventlistener.triggers.tekton.dev/cron-listener configured triggerbinding.triggers.tekton.dev/cron-sonar-binding unchanged triggertemplate.triggers.tekton.dev/cron-sonar-template configured执行以下命令,查看EventListener自动创建的Service。
kubectl get service -l eventlistener=cron-listener预期输出:
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE el-cron-listener ClusterIP 192.168.152.155 <none> 8080/TCP,9000/TCP 1m对应的其集群内服务域名是
el-cron-listener.default.svc.cluster.local,可以作为请求的入口地址。使用以下内容创建CronJob,定义Job进行EventListener触发。
apiVersion: batch/v1 kind: CronJob metadata: name: hello spec: schedule: "05 00 * * *" jobTemplate: metadata: labels: alibabacloud.com/compute-qos: "best-effort" spec: template: spec: containers: - name: hello image: curlimages/curl args: ["curl", "-X", "POST", "--data", "{}", "el-cron-listener.default.svc.cluster.local:8080"] restartPolicy: Never
执行以下命令,查看流水线执行情况。
tkn pr describe sonarqube-run-z4pb4预期输出:
Name: sonarqube-run-z4pb4 Namespace: default Pipeline Ref: sonarqube-pipeline Service Account: default Labels: tekton.dev/pipeline=sonarqube-pipeline triggers.tekton.dev/eventlistener=cron-listener triggers.tekton.dev/trigger=github-listener triggers.tekton.dev/triggers-eventid=4b2ac0fd-82af-48fb-a8bf-9318250c658e Status STARTED DURATION STATUS 20 hours ago 11m0s Succeeded Timeouts Pipeline: 1h0m0s Params NAME VALUE ∙ repo_url https://github.com/vinamra28/sonartest.git ∙ repo_revision master ∙ deleteExisting true ∙ SONAR_PROJECT_KEY sonarqube-scanner ∙ SONAR_HOST_URL https://sonarcloud.io/ ∙ PROJECT_VERSION 1.0 ∙ SONAR_ORGANIZATION tekton-catalog-test Workspaces NAME SUB PATH WORKSPACE BINDING ∙ shared-workspace --- VolumeClaimTemplate Taskruns NAME TASK NAME STARTED DURATION STATUS ∙ sonarqube-run-z4pb4-code-analysis code-analysis 20 hours ago 10m16s Succeeded ∙ sonarqube-run-z4pb4-fetch-repository fetch-repository 20 hours ago 44s Succeeded通过Tekton Dashboard查看执行情况。

在SonarQube的管理控制台中查看扫描结果。
任务执行完成后,在日志中也会提示任务的链接信息,可以通过链接查看扫描结果。
INFO: ANALYSIS SUCCESSFUL, you can find the results at: https://sonarcloud.io/dashboard?id=sonarqube-scanner INFO: Note that you will be able to access the updated dashboard once the server has processed the submitted analysis report INFO: More about the report processing at https://sonarcloud.io/api/ce/task?id=AYyL3cZOCNsYyHKt_KWe WARN: Failed to prepare write of the sensor cache INFO: Analysis total time: 9:10.390 s INFO: ------------------------------------------------------------------------ INFO: EXECUTION SUCCESS INFO: ------------------------------------------------------------------------ INFO: Total time: 9:32.762s INFO: Final Memory: 16M/63M INFO: ------------------------------------------------------------------------